Welcome back, my aspiring cyber warriors!
At the beginning of the cyberwar between Russia and Ukraine, Hackers-Arise, the IT Army of Ukraine and over 17,000 hackers around the world (this is the Russian estimate. we believe it is much higher) set out to make Russia’s digital assets unavailable. In this way, the Russians would not be able communicate via their websites, operate their military, or run their commercial operations. We targeted the following websites below within Russia. This is an example of the classic Distributed Denial of Service (DDoS) attacks.

One of things we did a little differently was to use UDP packets rather than TCP packets. UDP attacks can be much more effective for DDoS, as we will see. According to DDoS protection companies such as Radware and Akamai, this was the most common type of DDoS attack in 2023 accounting for nearly 2/3 of all attacks.
A UDP flood attack is a type of Distributed Denial of Service (DDoS) attack where the attacker overwhelms a target server with User Datagram Protocol (UDP) packets. The aim is to either consume network resources to the point where the target can no longer handle legitimate traffic or to exploit vulnerabilities in the UDP protocol to cause the server to respond with even more traffic, amplifying the attack.
Here’s a bit more detail about how it works and its impact:
Understanding UDP
UDP Characteristics: UDP is a connectionless protocol, which means it doesn’t require a handshake to set up a connection before data is sent. This makes UDP faster than TCP (Transmission Control Protocol), but less reliable in terms of ensuring data integrity and delivery.
No Connection Verification: Because there’s no connection verification in UDP, an attacker can send packets to random ports on a target server with a spoofed IP address (the source IP address is faked).
Mechanism of UDP Flood Attack
High Volume of Requests: The attacker sends a large number of UDP packets to random ports on the target server.
Server Responses: For each packet, the server checks for an application listening at that port. When no application is found, the server responds with a ‘Destination Unreachable’ packet.
Network Saturation: This flood of incoming UDP packets and outgoing ‘Destination Unreachable’ responses can saturate the network bandwidth and resources of the server, making it incapable of processing legitimate requests.
Amplification: Some UDP flood attacks use amplification techniques, where the attacker sends a packet to a third-party server (like a DNS server), forging the sender’s IP address to that of the victim. The third-party server then sends a large response to the victim, amplifying the amount of data directed at the target.
In addition, in UDP flood attacks the packets can be fragmented or otherwise malformed resulting in an even faster packets-per-second rate and cause some network cards to fail.
We can duplicate this attack with our trusty Kali and the tool known as the “packet-crafting” tool for its versatility, hping3.
Step #1: How hping3 works
hping3 is a tremendous and simple tool for network and port scanning. One of its beauties is its ability to create just about any type of packet. Most technologies that interact with the internet create standard packets that are compliant with the RFC’s that govern the Internet. As hackers, we are not limited by those RFC’s.
hping3’s ability to create just about any type of packets can be especially useful in crafting an attack to get past security devices such as IDS’s and firewall. It can also be an excellent DDoS too.
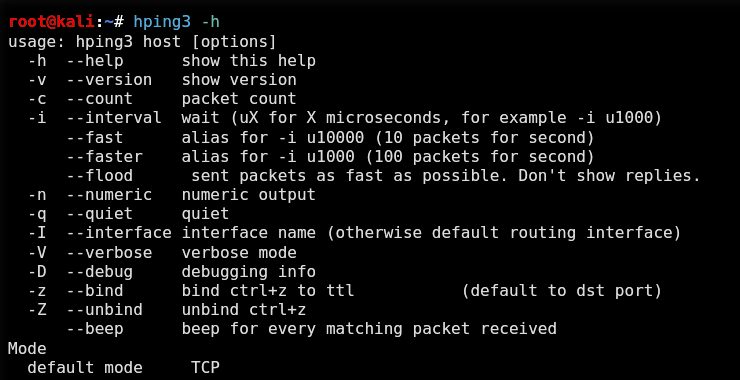
Let’s begin by looking at the help screen for hping3.
kali > hping3 -h



Step #2: Standard Port Scan
Let’s begin by doing a standard port scan with hping3. Like nmap, hping3 is able to determine whether a port is open on the target server but the results are a little more difficult to interpret.
We can do a port scan with hping3 by simply using the -S option and IP address of the target such as;
kali > sudo hping3 -S 192.168.107.150

Notice that hping3, without any other options simple scan port 0 (sport=0) and the target response is flags=RA. When the packet responds with the R (reset) flag, that means the port is closed.
To scan a particular port with hping3, you can append the scan command with a -p and the port number such as -p 80.
kali > sudo hping3 -S 192.168.107.150 -p 80

Step #3: UDP Flood with fragmented packet s and spoofed IP address
Now, to use hping3 as an effective DDoS tool, we need to send a flood of fragmented UDP packets from a spoofed IP address. We do this with the following command;
kali> sudo hping3 -S –udp –flood -f –spoof 192.168.107.101 192.168.107.152

Where:
hping3 is the command
-S option means scan
–udp means send UDP packets
-f option means fragment the packets
–spoof means use the following IP address as the sender IP
Summary
Despite years of technological security advances in DDoS protection, a simple tool such as hping3 with a little savvy and knowledge can still have devastating effects on the availability of websites and services. When a tool like hping3 is delivered to thousands are even millions of IoT devices and targeted to one IP address, there is little that can done to stop it’s devastating effects.