As an outside attacker/pentester, we often have to deal with security devices that may interfere with our unfettered access to the network and its hosts by our scanning tools. At the least, we should expect firewalls and IDS’s to attempt to block or alert on our scanning activity. Although this might not be disastrous initially, if we succeed in compromising the network or system, an IDS may log our IP address leaving a trail back to us for the forensic investigator to pinpoint.
In this tutorial, we look at various ways we evade detection by firewalls and IDS’s when we are scanning with nmap. Note that the concepts here are not unique to nmap, but the specific techniques are.
I. Ping Suppression
It is common for network engineers and security administrators to block ICMP (echo request, echo reply) at the firewall or router. They do this to keep outside attackers from being able to find active hosts on their network using the ubiquitous ping.
When we send out a scan with nmap, it will first send out an ICMP to port 80 to check to see if the host exists and is up. If it doesn’t receive a response, it doesn’t waste resources sending packets to a host that is presumably down. As a result, it will report back that the host is down without doing anything further.
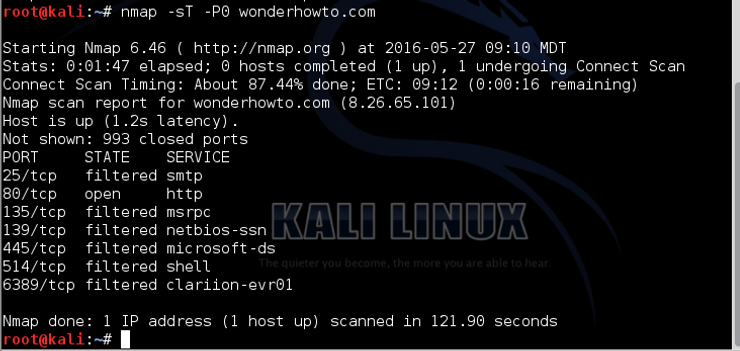
The simplest way around this is to suppress the ping. We can do this with any nmap scan by using the -P0 switch. So, to scan our favorite target website, wonderhowto.com, without sending the default ICMP to port 80, we could write;
kali > nmap -sT -P0 wonderhowto.com
II. Fooling the Firewall into Believing that the Packet is Part of an Established Connection
Once a TCP three-way handshake has taken place (SYN, SYN-ACK, ACK), every packet sent subsequently in the communication will have the ACK bit set. If a packet appears on the wire at the firewall with the ACK flag set, it would be reasonable for the firewall to assume that the packet is part of an established communication between the client and server and, thereby, let it pass.
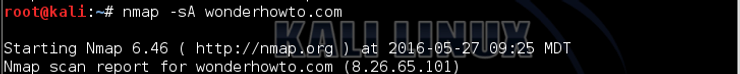
Some older firewalls, without state tables, will allow such packets to proceed into the network. We can simulate this established connection by using an ACK scan, like below.
kali > nmap -sA wonderhowto.com
III. Fragmentation
In 1998, a paper was published titled “Insertion, Evasion, and Denial of Service: Eluding Network Intrusion Detection” by Ptacek and Newsham. In this paper, the authors proposed multiple methods of evading IDS’s including fragmentation. Soon thereafter, Dug Sung of the University of Michigan , developed the fragroute tool that proved that IDS’s were susceptible to fragmentation attacks, that is, an attack that is broken into numerous pieces. The pieces are then reassembled at the destination and the attack malware is complete. Since IDS’s rely on signatures–very similar to AV software– the pieces would not match the signature the IDS is looking for. This would allow the pieces to traverse the network where they would be reassembled at the destination machine and do their dirty work.
We can do the something similar with nmap using the -f switch.
kali > nmap -sT -f wonderhowto.com
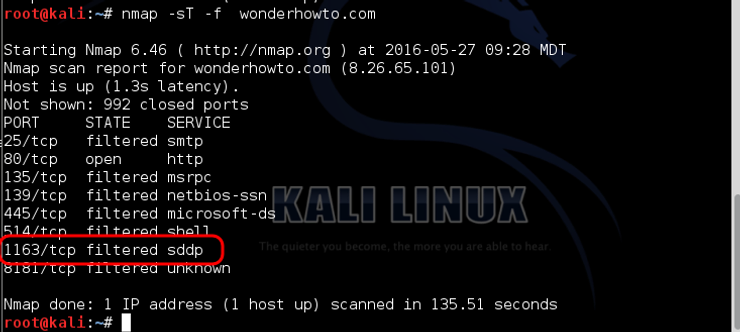
nmap will break the IP header into many small pieces to evade the IDS. As you can imagine, as we are splitting the packet into many smaller pieces, this scan can take quite a bit longer. nmap can also break the packets into increasingly smaller fragments by using the -f switch.
Note that when we fragmented the packets we were able to discover another port open at our target, 1163.
IV. Decoys
Although not strictly an evasion technique, nmap enables us to send decoys at the target to attempt to obscure the source of the scan. In other words, we still will need to send packets from our IP address (otherwise we wouldn’t get any return traffic, defeating the entire purpose of the scan), but we can spoof other IP addresses while scanning so that it appears that the scan is coming from addresses other than ours, in addition to ours. This might make it more difficult for the security device to automatically block our IP and more difficult for a forensic investigation to finger our IP as the responsible party.
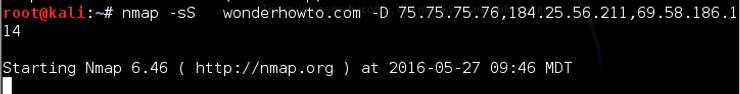
We can use the decoy feature by using the -D switch followed by a comma-delimited list of IP decoy addresses.
kali > nmap -sS wonderhowto.com -D 75.75.75.76,184.25.56.211,69.58.186.114
V. Using Proxies
Like any attack, we can use proxies between ourselves and the target system. By using proxies, the IP address of the proxies is recorded at the target, rather than our own. In this way, it makes it VERY difficult for even the most experienced forensic investigator to trace the source of the scan, much less the attack. We simply need to add the –proxies switch followed by a comma delimited list of HTTP or SOCKS4 proxies such as below. The format should be;
<protocol://IP:port>
We could then do this scan through proxies by using the following command.
kali > nmap -sS –proxies socks4://176.57.216.214:80,http://213.85.92.10:80 wonderhowto.com
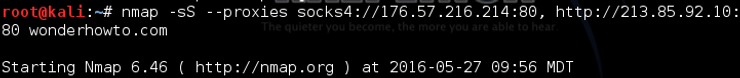
In this scan, the packets will appear to be coming from the proxy IP addresses.
VI. Timing Features
Most IDS’s only alert on scans when a threshold level of scans takes place. For instance, Snort–the world’s most widely used IDS and now part of the networking giant, Cisco–the default setting only alerts on scans when 15 or more ports are scanned per second. If we can slow down the speed of our scan, it can go right past the IDS without alerting the administrator.
nmap has a feature called scan_delay. It allows us to set the minimum amount of time between each probe that nmap sends to the host.
nmap’s scan_delay feature requires not only a numerical value, but also the units. These units are;
ms for milliseconds
s for seconds
m for minutes
h for hour
So, if we wanted nmap to delay 5 seconds between each probe we could write;
kali > nmap -sS –scan_delay 5s wonderhowto.com
Besides simply dictating the delay between scans with the –scan-delay option, nmap has six (6) built in timing or speed options. These can be designated with the -T switch followed by the numeric value or the name. Normal or -T3 is the default value. For instance, if we wanted to scan with the slowest option called “paranoid”, we could write;
kali > nmap -sS -T0 wonderhowto.com
In addition, we good use the timing word, such as paranoid in the command below.
kali > nmap -sS -T paranoid wonderhowto.com
The timing or speed options are listed below. “Insane” will complete the scan VERY quickly, but will likely to set off alarm bells and “paranoid” is VERY stealthy, but VERY, VERY slow. Be patient as a scan set at this level may take you hours, but you can be sure you won’t trigger any alarms.
paranoid (0) a serial scan with a 300 second wait
sneaky (1) a serial scan with a 15 second wait
polite (2) a serial scan 0.4 second wait
normal (3) a parallel scan
aggressive (4) a parallel 1.25sec/probe
insane (5) a parallel scan and 0.3 sec/probe
VII. Changing the Data length
Some firewalls and IDS’s have signatures of nmap scans based upon the length of the packet. These signatures include the default data length of nmaps scanning packets. These packets are generally very small (TCP scan is 40 bytes and an ICMP scan is just 28 bytes). If we can change the length of these packets, we can at least get past this signature component and may be able to get past the IDS to the network.
Nmap has a switch to set the data length of the scanning packets. By choosing a data length other than the default, nmap will pad the packet so that it doesn’t look like a typical scanning packet and hopefully, more like a legitimate packet.
We can use this feature such as this;
kali > nmap -sS –data-length 1200 wonderhowto.com
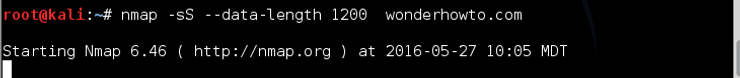
Note that payloads larger than 1400 bytes are NOT allowed.
VII. Best Practice
To make certain that your scan are not detected, you may want to use several of these techniques combined. For instance, you may want to slow the scan to T1, fragment the packets (-f), lengthen the packet to 1200 bytes, use proxies, such as this;
kali > nmap -sS -T1 -f –data-length 1200 –proxies sock4://176.57.216.214:80,http://213.85.92.10:80 wonderhowto.com
Scans, such as this, will be very slow, but nearly undetectable.




