Welcome back, my aspiring RF hackers!
Among the multitude of radio signals swirling around us everyday are the mobile telephone signals that all of us have become so dependent upon. Mobile networks use several different technologies including GSM, CDMA, TDMA, 4G, LTE, 5G and many others.
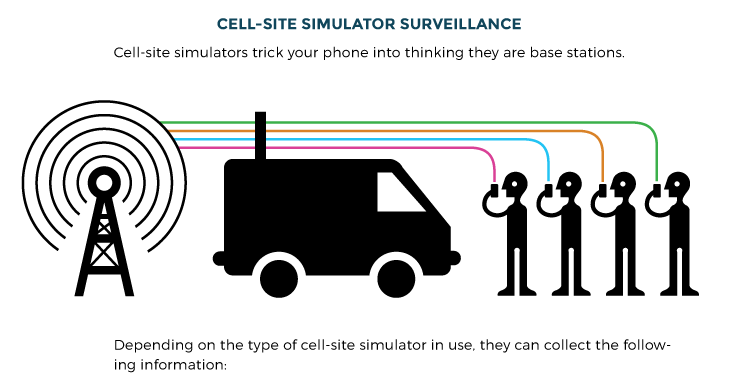
For almost two decades now, law enforcement around the world have been using IMSI catchers (aka Stingrays) to eavesdrop and track suspects. These IMSI catchers act as portable cellular towers and sniff the cellular traffic, identify the IMSI, track the IMSI geographically, intercept and read metadata/Internet traffic, and eavesdrop on voice conversations.

Commercially available IMSI catchers go by the name “Stingray”and others. These stingrays are supposed to be only available to law enforcement but they have made their way into the hands of others. Many have complained about the civil liberties aspects of allowing law enforcement and oppressive governments using these devices to track and listen to targets but this has not stopped their use. The Electronic Frontier Foundation has called the devices “an unconstitutional, all-you-can-eat data buffet.”
Generally, these devices are estimated to cost between $50,00-$200,000 from electronics companies such as Harris. It is my hypothesis that if the cost were to drop to about $2000 and be available to anyone with a bit of technical knowledge, they would be quickly outlawed. That is our goal in this series; develop a low-cost Stingray.
Technically, a Stingray is really a IMSI catcher with a cellular base station. In our tutorial here, we will implement the first stage of the cellular man-in-the-middle attack; the capture of the IMSI. Here we will only be able to capture the IMSI of 2G and 3G cellphones. That may seem limiting if you are in the US or Western Europe, but recent data indicates about 46% of current phones around the world are using these two older technologies. In future tutorials, we will work on 4G, LTE and 5G technologies.
Once we have are able to capture the IMSI, we have begun the process of building our Stingray. The next step is building a cellular base station. Cellular base stations are prohibitively expensive but an opensource project called OpenBTS has developed a base station for less than $1000.
GSM Networks and IMSI numbers
GSM is standard developed by the European Telecommunications Standards Institute (ETSI) and first deployed in Finland (home of Nokia and Linus Torvalds) in December 1991. It rapidly became the European standard for cell phone transmission and achieved 90% penetration of the global mobile network by the 21st century.
One of the security vulnerabilities of GSM networks is the lack of mutual authentication. The GSM handset does not authenticate the base station prior to accessing the network. In this tutorial, we will use this security vulnerability to sniff and acquire the handset’s IMSI.

The IMSI number is a globally unique number that identifies the user. It is up to 15 digits and includes;
MCC – Mobile Country Code. 3 decimals places and identifies the country of the mobile device owner
MNC – Mobile Network Code. 2 decimal places and identifies the carrier network
MSIN – Mobile Subscriber Number 10 decimal places and identifies the subscriber

The IMSI number is held within the SIM card in the mobile phone and identifies the country, the carrier, and the user. With this information, the person sniffing this traffic can identify and locate the phone user at a minimum and potentially intercept and spoof the user’s traffic.
Let’s see how we can harvest that information from 2G and 3G mobile networks with our RTL-SDR dongle and a few pieces of software.
Step #1: Install New Software in Kali
For this tutorial, we will be using Kali and several new pieces of software. Let’s begin with gr-gsm. Gr-gsm is a set of tools for receiving GSM transmissions, which works with any software radio (SDR) hardware capable of receiving a GSM signal.
Although gr-gsm is available in the Kali repository, I found that building it from the source code works better. To install gr-gsm, first install the dependencies;
kali > sudo apt-get install -y cmake autoconf libtool pkg-config build-essential python-docutils libcppunit-dev swig doxygen liblog4cpp5-dev gnuradio-dev gr-osmosdr libosmocore-dev liborc-0.4-dev swig
Then, clone gr-gsm from the github repository.
kali > sudo git clone https://git.osmocom.org/gr-gsm

Then follow the next few steps to build the application.
cd gr-gsm mkdir build cd build cmake .. make -j 4 sudo make install sudo ldconfig
Lastly, we need change the PYTHONPATH environment variable
kali > sudo echo ‘export PYTHONPATH=/usr/local/lib/python3/dist-packages/:$PYTHONPATH’ >> ~/.bashrc

Now you are ready to install kalibrate-rtl from the Kali repository.
kali > sudo apt install kalibrate-rtl

Next, clone the IMSI-catcher from github.

Step #2: Find the Frequencies the Base Stations are Operating on
The next step is to find the base stations in your area and the frequency they are operating on. For this action, we can use kalibrate.
Let’s begin by examining the kalibrate help screen.
kali > kal -h

As you can see above, kal simply needs -s to scan followed by the technology such as GSM850, GSM-R, GSM900, EGSM, DCS or PCS. In addition, we can specify the gain with the-g option. Since GSM850 is common in North and South America, I’ll scan for it with a gain of 45db.
kali > sudo kal -s GSM850 -g 45

As you can see above, there were 2 base stations within range at 889.0Mhz and 890.0Mhz. These fall within the receiving range of my RTL-SDR dongle (24-1766Mhz).
Step #3: Tune grgsm to the Base Station Frequency
Now we need to turn the grgsm to the frequency of the nearby base station. Navigate to the gr-gsm directory and enter;
kali > grgsm_livemon -f 889.0M -g 45

This should open the gr-gsm GUI. If you need, you can adjust the frequency with the slide bar.
Where 889.0M is the frequency we want to “listen” on (make certain to substitute the frequency found at your locale with kalibrate) and -g 45 is the gain rate.

Step #4: Start IMSI Catcher
Finally, let’s start the IMSI catcher.
Navigate to the IMSI-catcher directory and then execute the catcher with the -s option (scan).
kali > cd IMSI-catcher
kali > sudo python simple_IMSI-catcher.py -s

As I live in a remote location in the Rocky Mountains of the US where few people are still using 2G and 3G GSM phones, my IMSI-catcher does not pick up any IMSI’s. In addition, our hardware–the inexpensive rtl-sdr– is limited to 1766Mhz in the upper range and several GSM phone technologies operate outside that band at higher frequencies.
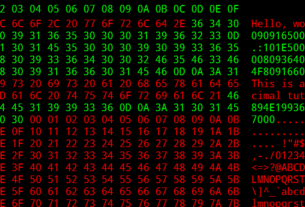
On the other hand, another user in Europe where GSM is the standard and still has many 2G and 3G phones, captured numerous IMSI’s along with operator and cell ID as seen below.

Summary
Even with an inexpensive RTL-SDR, we can pick up and sniff 2G and 3G cellular traffic complete with the IMSI. Since the IMSI is embedded in the SD card, there is little chance of spoofing the IMSI without more expensive equipment. On the other hand, IMSI’s are collected by a number of mobile applications and these IMSI’s can be used to correlate with that data to identify the user. Of course, law enforcement can get a subpoena for the user’s IMSI and identify the user with this data.
As we progress through this series, we will be adding more sophisticated software and hardware as we develop an inexpensive Stingray for intercepting mobile communications.