Welcome back, my novice hackers!
One of the most common questions that Hackers-Arise readers ask is: “How can I evade detection by antivirus software on the target?” I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

For the remainder of this series, we will be dissecting the most widely used, open-source, multi-platform AV software in the world, ClamAV.
Just a quick side note before we begin: when I use the term antivirus, you can substitute anti-malware. I prefer the term anti-malware as viruses are a subset of malware, but the industry and the public still use the term antivirus, so I will use them synonymously. Please don’t be confused.
About ClamAV
ClamAV is an open-source (GNU public license) project that was purchased by Sourcefire in 2007, the same company that purchased Snort. When Sourcefire was purchased by Cisco in 2013, both Snort and ClamAV became a part of Cisco, the networking giant.
As detailed on their blog:
“The ClamAV detection engine is multifaceted—heuristics, support for numerous archivers (ZIP, RAR, OLE, etc.), tons of unpacking support (UPX, PEtite, NSPack, etc.), and several different content inspection engines.
“MRG did a third-party evaluation of Immunet Protect (uses ClamAV as one of its engines) where it outscored 15 other leading AV vendors and was the ONLY product that had a 100% detection rate.”
ClamAV is just as effective as commercial antivirus software, and is widely utilized to protect email gateway systems, though, generally not consumer level systems. ClamAV did recently develop a Windows version, so its acceptance at the consumer level is likely to improve.
The beauty of working with ClamAV is that it is open source, so we can open it up and look inside to see and understand how it works. By doing this, we will have a better understanding of how all AV software works, and therefore can better devise strategies to evade it. This is not to say that all AV software works the same, but they do work similarly.
In this series, we will be examining the structure and operation of ClamAV. We will also look at its malware signatures, as well as develop our own malware signatures based upon some of the malware we use here on Hackers-Arise to learn about hacking.
Step 1:Fire Up Kali
The first step, as usual, is to fire up Kali and open a terminal.
Step 2: Download ClamAV
Next we have to download and install ClamAV on our Kali Linux system. There are multiple ways you can download ClamAV. The first, and probably the simplest, is to use the APTITUDE package manager:
kali > apt-get install clamav clamav-freshclam
Or, you can browse to the ClamAV website and download it. Just make certain you download the Debian Linux version as Kali is built on Debian.
Finally, you can clone it directly from the Git repository at:
kali > git clone http://git.clamav.net/clamav.devel.git
This is the method that I would advise you to use here for our purposes, as it installs the developer version of ClamAV.
Once ClamAV is downloaded, navigate to it’s directory by typing:
kali > cd clam-devel
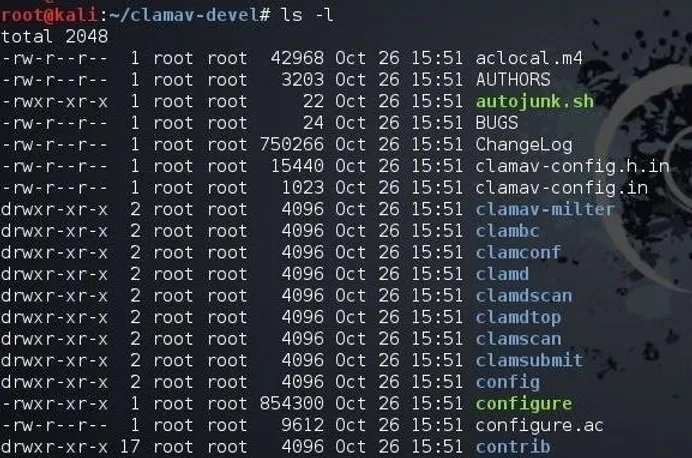
Then, let’s look inside the directory to see what files and directories ClamAV installed.
kali > ls -l
Step 3: Configure & Make ClamAV
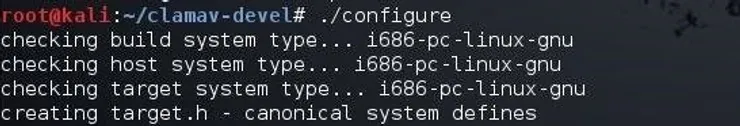
If you cloned the developer version of ClamAV, you will need to configure and make it. To configure ClamAV, use:
kali > ./configure
To make ClamAV, use these two commands:
kali > make
kali > make install
Be patient, these steps can take awhile. I also recommend that you run ldconfig before proceeding any further:
kali > ldconfig
Step 4: Download the Virus/Malware Signatures
Now that we have ClamAV installed and configured, let’s get the virus signatures. ClamAV stores these signatures in compressed files named main.cvd and daily.cvd. The main.cvd is a database of known virus signatures, while the daily.cvd is the “daily” updates to the virus signatures (actually, ClamAV updates signatures 4x per day).
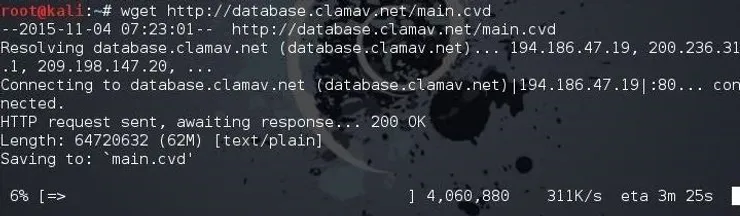
You download the main.cvd using wget by typing:
kali > wget http://database.clamav.net/main.cvd
and then the daily updates of malware signatures at:
kali > wget http://database.clamav.net/daily.cvd
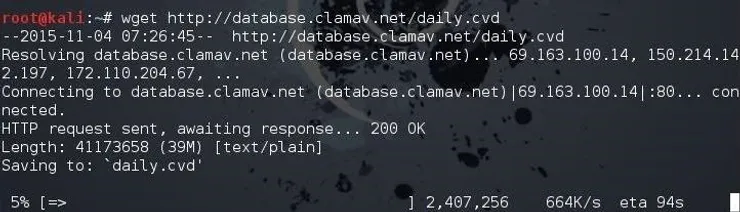
Step 5:Detection Databases in ClamAV
ClamAV maintains a number of databases of malware that it uses to compare the files it is examining. These include:
MD5 hashes of known malicious binaries (.hdb)
MD5 hashes of PE sections (.mdb)
Hexadecimal signatures (.ndb)
Archive metadata signatures (.zmd or .rmd)
Whitelist of known good files (.fp)
Step 6: Examine ClamAV Signatures
The signatures in ClamAV are compressed binary files. If you want to view a virus signature, you must first uncompress the file. To do this, ClamAV comes with a special tool to view its signature files, named sigtool, which stands for “signature tool”, presumably.
Navigate to the sigtool directory within ClamAV and type:
kali > ./sigtool
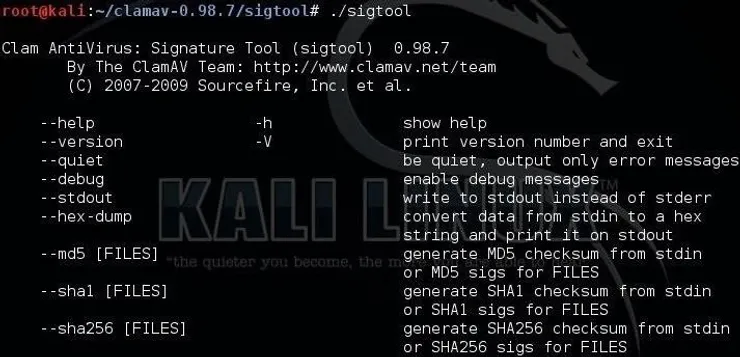
This displays the help file for sigtool. It is this tool that we will be using throughout this exploration of ClamAV. You can see some of the switches for this tool in the screenshot above.
Step 7: Unpack the Signatures
There are two signature files, main.cvd and daily.cvd. The first being the primary database of signatures, the latter being the daily updates of signatures. Let’s unpack them now with sigtool and take a look. We will use the -u switch for unpack.
kali > sigtool -u main.cvd kali > sigtool -u daily.cvd
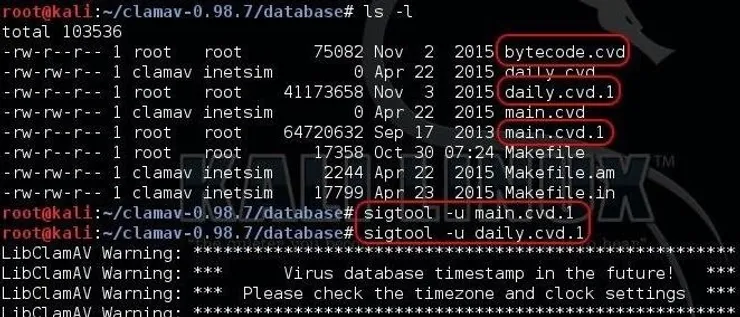
After unpacking these signatures, we can see many more files in the ClamAV database directory. These are the uncompressed signatures.
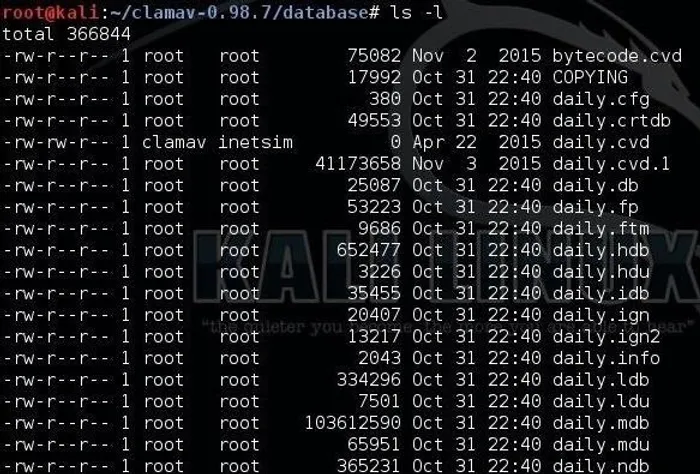
Step 8: View the Signature Files
Next, let’s take a look at some of the signature files. We can use the Linux command more to display the contents of the daily.ndb file. The daily.ndb file is the hexadecimal representation of the signatures. This means that the signature name will be in ASCII, but the signature itself will be in hex.
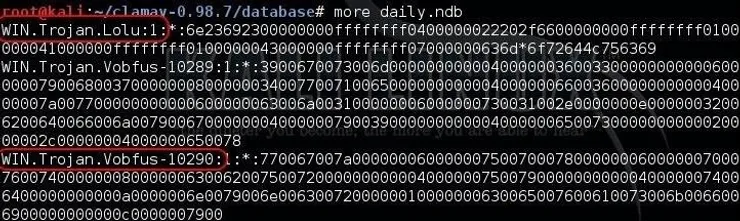
As you can see in the screenshot above, the name of the signature (circled in red) is in ASCII (WIN.Trojan.Lolu and Win.Trojan.Vobfus), but the rest of the signature is in hex. In the next tutorial, we will convert that signature to ASCII, then look at the signature language of ClamAV and decipher what the signature is looking for.
A Final Note
I do not recommend that you activate or run ClamAV on your Kali system, since nearly everything we use is known malware. ClamAV will identify your tools as malware and try to quarantine them, hence making your Kali a mess. If you have followed my instructions here, ClamAV is not activated and the daemon is not running—it should not interfere with your hacking platform.
Keep coming back, my novice hackers, as we explore the inner workings of AV software!





