Welcome back, my aspiring cyberwarriors!
Often, when doing a pentest, we have multiple Wi-Fi access points to test for security. Rather than testing each one individually with tools such as aircrack-ng, Reaver, pyrit, and hcxdumptool, and others, we can automate that testing with a single tool such as wifite. Wifite enables us to test all of the Wi-Fi AP’s with a single tool automatically using multiple strategies against different security protocols.

wifite can test the security of;
WEP
WPA
WPA2-PSK
WPS
In addition, wifite is capable of using multiple tools and strategies in these attacks such as;
Reaver
Bully
pyrit
PMKID and others
kali > sudo apt install wifite

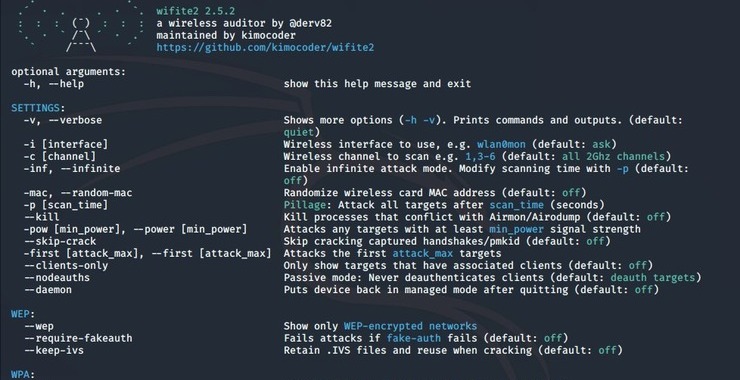
Step #1: wifite help
To begin, let’s take a look at wifite’s help screen.
kali > sudo wifite -h


Although there are many options in his tool, in general, you can use it simply by entering the command, wifite, at the command-line like below.

Note that when we do so, it states that pyrit, hcxdumptool and hcxpcaptool are not installed. We can run wifite without these as we have aircrack-ng and Reaver installed by default, but let’s take a minute to install these other tools as well.


For more on using these tools in the PMKID attack, click here.
Step #2: Kill Conflicting Processes
In addition, wifite recommends that we use the –kill option to stop potentially conflicting processes.
kali > sudo wifite –kill

Now hit Ctrl+C on your keyboard to begin attacking the Wi-Fi AP’s.
Step #3: Select Target
After you hit the Ctrl+C on your keyboard, wifite asks you to select a target. I selected 1 or the SSID, hug2g858469.

As soon as I select my target, wifite begins the process of capturing the WPA2 4-way handshake. As you can see above, the handshake was captured by tshark and NOT aircrack.
Once the handshake is captured, wifite begins the cracking process using its default password list, wordlist-probable.txt.

After just a few minutes, wifite accepts defeat and states that the wordlist did NOT contain the password.
Step #4: Using a Custom Password List
The outcome in Step #3 was not unexpected. The default wordlist is small and therefore very limited. Let’s attempt to use some larger and custom wordlists.
For more on custom wordlists, check out this tutorial from the Mr Robot Hacks section.
To use these custom wordlists, simply use the –dict switch in the command line followed by the location of your wordlist, such as;
kali > sudo wifite –dict /home/kali/top10000_passwords.txt

Here, I am using a my top10000_password list you can find here at Hackers-Arise. I strongly recommend that you use these common password lists before progressing to the massive multi-million word lists that many use and can take hours to days to exhaust.
After hitting ENTER, wifite will search and find all the available AP’s in the area and list them. To start the cracking process, once again enter Ctrl+C on your keyboard and then enter the number of the target AP.

Now, wifite begins the cracking process with the new wordlist. As you can see in the screenshot above, wifite successfully cracked the AP Pre-Shared Key (PSK)!
Summary
When conducting a wireless penetst, wifite can save you time and headache by automating the testing process. Capable of cracking WEP, WPA2-PSK and WPS, wifite is an essential tool in the hacker/penester/cyberwarriors toolbox!