Welcome back, my aspiring cyber warriors!
The Internet is the largest data repository the world has ever known! Open Source Intelligence or OSINT is the way to gather and unlock the intelligence embedded in all that data.
In recent years, a brand new reconnaissance framework has become available to us that leverages many of the tools we are already using, but makes them far more powerful. Rather than manually searching for the data from innumerable data sets, recon-ng enables you to automate your data searches saving you time and energy.
recon-ng, was developed by Tim Tomes while at Black Hills Information Security. He developed it as a Python script and tried to model its usage after Metasploit, making it easy for a pentester with Metasploit skills to use recon-ng with a very short learning curve
It is built into Kali, so there’s no need to download or install anything.
Let’s explore its many and powerful capabilities a bit here.
Step #1: Fire Up Kali and Open a Terminal
The first step, of course, is to fire up Kali and open a terminal like below.

Step #2: Start recon-ng
To start recon-ng, we simply need to enter the command “recon-ng” at the command line.
kali > recon-ng
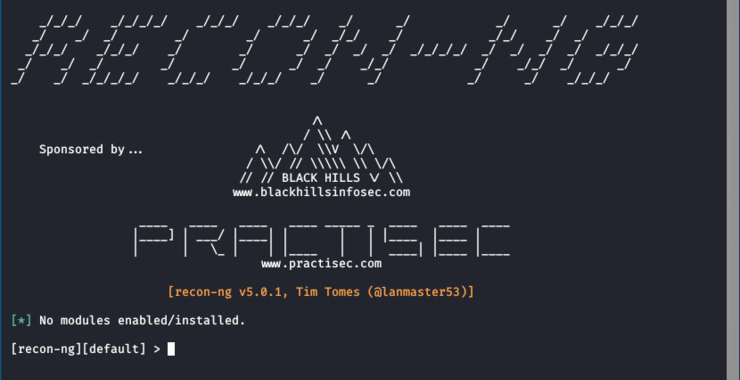
When recon-ng starts you will be greeted by it’s splash screen as seen below.

Next, let’s find out what commands we can use in recon-ng by entering help at the recon-ng prompt.
[recon][default] > help

If you have used Metasploit, you can see many of the same commands such as use, set, show, search, etc
To see all the modules in recon-ng, we can simply enter “search marketplace”.
[recon][default] > search marketplace


Step #3: API (Application Programming Interface) Keys
recon-ng is capable of using a number of online resources such as Facebook, Twitter, Instagram, Google, Bing, LinkedIn and others. To use these resources, you simply need to obtain an API key and enter it.
So, once we obtained our Shodan API key, we simply need to add that key to use Shodan for reconnaissance.
[recon][default] > keys add shodan_api 123456
[recon][default] > keys list

Now, you are ready to use Shodan’s API to connect to Shodan and do your recon searches there.
Step #4: Profiler Module
recon-ng has numerous modules for finding information available on the web. Let’s take a look at just one module here, profiler (we’ll examine others in future tutorials).


Let’s assume that you are looking for a person who uses the profile name “Occupytheweb” and want to find out whether they use that same profile on other sites. recon-ng has a module for that!
It’s called the ‘profiler’ and we can find it in the recon-ng marketplace. To install this module, simply enter;
[recon][default] >marketplace install profiler

Next, to use this module, you must load it.
[recon][default][profiler] >modules load profiler
To learn more about this module, then enter;
[recon][default] [profiler]> info

We can see in the screenshot above that it takes a profile name and searches for that profile name through numerous web sites for that same name.
To begin our search, we simply enter the profile we are looking for;
[recon][default][profiler] > options set SOURCE occupytheweb

and then enter;
[recon][default] [profiler]> run


The profiler module then searches through numerous web sites seeking matches of this profile name. In this case, it found 21 matches! It should be pointed out these may not all be the same person, but simply the same profile name.
In my earlier tutorial on finding information on Twitter using twint, we searched the tweets of the smarmy second-term U.S. congressman from Florida, Matt Gaetz. Let’s try a similar search for the sycophantic Mr. Gaetz with profiler and see whether he has other accounts under his same twitter profile, mattgaetz.
Let’s set the source to “mattgaetz”.
[recon][default][profiler] > options set SOURCE mattgaetz

Then, enter “run”.
[recon][default][profiler] >run
Within seconds, recon-ng returns numerous accounts using this same profile.


Next, of course, we can go to those accounts to find more information on the target of our recon.
When we go to account of Matt Gaetz on flickr (flickr.com/photos/mattgaetz) we see photos of Mr. Gaetz impersonating a public servant for his 0 followers.

Summary
recon-ng is an excellent tool for automating the extraction of the cornucopia of information and intelligence from the web. In this case, we used the profiler module to look for the use of the same profile in numerous websites. This can be an effective way to find accounts where the target may reveal additional information about themselves that can be useful in social engineering attacks and forensic investigations.
For more on recon-ng, check out the tutorial on determining the anti-virus of the target using recon-ng here.