One the most important distinguishing characteristics of SCADA/ICS systems from that of traditional IT systems is that these systems communicate by distinctly different and, sometimes, proprietary protocols. In my previous tutorial, I detailed the inner anatomy of a the most common SCADA/ICS protocol, MODBUS. In this article we will examine probably the second most widely used protocol among SCADA/ICS systems, Distributed Network Protocol 3.0 or DNP3.

DNP3 was first developed by Westronic (now a division of GE-Harris), and was released in 1993. This protocol is widely used among the electric, oil and gas, and wastewater/water utilities. It is preferred among the electric utilities, in part, because;
(1) it is resistant to EMI-induced distortion,
(2) it works reliably over varied and low-quality media
(3) it can address 65,000 devices in a single link
All these characteristics that are highly-valued among electric utilities and the oil and gas industry with widely remote field stations.
DNP3 was based upon the early drafts of IEC 60870-5. DNP3 was extended in 1998 to be encapsulated in either a TCP or UDP packet (TCP is typically used). DNP3 is usually configured to work over TCP port 2000.
DNP3 is a robust, flexible, reliable and non-proprietary (community managed by dnp.org) communication protocol. It supports;
(1) multiple data types
(2) multiple master stations are supported for outstations
(3) data types may be assigned priorities
(4) time synchronized and time-stamped events
(5) broadcast messages
(6) data link and application layer confirmation
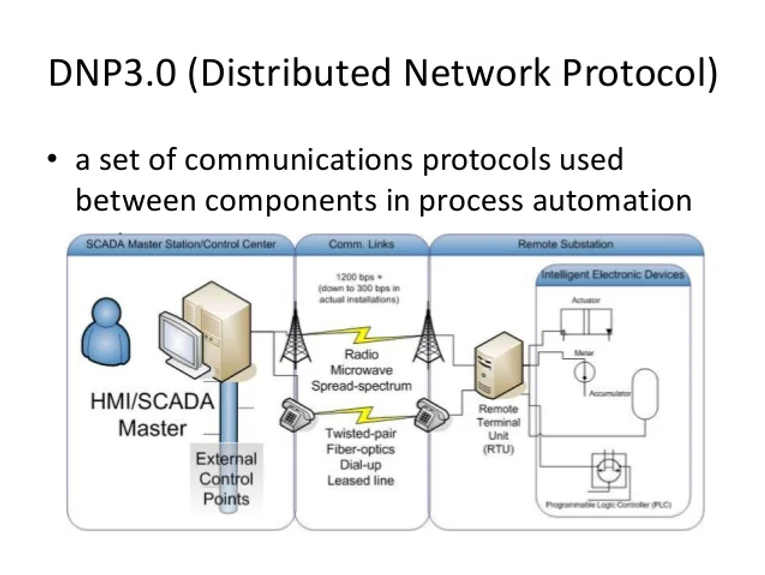
DNP3 is usually configured in a client server configuration–like Modbus–where the control center is the SCADA client and the server within the remote units (RTU, PLC, IED, etc.). The differences with Modbus include;
(1) an outstation can send an unsolicited response to the master
(2) report by exception (RBE). SCADA server polls for change events
(3) has defined other layers including application, transport and data link layers
DNP3 Communications
Each DNP3 packet starts with two bytes 0x05 and 0x64. These are usually referred to as the start bytes or start frame. This starts the Data Link Layer frame which is the initial section of a DNP3 packet, as seen below.
DNP3 Frame
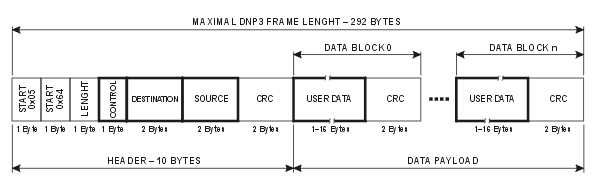
In the diagram below, we can see the data link layer of the DNP3 communication. This section includes;=
(1) start bytes
(2) length
(3) control
(4) destination
(5) source
(6) CRC error checking
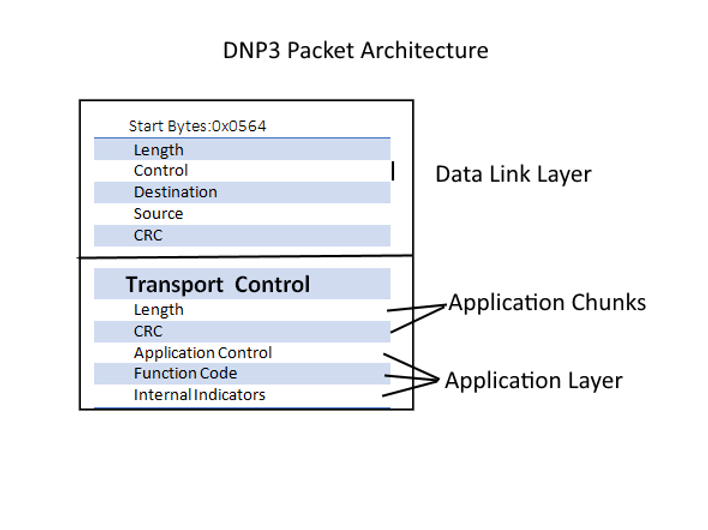
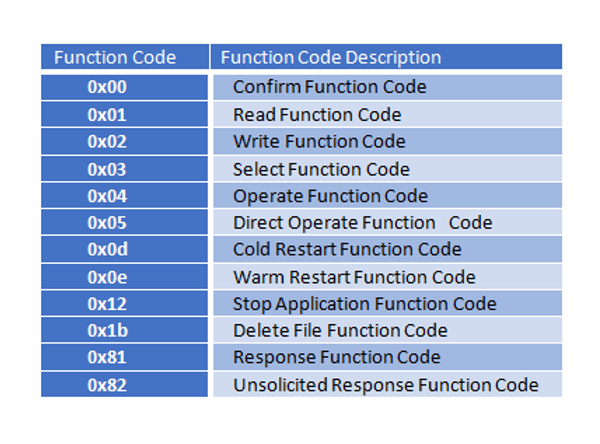
The Application Layer section of the packet includes the instructions as seen below. Note that Function Code 0x12 is “Stop Application” This can be used to effectively create a Denial of Service, if sent by an attacker.
DNP3 Function Codes
DNP3 Security
Unfortunately, DNP3 was developed before security was a major concern. As a result, DNP3 has no built-in security. For instance, there is no authentication or encryption. This lack of authentication and encryption combined with the standardization of the function codes and data types, makes spoofing and eavesdropping attacks relatively simple and straightforward.
There are a number of well-known vulnerabilities and exploits in the wild against DNP3. These include MiTM attacks, DoS attacks, manipulating time synchronization, suppressing alarms and more. I will have a tutorial on the DNP3 attacks coming soon.
DNPSec v5 has been developed in response to address security concerns such as spoofing, modification, replay attacks, and eavesdropping. As of today, this new, more secure standard has yet to be widely accepted and implemented.



