Welcome back, my aspiring Wi-Fi Hackers!
In previous tutorials here at Hackers-Arise, we have demonstrated how to hack Wi-Fi (IEEE 802.11) access points using multiple techniques, including;
4. PMKID Attack
5. Continuous Denial of Service (DoS) Attack
6. Evading Wi-Fi Authentication
7. Using wifiphisher to Social Engineer a Wi-Fi Password
In this tutorial, we will be examining the Wi-Fi (802.11) protocol anatomy. It’s great to know how to use the tools at our disposal to hack Wi-Fi, but if you want to develop your own tools, you will need to dig deeper into the Wi-Fi protocol in order to better understand it.
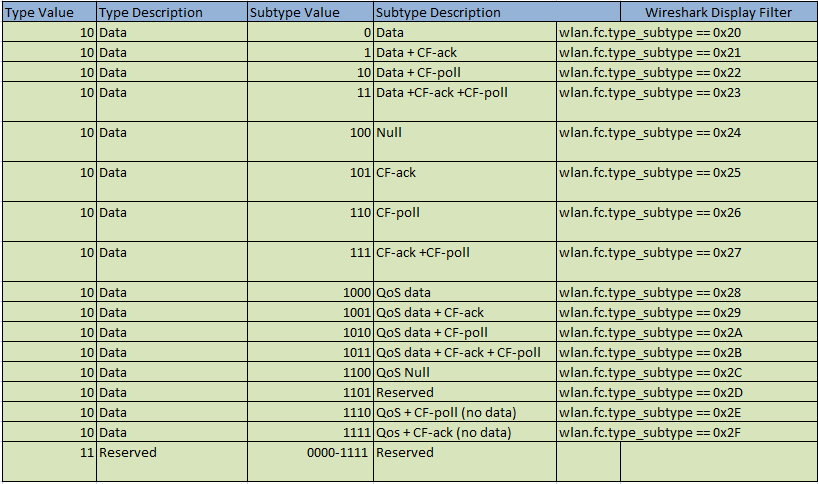
The tables below enumerate each of the Wi-Fi frame types, their description, and how you can filter for each type using Wireshark.


A Bit of Background of these Different Frame Types
The tables above are a great reference, but let’s take a moment to review what each of those frames do including their specific Wireshark filter (in italics beneath each description). It’s important to note that tools such as airodump-ng and Kismet are capable of using these frames to provide you with key information necessary for hacking the AP.
1. An Association request is sent by a station to associate to a BSS.
wlan.fc.type==0x00
2. An Association response is sent in response to an association request
wlan.fc.type==0x01
3. A Reassociation request is sent by a station changing association to another AP in the same ESS (so roaming between APs, or reassociating with the same AP)
wlan.fc.type==0x02
4. Reassociation response is the response to the reassociation request
wlan.fc.type==0x03
5. Probe request is sent by a station in order to “scan” for an SSID (this is how airodump-ng and other tools find the AP even if the SSID is turned off).
wlan.fc.type==0x04
6. Probe response is sent by each BSS participating to that SSID
wlan.fc.type==0x05
7. Beacon is a periodic frame sent by the AP (or stations in case of IBSS) and giving information about the BSS
wlan.fc.type==0x08
8. ATIM is the traffic indication map for IBSS (in a BSS, the TIM is included in the beacon)
wlan.fc.type==0x09
9. Disassociation is sent to terminate the association of a station
wlan.fc.type==0x0A
10. Authentication is the frame used to perform the 802.11 authentication (and not any other type of authentication)
wlan.fc.type==0x0B
11. Deauthentication is the frame terminating the authentication of a station. This frame is often used in our attack tools to “bump” users off the AP using aireplay-ng or perform a Denial of Service on the AP.
wlan.fc.type==0x0C
12. Action is a frame meant for sending information elements to other stations (when sending in a beacon is not possible/best)
wlan.fc.type==0x0D
13. PS-Poll is the Power-save poll frame polling for buffered frames after a wake-up from a station
wlan.fc.type==0x1A
14. RTS is the request-to-send frame
wlan.fc.type==0x1B
15. CTS is the clear-to-send frame (often response to RTS)
wlan.fc.type==0x1C
16. ACK is the acknowledge frame sent to confirm receipt of a frame.
wlan.fc.type==0x1D
17. Data frame is the basic frame containing data
wlan.fc.type==0x20
18. Null frame is a frame meant to contain no data but flag information
wlan.fc.type==0x24
19. QoS (Quality of Service) data is the QoS version of the data frame
wlan.fc.type==0x28
20. QoS (Quality of Service) null is the QoS version of the null frame
wlan.fc.type==0x2C
Wireshark Display Filters for Wi-Fi Frames
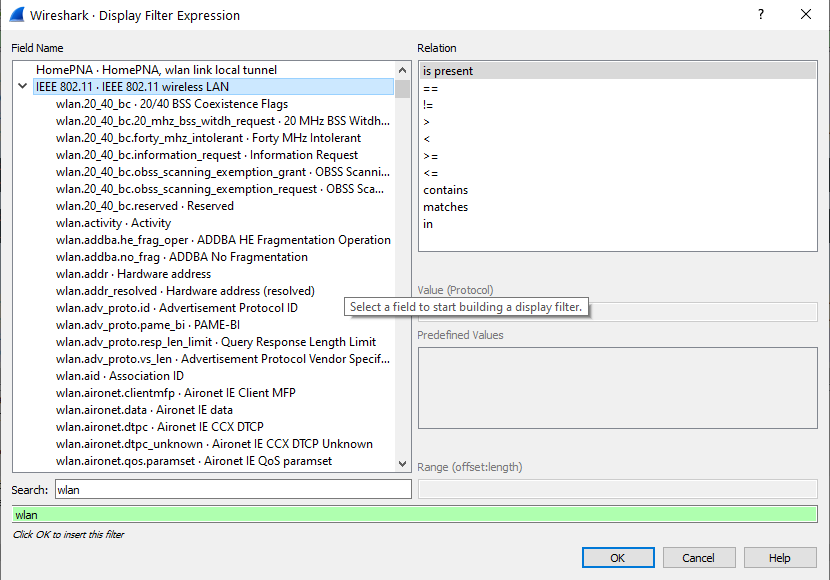
To filter for these frames in Wireshark, click on the “Expressions” tab to the right of the filter window and the following Window will open.
In the Search field near the bottom right, enter “wlan” as seen below.
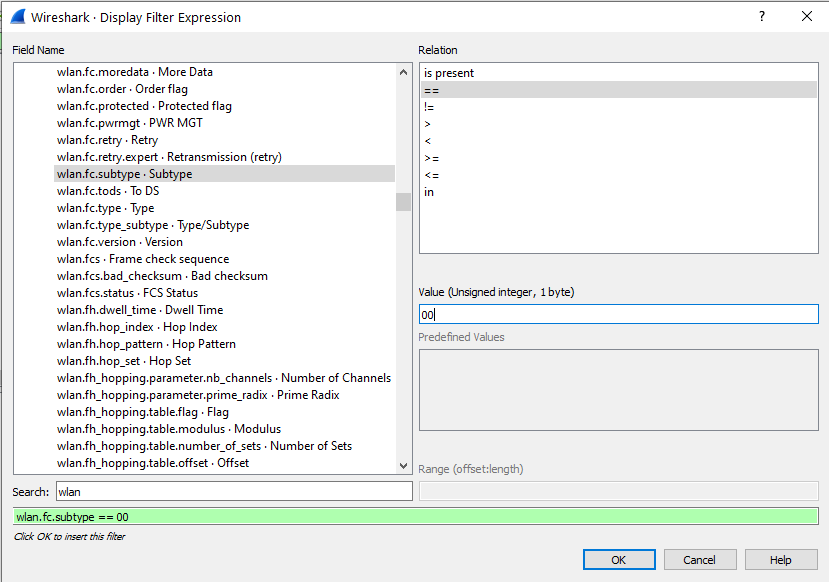
Now, scroll down to the “wlan.fc.subtype” field and click on it. Select the “==” for relation and then enter the value of the frame type you want to filter for.
Summary
When trying to develop your own Wi-Fi hacking tools, it is critical to understand the frames and their purpose in this 802.11 protocol. Bookmark this page for future reference as we use this information to develop our very own Wi-Fi hacking tools!





