Welcome back, my aspiring cyberwarriors!
In the first part of this series, Cryptography Basics for Hackers, we reviewed each of the many types of encryption. One of those types is hashing or one-way encryption. Hashing is used throughout cybersecurity to ensure integrity for such things as software downloads, passwords, and digital certificates. In digital forensics, hashing is used to ensure the integrity of image captures of storage devices such as hard drives and flash drives.

In addition, the Bitcoin blockchain utilizes SHA256 hashes as block identifiers. Network protocols use checksums (another name for hashes) to make certain the data has not been altered or corrupted, in other words, to check integrity. An X509 digital certificate includes a hash value known as the fingerprint, which can facilitate certificate verification. These are just a few of the multitude of ways that hashes are used in cybersecurity today.
In Cryptography Basics for Hackers, Part 1, we introduced you to hashing concepts. In this tutorial, we will focus on hashes and hashing from a practical aspect in our Kali Linux.
Step #1: Fire Up Kali Linux
The first step, of course, is to fire up Kali and open a terminal.

Step #2 Linux Hashing Tools
Nearly every distribution of Linux has hashing tools and, as you would expect, Kali Linux is no exception. We can test these hashing tools by generating a random bit of text and running it through some of the most common hashing algorithms such as MD5, SHA1, SHA256 and SHA512.
Let’s try a short and tautological statement to test each of these hashing tools such as “Hackers-Arise is THE Best place to learn cybersecurity.” We can use the echo command followed by this statement and then pipe it to the hashing command such as;
kali > echo -n “Hackers-Arise is the Best to learn cybersecurity”| md5sum

As you can see above in the second line, the system responds with the MD5 message digest (MD). We can do the same for SHA1, SHA256, and SHA512.
If you prefer a GUI tool for creating hashes, consider gtkhash. You can get it from the Kali repository.
kali > sudo apt install gtkhash
To start gtkhash, simply enter;
kali > sudo gtkhash

Note that by default, this tool includes MD5, SHA1, SHA256 and CRC32 hashing algorithms. If you need other hashing algorithms, click on Edit tab and then click Preferences. This will open a menu like that below.

To use any other hash algorithms, simply click the radio button next to the algorithm and the initial window will re-populate with the new algorithms.

Step #3: Hash identifier
When trying to crack hashes with tools such as hashcat and others, the first step is to identify the type of hash. Obviously, the hash cracking tool needs to know what hashing algorithm to use before cracking it. Some tools, such as John the Ripper, have hash auto detection which is VERY useful, but unfortunately it is not always accurate. hashcat requires that you input the type of hashing algorithm before cracking a hash. When we run the hashcat help screen, we can see hundreds of hashing algorithms listed.

Luckily, if we don’t know which hashing algorithm created the hash, we have a tool built into our Kali Linux that can help us identify the it called hash-identifier. This tool can reliably estimate the hashing algorithm that created the hash by the patterns of the message digest.
To use it, we simply need to enter the command followed by the hash (our MD5 hash from our text from above) such as;
kali > hash-identifier 3f97dc48855067a56095837187099998
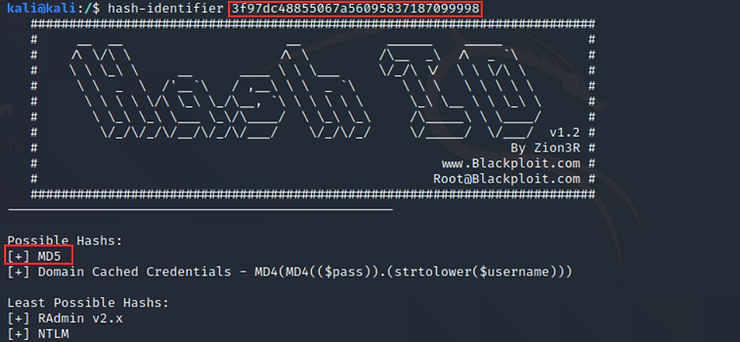
As you can see, hash-identifier was able to identify this hash as MD5! Correct!
To identify another hash, we simply enter it as the HASH: prompt at the bottom of the screen. In this case, we enter the second (SHA1) hash of our text.

Voila! It identified it as SHA-1! What a great tool!
It also lists the numerous hashes that it is least likely to be.
Let’s try the SHA-256 hash and the SHA-512 hashes of our text.

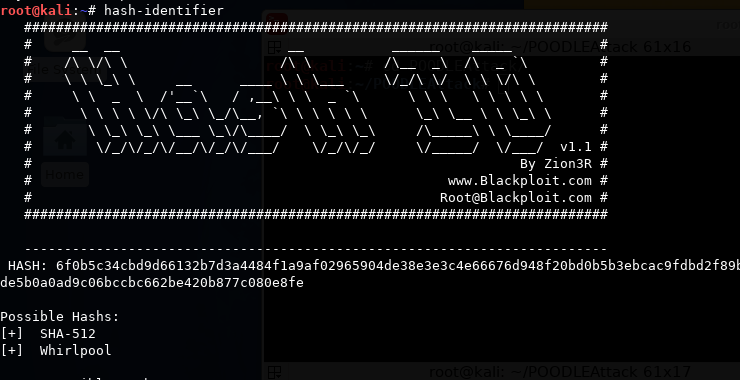
As you can see above, hash-identifier correctly estimated that this hash was SHA-256 or HAVAL-256.

Hash-identifier estimated that our hash of our text generated by the SHA-512 algorithm is either SHA-512 or Whirlpool! This is a great tool!
Summary
Hashing is one-way encryption that is used throughout cybersecurity to ensure integrity in such systems as password authentication, the blockchain, and digital certificates. When trying to use tools such as hashcat to break this encryption of passwords, the first step is to identify the hash algorithm. Tools such as hash-identify are excellent for identifying the hash algorithm by detecting the pattern of the message digest (hash).