Editor’s Note: This article was submitted by Skrub, a loyal reader from my Null Byte days. Although he submitted it as two separate articles, I combined them into a single article with two parts.
Enjoy!
This is my first article on Hackers-Arise, it’s based off of a project that I’m working on at school which is on three ways to bypass windows user passwords. If all goes as planned and you all would like I’ll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt (he’s kind of a celebrity around here having won the Null Byte tutorial contest), both of whom are my classmates at college and have helped me with writing this article.

Step 1: Booting into Kali/Parrotsec and Navigation to SAM
In Part 1 we will focus on using Kali Linux or ParrotSec to remove the password of a specific user in the SAM file. We will need a bootable usb with your choice of operating system, so that we can boot directly into Kali/Parrotsec.
Once we have booted into our flavor of Linux, we need to mount the local hard drive. We must mount before we can have access to the hard drive or it will not show up. To mount, simply click on Places > Home > “Primary Hard Disk” (This name will vary with each computer.)
After we have accomplished this the next step is to open up a terminal. At this point we need to change directory, using the cd command, to root. Now all we need to do is navigate to the place on the hard drive that contains the password information. Navigating to the location can get tricky for new users. The ls command is incredibly helpful with finding out what files and folders are located in the directory that we are currently in. Once we navigate to the config folder your location should look something like the image below. (Once again the name of the hard drive you are accessing will vary by system.)
Step 2: Selecting the User
Our next act will be to use the chntpw -l SAM command without the brackets. What this command does is to list the users and the corresponding permissions level. The very important part that we need to be aware of is the RID. The RID is what we will be using to specify which user account that we are going to modify.
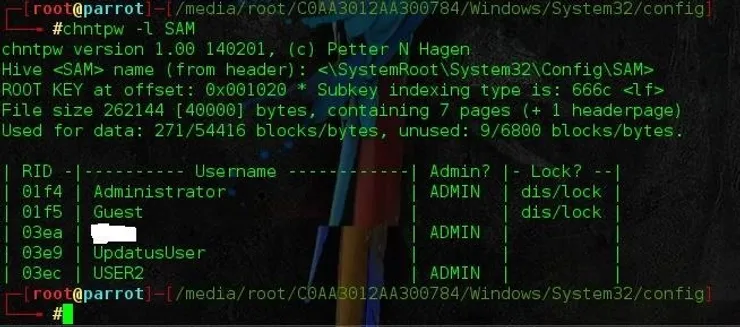
In this case we are going after USER2, so the RID we need is 03ec.
Step 3: Removing the Password
When we are sure of which user account that we want to modify we use the chntpw -u 0x03ec SAM command. It is very important that we put the 0x before the 03ec because if it’s not there the command will not be recognized.
After we execute that command we will be presented with choices of what to do with that particular user.
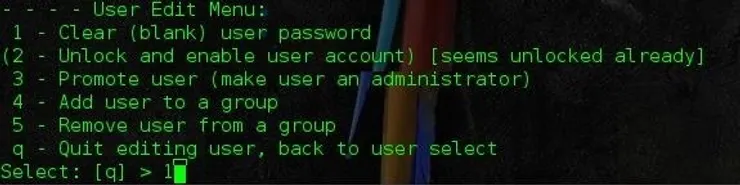
As shown above, we want to choose the 1 option to remove the password. After that it will ask if we want to write to hive files. Type y otherwise all the work we have done will go out the window and we will have to re-execute the commands.
Once this is done then reboot and if everything was done correctly, the user we chose should not have a password. If it still does then unfortunately we will have to redo all of the steps above. At this point I have only done this on Windows 7, I will be trying all three methods on my windows 10 laptop and update with the results.
Why Would We Need to Know These Technique’s?
If we are working in an office as a tech there will inevitably be an occurrence of an end user forgetting a password. Now depending upon the organization that you are working for, there might be policies in place that allow for bypassing or disallow it altogether. Ethically we are bound by these policies. On the other hand lets say we are in class and feel like messing with a fellow classmate by changing their background or any other pranks (not that PMB nor I have any experience in this), these technique’s will come in handy.
-Skrub
Part 2
This is the second installment of the short series on how to remove user passwords in Windows. Once again this has only been tested on Windows 7. If I can find some time between two jobs and school I’ll test all the ways on Windows 10 and Windows 8/8.1.
Step 1: Startup Repair
The route of using the command line can be a little more complex than the other two ways. On the other hand it can be more simple in that we don’t need to rely on having a bootable usb, everything we need is already installed on the machine. Our first step is to force the computer into its startup repair mode. To do this we need to boot the computer up and the moment that the Windows logo appears perform a hard reset. In short, hold down the power button down until it turns off completely. Next, reboot the computer and let it load up until you get a screen like below.
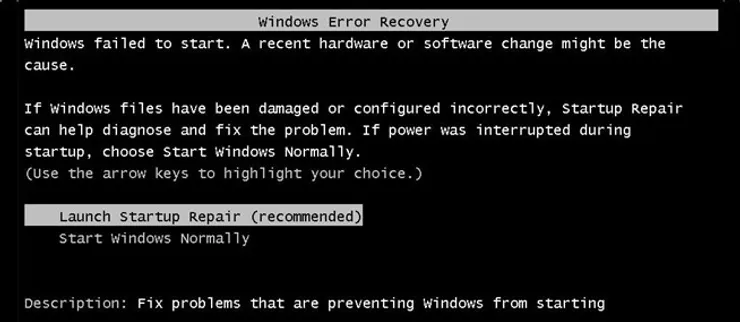
The option that we want to choose is Launch Startup Repair. Let it run its course and when we get a pop up window that says “Startup Repair cannot repair this computer automatically.” there will be a button with a down arrow on it with text to the right that says “View problem details.”. Once you locate that arrow click on it and scroll all the way to the bottom. There will be a link that looks like the one in the picture below.
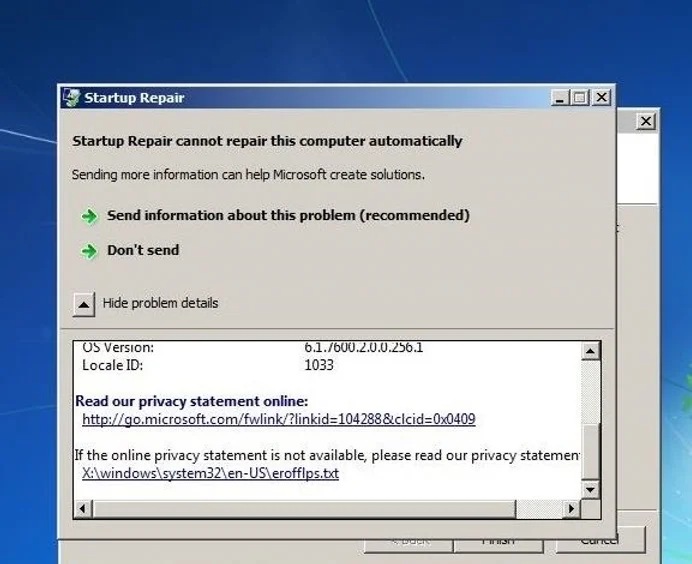
Step 2: Navigating and Renaming
Click that link and it will open up a text file. We don’t care about the contents of the file, rather we use it as a path to the next step. Go to File and click Open. What this does is give us a way to access the System32 file. But before we get to that point go ahead and change the type of file from Text Documents to All Files. This is very important in that if we don’t do this we won’t be able to see the files that we need to rename. Once that is done in the left hand pane click on Computer. The next series of steps is literally just clicking to navigate to System32. The order should go something like Local Disk>Windows>System32.
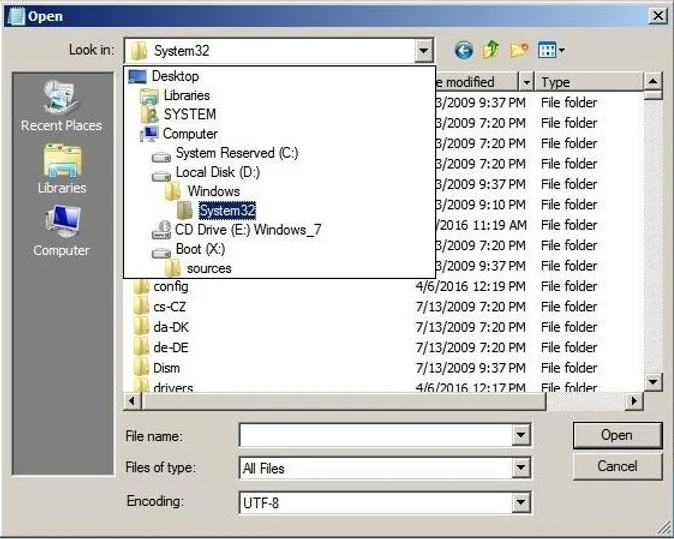
Once we are here we need to find the cmd executable and sethc. In short, we are going to rename them with each others name. It is very important to rename one of them a variation of one of their names before you try to give either one the specific name. For instance, I renamed cmd to sethc1 then renamed sethc to cmd and then back to sethc1 and removed the 1. Now I’m sure that there is a more streamlined way to do this but it’s just how I did it this time. Once we have accomplished this back out of where you are and restart the computer.
Step 3: Changing the Password Using Command Prompt
As it boots let it go to the login screen like a normal boot up, instead of putting in a password as usual, we are going to hit the right shift key five times. What this does is brings up a command prompt window. In the newly opened command prompt window type in the command net user (username)(password). It is very important to note that the username is the user we are trying to access and the password is whatever we want the new password to be.
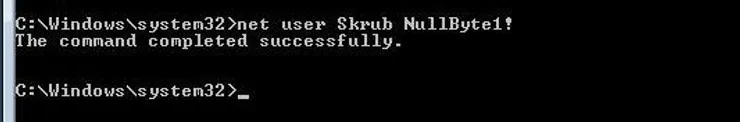
In this example I have chosen to go for the User Skrub and make the Password NullByte1! If we’re successful the response will look like the one above. Now we can log in with your new password.
Step 4: Cleaning Up
Don’t forget that we need to revert the names of the files to their original. If we try to rename it while logged on to the user we get an error that looks like the picture below.
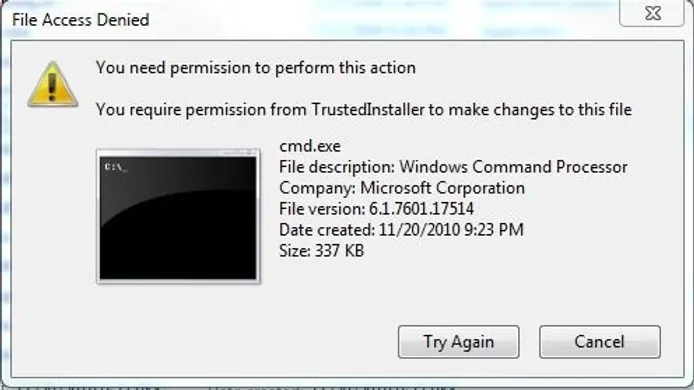
For us to successfully rename the programs back all we need to do is run startup repair again and it will be reverted to original. That’s it! We’ve successfully created a new password, gained access to the user, and reverted the changes that we had to make in the process. Thanks for reading!