Welcome back, my newbie hackers!

In previous articles this section, I showed you how to find WordPress sites and how to identify the vulnerabilities in these sites (WordPress comprises nearly 30% of all websites). In this tutorial, we will use wpscan again to enumerate the user accounts on that WordPress site and then brute force the passwords on those user accounts.
Step #1 Fire Up Kali
The first step, of course, is to fire up Kali.

Step #2 Enumerating Users
Now that we have Kali up and running, open a terminal. You will remember from the previous tutorial that the wpscan tool simply requires the command wpscan followed by -u and the URL of the website you want to scan. In this initial exercise, we will be adding just one more option , –enumerate u
So, our new command to enumerate users now becomes;
kali > wpscan -u <URL> –enumerate u
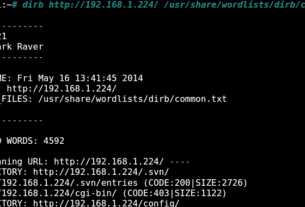
Let’s try it out on one of our “hacker” websites. Let’s begin with www.maherhackers.com. To enumerate the users on that site, we can enter;
kali > wpscan -u www.maherhackers.com –enumerate u

The script will begin to run and will give you voluminous output regarding the modules and potential vulnerabilities on that site. Eventually, it will enumerate the all the users registered to that site.

As we can see above, it found only one user with the name “Vinod” and the Login “v3king”. as he is the only user, he is likely the admin.
Let’s try the same on the other “hacker” website, www.kryptostechnology.com.
kali > wpscan -u www.kryptostechnology.com –enumerate u

As we can see, wpscan found three (3) users on that site, “wh1ter0se”, “pedro”, and “info-tech”. In this case, “wh1ter0se” is likely the admin.
Now that we know who are registered users on these WordPress-based website, we can begin the process of brute forcing their passwords. Brute forcing passwords can be a time consuming and tedious process, but for people who use dictionary and simple passwords it can pretty work well and we only need to find one user with a weak password.
Part of the beauty of using brute forcing on WordPress sites is that there usually is not lock out, so you can try hundreds, thousands and maybe even millions of passwords until you are successful.
When brute forcing the passwords of a WordPress site, the syntax is;
kali > wpscan -u <URL> –wordlist <wordlist file> –username <username>
The two keys here are the wordlist and the username. Since we have the username, all that is left is the wordlist. Brute force password cracking is only as good as your wordlist. There are numerous wordlists built into Kali and even more that can be downloaded off the web. I always recommend using small wordlists with common passwords first. No point in spending hours or days attempting millions of passwords, if the password is “p@ssw0rd”.
Kali has numerous password lists that can be located by entering;
kali > locate wordlists
You can use any of these, but I often use a list of common passwords first such as 500-worst-passwords.txt that is available for download from several places on the web. These easy and common passwords are always the place to start before advancing to larger, more complex and more difficult passwords.
For the first site that we enumerated the users from above, www.maherhackers.com, the command to brute force the password of “v3king”would be;
kali > wpscan -u www.maherhackers.com –wordlist /root/Downloads/500-worst-passwords.txt –username v3king

Press ENTER and wpscan will repeatedly attempt all 500 passwords on the list. This should only take a few minutes.

In this case, wpscan was unable to find the password among the 500 worst passwords. The next step then is to use a different and larger wordlist such as rockyou.txt. Using this much larger list can take hours and even days, though. Other alternatives might be to create a custom wordlist using crunch or scraping the website with CeWL for words that might be meaningful to site’s owner and creating a wordlist from these.
If brute forcing the password fails, you may be left to use one of the many exploits designed to compromise WordPress sites. That is exactly where we will be going next in this webapp hacking series, so make certain to come back for Part 6.