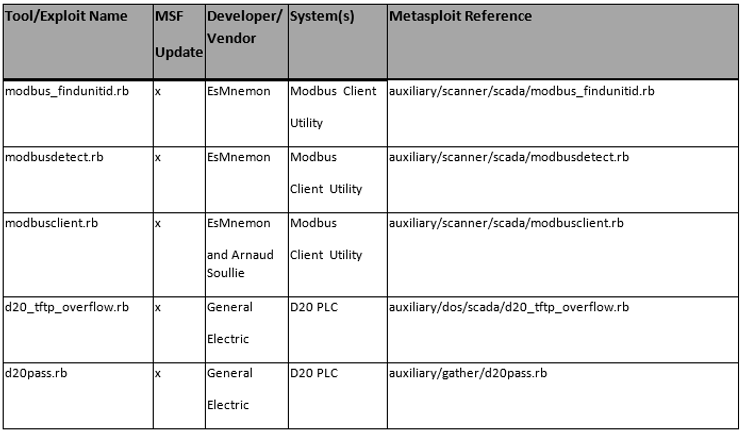
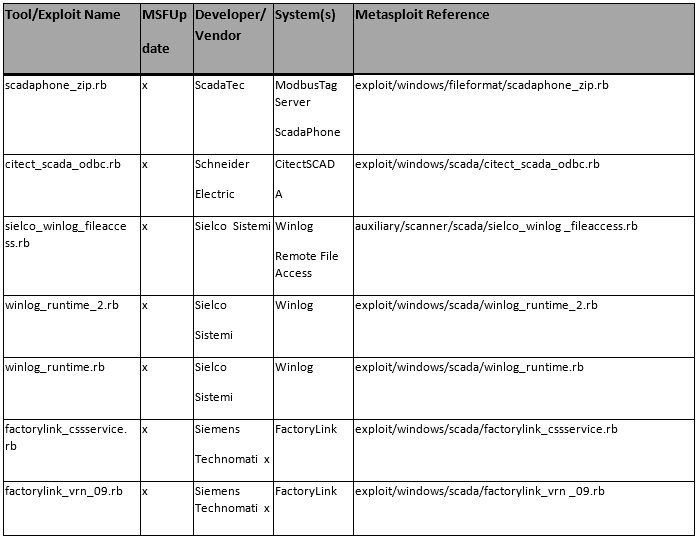
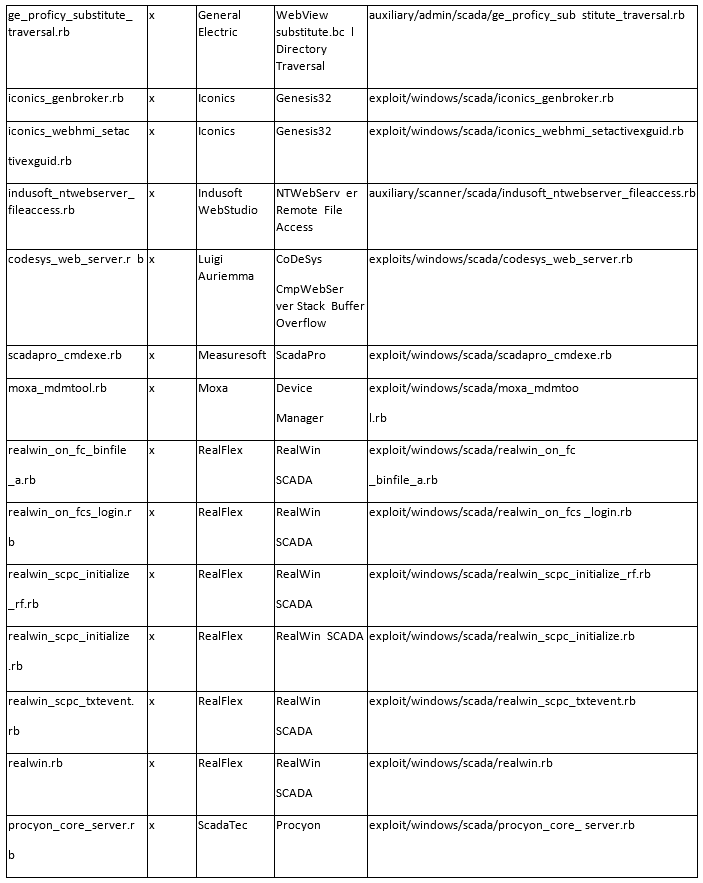
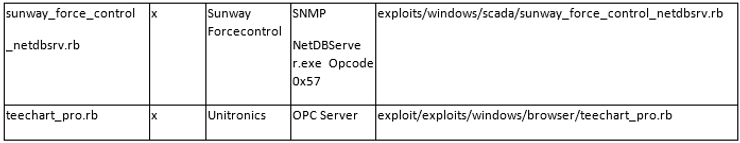
As a penetration tester/hacker, we have many resources we can use to test SCADA/ICS system security. One of the most popular is the Metasploit Framework.

Here, I have tried to compile a list of most of the Metasploit modules that are useful for testing/hacking SCADA/ICS. Please keep in mind that SCADA/ICS sites use varied hardware and protocols, so reconnaissance becomes critical for a successful hack. You will need to know, at a minimum, the manufacturer and the protocol and then find the appropriate module from this list.
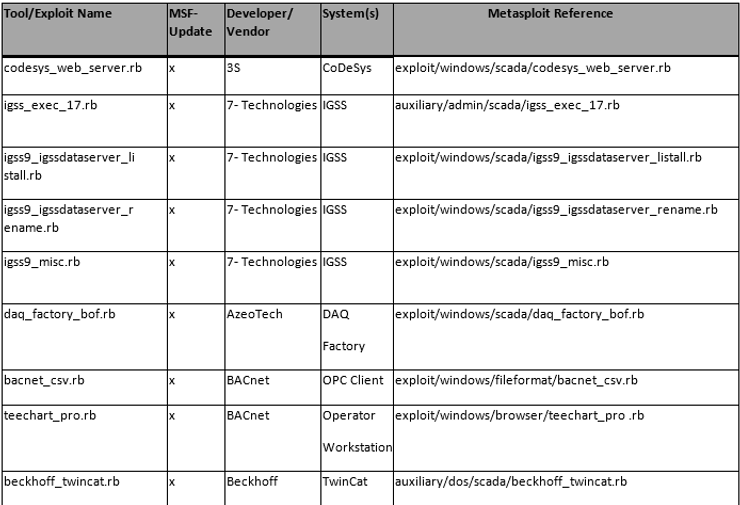
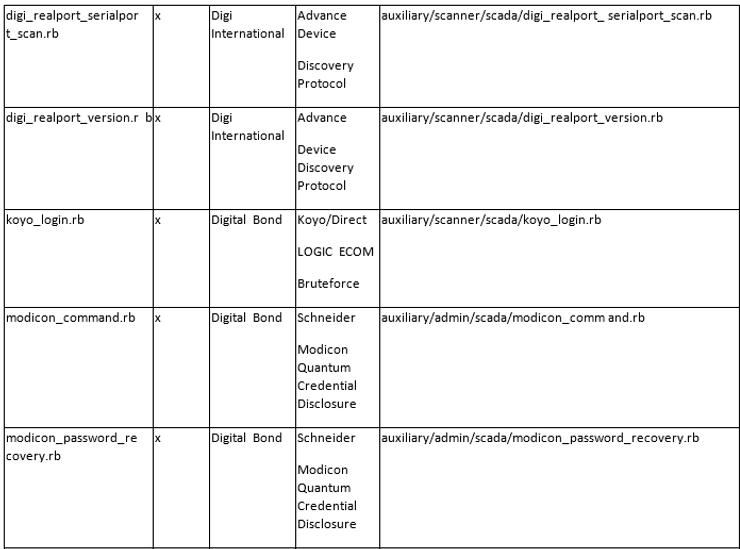
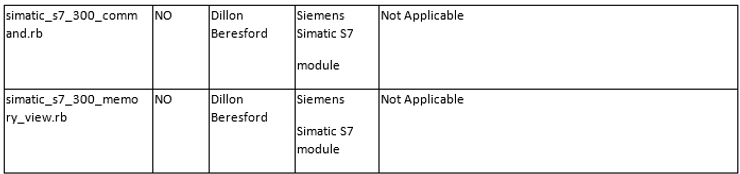
The List Format
This information is organized in the following format;
Tool/Exploit MSF-Update Developer/Vendor System(s) Metasploit Reference
I believe that most of these columns are self-explanatory with the possible exceptions of MSF-Update and System(s).
The MSF-Update column indicates whether the module is available when you do a an update on Metasploit. Some modules will automatically update and be added to your Metasploit Framework. Others, you will likely need to add manually.
The System(s) column indicates the systems vulnerable to the exploit/scanner module. Once again, I want to emphasize the varied nature of SCADA/ICS systems.
Please note that the modules are varied from exploits and auxiliary modules (primarily used for recon).
If you want to learn more about Hacking SCADA systems, see my series titled “SCADA Hacking” here and if you need more information on Metasploit, check out my Metasploit series here.