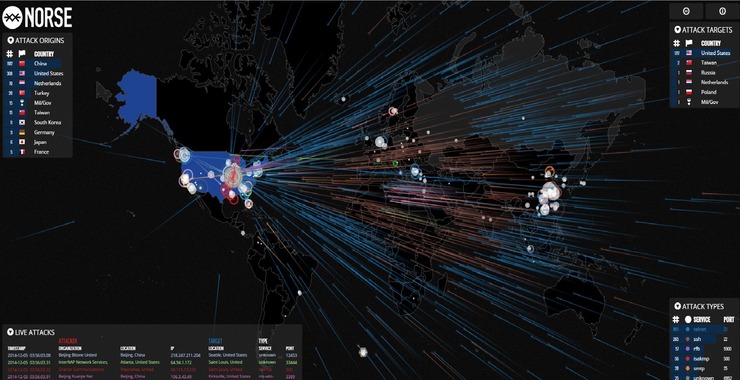
Welcome back, my aspiring cyberwarriors!
As you well know, the Distributed Denial of Service (DDoS) attack is one of simplest attacks. It is simply brute-force packet jamming a network to render it useless or nearly useless. When its done with just a few nodes it can be easily thwarted by a number techniques such as load balancing, black hole routing, rate limiting and many newer intelligent systems techniques. The impact is minimal.

Massive Numbers of Compromised IoT Devices
When it done with a massive number of nodes, nearly everything is vulnerable. Millions of IoT devices have been compromised due to VERY lax security for these devices. Any IoT device such cameras, security systems, and baby monitors can become an attack vector used to create a massive attack that would crush any network. Nothing would be safe. This is a vastly overlooked issue in our time of IoT devices. We may be ready to pay a heavy price for such oversight. This keeps me awake at night and I think it should keep you awake too!
New DDoS Techniques
In addition, new techniques have made DDoS even more deadly. Distributed Denial of Service (DDoS) attacks have become increasingly sophisticated, with attackers continually developing new techniques to circumvent traditional defense mechanisms. Some of the latest DDoS attack techniques and trends include:
Multi-Vector Attacks: Modern DDoS attacks often combine several attack vectors at once, making them more difficult to defend against. Attackers may simultaneously use volumetric attacks, protocol attacks, and application layer attacks to overwhelm systems in different ways.
Amplification Techniques: Attackers continue to use amplification to increase the volume of their attacks. They exploit the communication protocols that respond with more data than they receive (like DNS, NTP, SSDP, CLDAP, and memcached) to send small queries that provoke much larger responses to the targeted system.
Burst Attacks: These are short-duration attacks that come in quick bursts, intended to disrupt service without triggering DDoS mitigation which often requires a sustained attack before it activates. Burst attacks can be particularly damaging for services that require high availability.
IoT Botnets: Insecure Internet of Things (IoT) devices are increasingly being co-opted into botnets. These botnets are used to mount large-scale DDoS attacks, as seen with the Mirai botnet and its variants. Because there are so many IoT devices with poor security, they provide a vast attack surface for malicious actors.
AI and Machine Learning: Some attackers are beginning to use AI and machine learning to automate the process of finding and exploiting vulnerabilities, as well as to adapt in real-time to defensive measures, making their attacks more effective and persistent.
SSL/TLS Exploits: Attacks are increasingly targeting the encrypted traffic of SSL/TLS protocols. These attacks require more processing power to mitigate because the defensive systems must decrypt the incoming data to inspect it, which can be resource-intensive.
Direct Path Attacks: These attacks bypass common DDoS protection by targeting the IP address of individual network interfaces. This is particularly a risk for cloud services, where the IP address can be exposed through various methods.
Ransom DDoS (RDoS): Here, attackers threaten to launch a DDoS attack or start a small-scale attack unless a ransom is paid. The fear of a potential large-scale DDoS can pressure organizations into paying.
Supply Chain and Dependency Attacks: Attackers target less-secure elements of an organization’s supply chain, including third-party services and APIs, understanding that disrupting these can have knock-on effects on the primary target.
State-Sponsored Attacks: Some of the most sophisticated DDoS attacks are suspected to be carried out by state-sponsored actors, often as part of broader cyberwarfare strategies. These attacks may target critical infrastructure or be used as a distraction for other types of cyber intrusions.
The Greatest DDoS Attacks in History
To better understand the incredible weight that a massive DDoS attack might have, let’s consider the greatest DDoS attacks in history.
BBC – December 2015
The BBC’s entire domain, including its website and iPlayer service, was brought down by an attack that was believed to be around 600 Gbps.
Krebs on Security – September 2016
Security journalist Brian Krebs’ website was hit by a DDoS attack that peaked at 620 Gbps. It was later found that this attack was also carried out by the Mirai botnet.
Spamhaus – March 2013:
Spamhaus, a non-profit organization that fights spam, was targeted by an attack that reached 300 Gbps. The attackers used a DNS reflection technique, which was, at the time, one of the largest-known DDoS attacks.
GitHub – February 2018:
GitHub was hit by a DDoS attack that peaked at 1.35 Tbps. This attack was notable because it was powered by an amplification attack exploiting memcached servers, which returned large volumes of data to the targeted IP address in response to small queries.
Dyn – October 2016
A major attack targeted the DNS provider Dyn and peaked at an estimated 1.2 Tbps. This attack caused major internet platforms and services to be unavailable to large swathes of users in Europe and North America. The attack was attributed to a large network of IoT devices (such as cameras and home routers) that had been hijacked by the Mirai botnet.
Google – September 2017:
Google revealed that in 2017 it had defended against a DDoS attack that peaked at 2.54 Tbps, which at the time of the revelation made it the largest DDoS attack in history, surpassing the attack against AWS.
Amazon Web Services (AWS) – February 2020:
AWS reported a DDoS attack that peaked at 2.3 terabits per second (Tbps), the largest ever reported at the time. The attack was a Connection-less Lightweight Directory Access Protocol (CLDAP) reflection-based attack, a type of attack that exploits a vulnerability in CLDAP servers to amplify the amount of data sent to the victim’s network.
The Cyberwar DDoS Attack Against Russia February-March 2022
Although no one knows for certain the precise number of packets directed at Russia at the outset of the war, Russia stated that this was the largest DDoS attack in their history.
Read what Bleeping Computer reported on the attack below.
The most powerful of these DDoS attacks was recorded by Rostelecom–the Russian Telecom giant–was 760 GB/sec, almost twice as big as the most potent attack of the previous year, while also the longest, lasting nearly three months.
We, at Hackers-Arise, the IT Army of Ukraine and hackers across the planet participated in the largest DDoS attack in history. For nearly three months, we crushed Russia’s major institutions such as SberBank, the Moscow Stock Exchange, the distribution of alcoholic beverages throughout Russia (heaven forbid! A Russia without vodka!) and many other major institutions.
Russia estimates that 17,000 IP addresses attacked them and they have vowed to exact revenge on all 17,000 of us. Imagine what would have happened if someone had used millions of IoT devices?
Summary
These figures for each of these attacks represent the peak sizes as reported, but it’s worth noting that the actual impact of a DDoS attack is not solely determined by its size. The sophistication of the attack, the defenses in place, and the duration of the attack are all critical factors that influence the overall effect.
I believe we are on the cusp of massive DDoS attacks from IoT devices that will cripple major institutions around the globe.
What are you doing to prepare?