Welcome back, my aspiring White Hat Hackers!
In this series on the world’s most popular exploitation framework, Metasploit, we have looked at the many ways to get started, including;
1. Getting Started and Keywords
2. Modules
3. Payloads
4. Connecting the postgresql Database
5. Scanning and Reconnaissance
Before we advance to exploitation, I want to introduce you to one more way you can interact with Metasploit. Throughout this series I will be using the most popular interface, the msfconsole, but that is not the only way to use Metasploit. Metasploit has multiple interfaces;
1. msfconsole
2. Armitage
3. msfcli
4. web access
In this tutorial, I want to introduce you to Armitage. Developed by Raphael Mudge, this easy to use GUI makes Metasploit more accessible to the beginner. The drawback is its use of system resources.
Let’s get started with Armitage!
Armitage
After the msfconsole, the Armitage GUI is probably the most popular Metasploit interface. It is particularly favored by those that come from a Windows or Mac interface and want an easy to use graphical user interface (GUI).
To install armitage, simply use the apt-get command as Armitage is in the Kali repository.
kali > apt-get install armitage
Then, we start the postgresql database.
kali > service postgresql start
Now, we simply enter the “armitage” command, and the connection window pops up. Simply click “Connect”.
This now starts the msfrpcd (the Metasploit Framework RPC daemon). This loads all the Ruby scripts and takes awhile, so be patient.
Eventually, Armitage loads completely and presents you the Armitage interface (when I first loaded Armitage, I received numerous error messages but this did not seem to interfer with the smooth operation of Armitage).
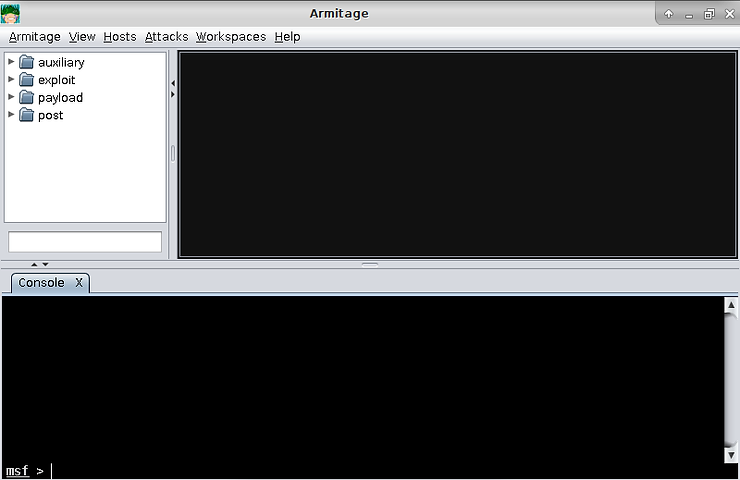
As we can see in the upper left corner, Armitage presents us with an easy-to-use directory explorer. The directories are broken out into the different types of modules, auxiliary, exploit, post, and payloads.
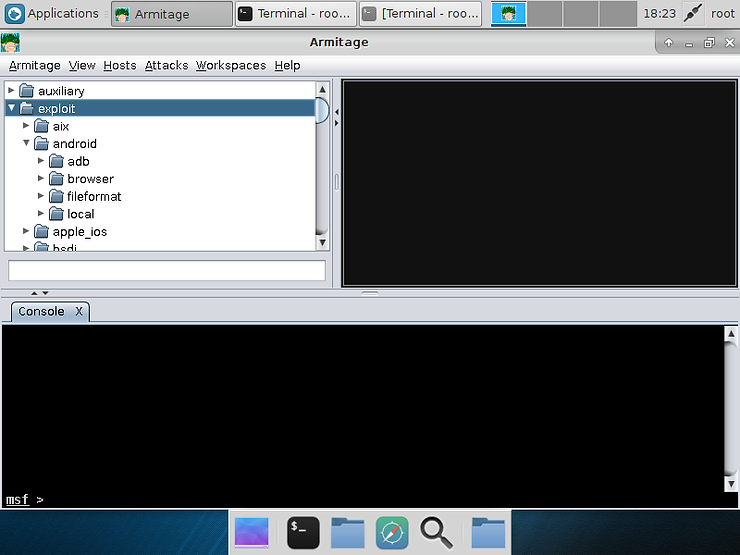
Let’s take a look at the exploits modules. Click on the arrow next to exploits and expand it. Now, you can see that the exploits are in sub-directories based upon target type, primary broken out by operating system. Let’s open up Android and then the sub-directory “browser”.
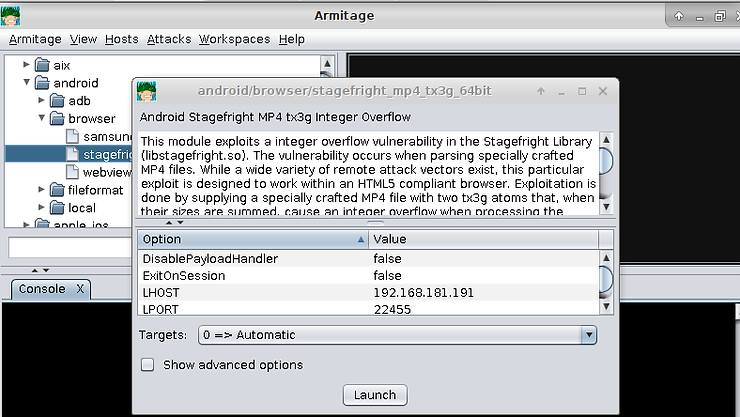
There, we will find three exploits for Android browsers. When we double click on the infamous, Android Stagefright exploit, it opens another window with all the information we need to use this exploit, including info in the upper window, the options in the middle window and targets beneath that. At the very bottom, we can see the launch button (exploit). Simply make certain that all the options are set correctly and then click on “Launch” to exploit the Android target.
Conclusion
Armitage is one more way to access and use the Metasploit framework. It provides an easy to use GUI interface making it easier for the novice pentester/hacker. It’s only real drawback is that it uses significantly more system resources than the msfconsole.





