Ransomware is a type of malware that has become almost epidemic in recent years. Consumers and businesses are being hit with this malware around the world. After infecting the victim’s computer, this malware encrypts the victim’s data making it unusable. The victim can only recover their data after paying a ransom (hence, its name) to get the key from the cyber criminals to de-crypt it. Generally, the ransoms are relatively small–usually in the $300-500 range for consumers– but there have been cases where hospitals, municipalities and other large institutions have paid $100,000 or more.

Let’s take a look at an example of some actual ransomware that was captured in the wild to better understand how it works. This is a good example of how Reverse Engineering can help us to understand how malware actually functions. Although each of the variants of ransomware is slightly different, they tend to operate similarly. In this case, let’s look at Chimera, a variant of the ransomware genre of malware found in Germany.
Using Chimera as an Example
Most ransomware has been used against consumers, but Chimera has been used primarily to attack businesses in Germany. Since most ransomware works similarly, we can use Chimera as a model of how ransomware works, generally.
In this analysis, I will summarize how Chimera works, leaving out some steps for the sake of brevity. If you would like a copy of Chimera to conduct your own thorough analysis, I have posted it in my Pastebin account here.
Step 1: Delivering the Malware
Like much of the ransomware that has appeared in recent years, Chimera was delivered by email, likely with a social-engineering component to get someone to click on a link or a file. Chimera was written in .NET.

In this first stage, Chimera initially delivers an executable stub, whose only job is to call, de-crypt, and decode the second stage payload to the victim’s machine (see Step #8).
Step 2: The AES Algorithm
The second stage is the encrypted and encoded payload that contains a method that is clearly an AES encryption algorithm. Very likely, the cyber criminals would have it run in multiple threads to speed up the process. For businesses with petabytes of data, a multi-thread process would be necessary to encrypt the files quickly before being detected.

Step 3: Mapping to Memory
In the next stage, Chimera then manually maps its processes to memory. This is very likely to bypass ASLR (Address Space Layout Randomization) and DEP (Data Execution Prevention) protections that are built into Windows and other operating systems. These protections randomize where a process will likely be located in memory, making it more difficult to implement a buffer overflow. ASLR and DEP make it difficult as the malware cannot predict the location of the execution pointer. By manually mapping the process to memory, it makes it more likely that the malware will function as expected.

Step 4: Find 32-Bit Process to Host
Next, Chimera goes through every Windows process looking for a 32-bit process that can host its payload and then open it.

Step 5: Finding the Local IP
In the next step, Chimera goes out and finds the public IP of the machine it has infected by using www.whatismyipaddress.com. It then stores that value in a variable.

Step 6: Call Back to Command & Control Servers
Once Chimera has the IP of the infected host, it then calls out to its command and control (C&C) servers. In this case, those servers are at 95.165.168.168 and 158.222.211.81.

Chimera uses Bitmessage to communicate via a P2P protocol on ports 8444 and 8080. Bitmessage is a secure, encrypted P2P messaging system that enables a single machine to send out messages to one or many recipients. You can see in the screenshot below that Chimera calls the Bitmessage client PyBitmessage.

Step 7: Browse & Find Hard Drives, Then Files
Before beginning the encryption process, Chimera must find the hard drives (or other devices) where the data is stored. It needs to browse each of the logical drives and then store these locations into a variable for later use in the encryption process.

Step 8: Get Random Key
Now that Chimera has successfully taken over a 32-bit process, mapped itself to memory (to avoid ASLR), and enumerated the hard drives, it next needs to call back to its command and control server (C&C) to get a random key with which to encrypt the files.

Once the random key has been obtained from the command and control server, Chimera calls the function from Step #2 above—the AES encryption algorithm—and begins to encrypt critical files.
Before it starts the encryption, it looks for the following file types:
.jpg, .jpeg, .xml, .xsl, .wps, .cmf, .vbs, .accdb, .ini, .cdr, .svg, .conf, .config, .wb2, .msg, .azw, .azw1, .azw3, .azw4, .lit, .apnx, .mobi, .p12, .p7b, .p7c, .pfx, .pem, .cer, .key, .der, .mdb, .htm, .html, .class, .java, .asp, .aspx, .cgi, .php, .jsp, .bak, .dat, .pst, .eml, .xps, .sqllite, .sql, .jar, .wpd, .crt, .csv, .prf, .cnf, .indd, .number, .pages, .x3f, .srw, .pef, .raf, .rf, .nrw, .nef, .mrw, .mef, .kdc, .dcr, .crw, .eip, .fff, .iiq, .k25, .crwl, .bay, .sr2, .ari, .srf, .arw, .cr2, .raw, .rwl, .rw2, .r3d, .3fr, .eps, .pdd, .dng, .dxf, .dwg, .psd, .png, .jpe, .bmp, .gif, .tiff, .gfx, .jge, .tga, .jfif, .emf, .3dm, .3ds, .max, .obj, .a2c, .dds, .pspimage, .yuv, .3g2, .3gp, .asf, .asx, .mpg, .mpeg, .avi, .mov, .flv, .wma, .wmv, .ogg, .swf, .ptx, .ape, .aif, .av, .ram, .m3u, .movie, .mp1, .mp2, .mp3, .mp4, .mp4v, .mpa, .mpe, .mpv2, .rpf, .vlc, .m4a, .aac, .aa3, .amr, .mkv, .dvd, .mts, .vob, .3ga, .m4v, .srt, .aepx, .camproj, .dash, .zip, .rar, .gzip, ., mdk, .mdf, .iso, .bin, .cue, .dbf, .erf, .dmg, .toast, .vcd, .ccd, .disc, .nrg, .nri, .cdi
These file types are likely critical to the business operation. These are graphics files, spreadsheet files, database files, backup files, email files, Java files, audio files, movie files, and encryption keys. Without them, the business would be crippled.
Step 9: Ransom Request
Finally, Chimera makes a ransom request to the business owner. Note that the browser and its associated files are exempt from the encryption to enable the browser request and receive the payment of the ransom.
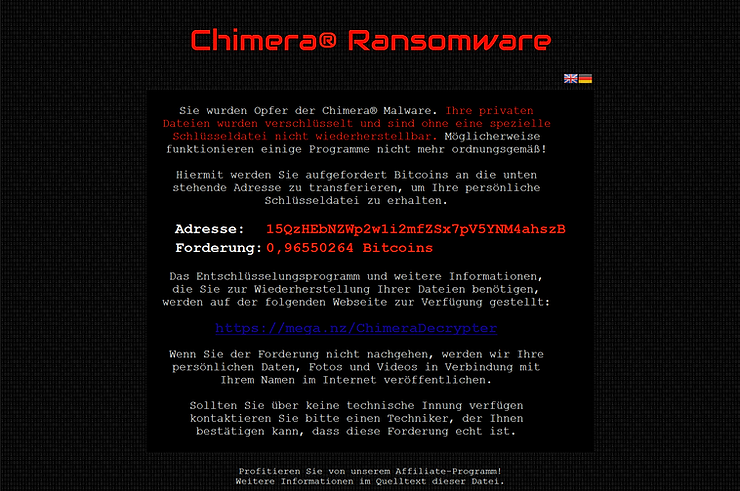
I hope this short tutorial both helps you understand how ransomware functions, but also to understand the value of reverse engineering malware. Now, with this understanding, we can develop defenses against this type of malware or re-engineer and re-purpose it just as the CIA and nearly every malware developer does.
To learn more about ransomware, attend our upcoming course Advanced Hacking and Pentesting training at Hackers-Arise. You must be a Subscriber PRO to attend this state of the art training





