Welcome back, my aspiring car hackers!
In the previous tutorial in this series, we learned how to use the CAN utilities or can-utils to capture and send CAN packets. Now, with those tools we can begin to isolate and reverse engineer the CAN packets to take control of the vehicle!
Step #1: Use the Controller to Accelerate the Car
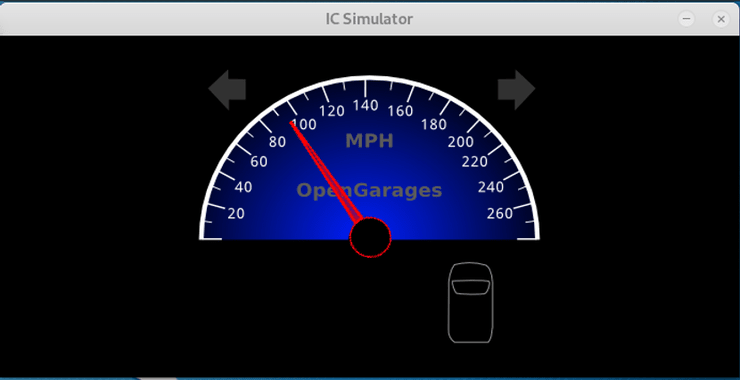
Now, with the instrument panel (like below) and the controller open, we can begin to send packets on the network to open and close doors, turn on the turn signals, and accelerate the vehicle.


Now that the Control Panel is in focus, we can begin to use the game controller or keystrokes to control our simulated vehicle.
Let’s try to speed up our car. Hold down the UP arrow key until the car accelerates to 100mph as seen below.

Release the UP arrow and the car speed will fall back to an idle again.
To reverse engineer this process, we need to find the CAN packet signal that accelerates the car to 100 mph. When we find that packet, we can then duplicate it (reverse engineer) and send it on the network to make the car accelerate to 100mph without the driver doing anything! Like a ghost has taken over his vehicle!
Step #2: Use the cansniffer to Find the Specific Packet and Values
The next step is to open the cansniffer on our CAN network.
kali > cansniffer -c vcan0
Now, with the cansniffer running, once again press the UP arrow and accelerate the car to 100mph. Watch the data pass and look for the packets that are changing rapidly (they will be in red). These packets will likely be those changing the speed of the vehicle.
As you can see below, we identified the packet with Arbitration ID 244 as a likely candidate for the car acceleration. Let’s focus on that ID.

-000000
+244
Remember, these entries will not appear on screen.
When you do, cansniffer will filter out all the traffic but that intended for Arbitration ID 244 as seen below.

Now, accelerate the car to 100 mph again and watch the values change. When you reach the maximum speed, you will likely see values similar those above. Record these values on paper.
Step #3: Reverse Engineer the Accelerate Packet
We can now send a packet with that Arbitration ID and those values over the network by using the cansend utility. Remember, the cansend utility requires the interface, followed by the arbitration ID, followed by a #, and then the values, such as;
kali > cansend vcan0 244#0000003812

This packet will signal to the car to accelerate to 100mph!
Although this is the right packet, you might not notice any change in the speedometer. That is because the CAN network is simultaneously sending signals to also idle at 0mph. The car is getting mixed signals. The car’s normal control system is telling it to run at 0 mph and you are sending a single packet to accelerate to 100 mph.

Let’s try writing a simple script to send continuous packets telling the car to accelerate, such as;
kali > while true; do cansend vcan0 244#0000003812; done

Now hit ENTER and see what happens!

The car should immediately begin to accelerate to 100 mph! You have taken control of the car!
Summary
The can-utils and the ICSim are excellent training tools for understanding how the CAN protocol works and reverse engineering the control signals and packets on the network. Although there are many vectors for gaining access to the car such as GPS, cellular and wireless networks, once inside the car’s network we need to determine what signals control which functions. This tutorial, I hope, provides you with some idea of how this process works.
For more on Automotive or Car Hacking, check out the Car Hacking course at Hackers-Arise!