This section will be dedicated to training you on Metasploit. Metasploit is THE most popular hacking framework in the world and it is FREE. Although it does have its shortcomings, every aspiring hacker should understand how to use Metasploit.
Below, I have begun with some Metasploit Basics and more will be coming soon.
Metasploit, The Basics
I. Introduction
Metasploit is the world’s leading exploitation framework. Originally developed by HD Moore as an open source project, it is now owned by the security company, Rapid7, which also owns the vulnerability scanner, Nexpose. Although originally developed as an open source project, Rapid7 has now developed a Pro version of Metasploit with a few more “bells and whistles”. Fortunately, the open source, community edition is still available to the rest of us without tens of thousands of dollars to spend on the Pro version (if you are a professional pentester, the efficiency and time savings accrued in using the Pro version make it a good investment).
Metasploit has multiple interfaces including;
(1) msfconsole – an interactive command line like interface
(2) msfcli – a literal Linux command line interface
(3) Armitage – a GUI based third party application
(4) msfweb – browser based interface
Undoubtedly, the most common way to use Metasploit is through Metasploit’s own interactive shell, msfconsole. In this course, we will be largely using this msfconsole, but I will show you how to use the others in a later tutorial.
In recent years, Metasploit has integrated additional tools to make it more than just a exploitation framework. Tools, such as nmap and Nexpose, are now integrated into Metasploit, so that the entire process of port scanning and vulnerability scanning can all be done from one single tool. In addition, Metasploit has now integrated a postgresql database to store the data collected from your scans and exploits.
II. Getting Started
Before we start Metasploit, we should start the postgresql database. Metasploit will work without postgresql, but this database enables Metasploit to run faster searches and store the information you collect while scanning and exploiting. Start the postgresql database by typing;
kali > service postgresql start
Once the database has been started, you can type to start the Metasploit Framework console;
kali >msfconsole
As Metasploit loads everything into RAM, it takes awhile, so be patient. Eventually, you should get a screen that looks like this.
Don’t worry if it doesn’t look exactly the same as my screen as Metasploit rotates the images. As long as you have the msf > prompt, you are in the right place.
This starts the Metasploit console. If you are more GUI oriented, you can go
Applications–>Kali Linux–>Exploitation Tools–> Metasploit–>metasploit community/pro
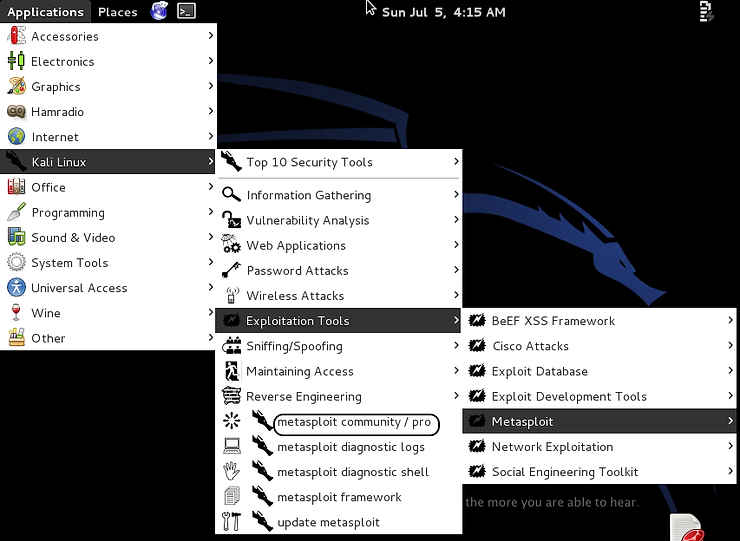
Make certain you choose the community edition. You can get the Pro edition, but it is free trial that expires quickly.
III. Metasploit Keywords
Although Metasploit is a very powerful exploitation framework, just a few keywords can get you started to hacking just about any system. A word about terminology though before we start. In Metasploit terminology, an exploit is a module that takes advantage of a system or application vulnerability. It usually will attempt to place a payload on the system. This payload can be a simple command shell or the all powerful Meterpreter. In other environments these payloads might be termed listeners or rootkits.
Let’s take a look at some of those keywords.
msf > help
Note that we can access this help menu with the “?” as well as “help”.
msf > use
The “use” command loads a module. So,for instance, if I wanted to load the exploit/windows/browser/adobe_flash_avm2 module, I would type;
As you can see, when Metasploit successfully loads the module, it responds with the type of module (exploit) and the abbreviated module name in red.
msf> show
After you load a module, the show command can be very useful to gather more information on the module. The three I use most often are show options, show payloads and show targets.
msf > show payloads
This command, when used after selecting your exploit, will show you all the payloads that will work with this exploit. If you run this command before selecting an exploit, it will show you ALL payloads.
As you see in the screenshot above, the show payloads command listed all the payloads that will work with this exploit.
msf > show options
This command is also very useful in running an exploit. It will display all of the options that need to set before running the module.
msf > show targets
A less commonly used command is show targets. Each exploit has a list of the targets it will work against. By using the “show targets” command, we can get a list of them.
msf > info
The info command is simple. When you type it after you have selected a module, it shows you key info about the module including the options that need to be set. I usually always run it after selecting my exploit.
msf > search
As a newcomer to Metasploit, the “search” command might be the most useful. When Metasploit was small and new, it was relatively easy to find the module you needed. Now with nearly 3000 modules, finding just the right module can be time-consuming and problematic. Rapid7 added the search function starting with version 4 and it has become a time and life saver.
Although you can use the search function to search for keywords, that approach is not always efficient. The primary methods by which you will search Metasploit are;
platform – the is the operating system that the module is built for
type – this is the type of module. These include exploits, nops, payloads, post and auxiliary
The syntax for using search is the keyword followed by a colon such as type:exploits
For instance, if you were looking for an exploit (type) for Windows (platform) for Abobe Flash we could type;
msf > search type:exploits platform:windows flash
msf > set
This command is use to set options within the module you selected. For instance, if we look above at the show options command, we can see numerous options that must set such as URIPATH, SVRHOST and SVRPORT. We can set any of these with the set command such as;
msf > set SRVPORT 80
msf > unset
This command, as you might expect, unsets the option that was previously set. Such as;
msf > unset SRVPORT
As you can see, we first set the SRVPORT variable to 80 and then unset it. It then reverted back to the default value of 8080 that we can see when we typed show options again.
msf > exploit
Once we have loaded our exploit and set all the necessary options, the final thing we do is “exploit”. This sends the exploit to the target system and if successful, installs the payload.
As you can see in this screenshot, the exploit starts and is running as background job with a reverse handler on port 4444. It then started a webserver on host 0.0.0.0 on port 8080 with a randomized URL (SLoJ05mneYHz5). We could have chosen a specific URL and set it.
msf > back
We can use the back command to take us “back” one step in our process. So, if you instance, we decided that we did not want to use the adobe/flash/avm2 exploit, we could type “back” and it would remove the loaded exploit.
msf > exit
The exit command, as you would expect, exits us from the msfconsole and back into the BASH command shell.
Notice that in this case, it stops the webserver that we created in this exploit and returned us to the Kali command prompt in the BASH shell.
Although this is less than an exhaustive list of Metasploit commands, with just these commands you should be able to execute nearly 100% of the functions in Metasploit. When you need another command in this course, I will take a few minutes to introduce it, but these are all you will likely need.
In many exploits, you will see the following options (variables).
RHOST – this is the remote host or target IP
LHOST – this is the local host or attacker IP
RPORT – this is the remote port or target port
LPORT – this is the local port or attacker port
IV. Payloads
Metasploit has numerous payloads that we can use to leave behind on the target system and maintain access. There are 335 payloads and the number is changing constantly as new payloads are developed.
Among these 335 payloads in Metasploit, there are 8 types of payloads.
Inline
These payloads are a single package of exploit and payload. They are inherently more stable, but because of their size, they can’t always be used in small vulnerable memory areas.
Staged
These payloads essentially are able to fit into very small spaces and create a foothold on the system and then pull rest of the payload.
Meterpreter
Is the all powerful payload that we most often want on a victim system. It works by .dll injection and resides entirely in memory, leaving no trace of its existence on the hard drive or file system. It has a number of specific commands and scripts developed for it, enabling us to largely work our will on the victim system.
PassiveX
This payload is for use when firewall rules restrict outbound traffic. In essence, it uses ActiveX through Internet Explorer to hide its outbound traffic and evade the firewall by using HTTP requests and responds just as any browser would.
NoNX
In some CPUs, there is a built-in security feature called DEP (Data Execution Prevention). In Windows, it is referred to as No eXecute, or NX. The idea behind this security feature is to keep from data making its way to the CPU and being executed. The NoNX payloads are designed to evade this safety feature of modern CPU’s.
Ord
These type of payloads work on nearly all Windows operating systems. These are extremely small, but somewhat unstable. They are dependent upon loading a .dll (dynamic link library) into the exploited process.
IPv6
These payloads, as their implies, are designed to work on IPv6 networks.
Reflective DLL Injection
These payload modules are injected directly into the target process while it is running in memory, thereby never writing anything to the hard drive and leaving little or no evidence behind.







