Welcome back, my aspiring cyberwarriors!
In this continuing series on Linux Basics for Hackers, I now want to address Loadable Kernel Modules (LKMs). LKM’s are critical to the Linux administrator as they provide them the capability to add functionality to the kernel without having to recompile the kernel. Things like video and other device drivers can be added to the Linux kernel without shutting down the system, recompiling, and rebooting.

Loadable kernel modules are critical to the hacker because if we can get the Linux admin to load our new module to their kernel, we not only own their system–but because we are at the kernel level of their operating system,–we can control even what their system is reporting to them in terms of processes, ports, services, hard drive space, etc.
So, if we can offer the Linux user/admin a “new and improved” video driver with our rootkit embedded in it, we can take control of his system and kernel. This is the way some of the most insidious rootkits take advantage of the Linux OS.
So, I hope it’s clear that understanding LKMs is key to being an effective Linux admin and being a VERY effective and stealthy hacker.
Step 1: What Is a Kernel Module?
The kernel is a core component of any Linux operating system, including our Kali Linux. The kernel is the central nervous system of our operating system, controlling everything an operating system does, including managing the interactions between the hardware components and starting the necessary services. The kernel operates between user applications and the hardware such as the CPU, memory, the hard drive, etc.
As the kernel manages all that is taking place with the operating system, sometimes it needs updates. These updates might include new device drivers (such as video card or USB devices), file system drivers, and even system extensions. This is where LKMs come in. We can now simply load and unload kernel modules as we need them without recompiling the kernel.
Step 2: Checking the Kernel
The first thing we want to do is check to see what kernel our system is running. There are at least two ways to do this. We can enter:
kali > uname -a
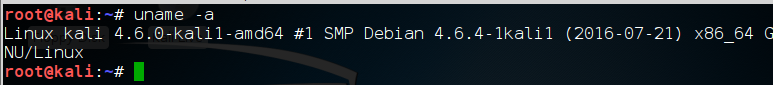
Note that the kernel tells us its kernel build (4.6.4), but also the architecture it is built for (x86_64). We can also get this info by “catting” the /proc/version file, which actually gives up even more info.
kali > cat /proc/version
Step 3: Kernel Tuning with sysctl
Sometimes, a Linux admin will want to “tune” the kernel. This might include changing memory allocations, enabling networking feature, and even hardening the kernel from hackers.
With modern Linux kernels, we have the sysctl command to tune kernel options. All changes you make with the sysctl remain in effect only until you reboot the system. To make any changes permanent, the configuration file for sysctl must be edited at /etc/sysctl.conf.
Be careful in using sysctl because without the proper knowledge and experience, you can easily make your system unbootable and unusable. Let’s take a look at the contents of sysctl now.
kali > sysctl -a | less
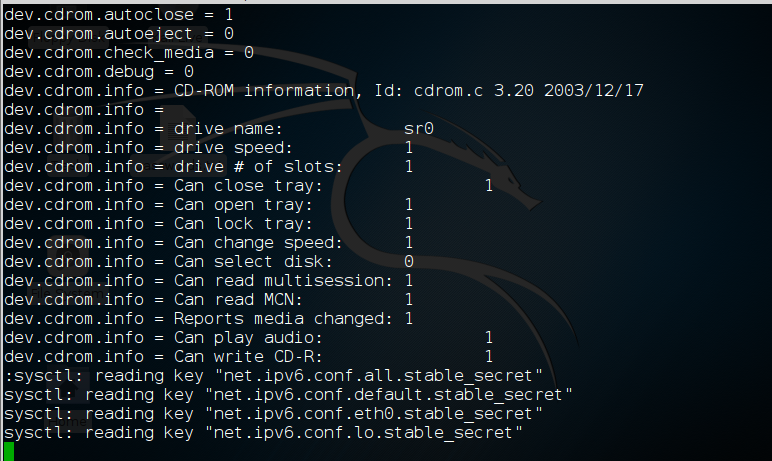
To view the configuration file for sysctl, we can get it at /etc/sysctl.conf.
kali > less /etc/sysctl.conf
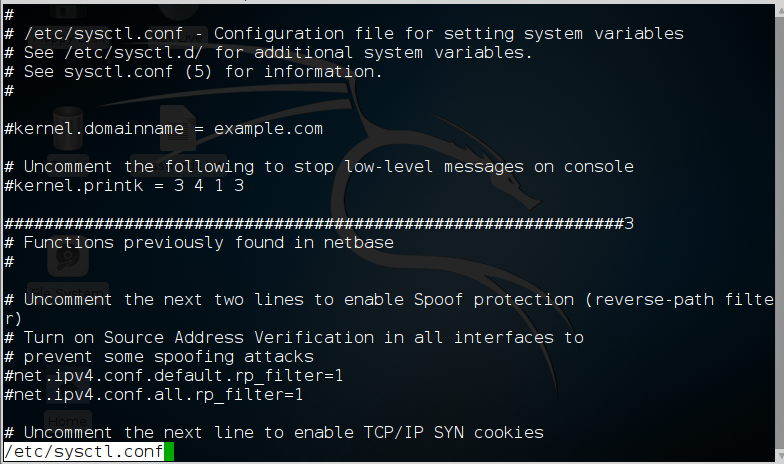
One of the ways we may want to use sysctl for hacking is to enable ipforwarding (net.ipv4.conf.default.forwarding) for man-in-the-middle attacks. From a hardening perspective, we can disable ICMP echo requests (net.ipv4.icmp_echo_ignore_all) so as to make more difficult–but not impossible–for hackers to find our system.
Step 4: Kernel Modules
To manage our kernels, Linux has at least two ways to do it. The older way is to use a group of commands built around the insmod command. Here we use one of those—lsmod—to list the installed modules in kernel.
kali > lsmod
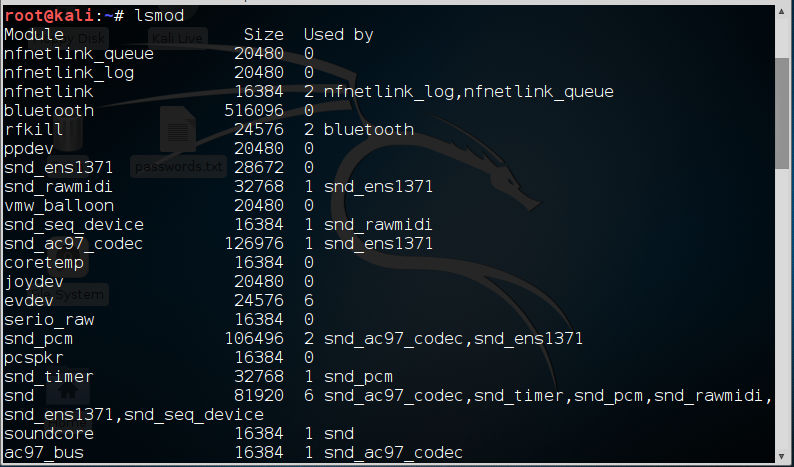
We can load or insert a module with insmod and remove a module with rmmod.
Step 5: Modprobe
Most newer distributions of Linux, including our Kali Linux (built on Debian), have converted to the modprobe command for LKM management. To add a module to our kernel, we can type:
kali > modprobe -a <module name>
To remove a module, we simply use the -r switch with modprobe followed by the name of the module.
kali > modprobe -r <module to be removed>
A major advantage of modprobe is that understands dependencies, options, and installation and removal procedures for our kernel modules.
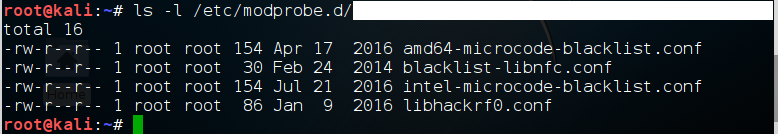
To see configuration files for the installed modules, we list the contents of the /etc/modprobe.d/ directory.
kali> ls -l /etc/modprobe.d/
Remember, the LKM modules are a convenience to a Linux user/admin, but are a major security weakness of Linux and one the professional hacker should be familiar with. As I said before, the LKM can be the perfect vehicle to get your rootkit into the kernel and wreak havoc!
For more on using Linux for hacking, check out my book “Linux Basics for Hackers” now available here on Amazon.