Welcome back, my aspiring cyberwarriors!
SCADA hacking and security is different from traditional hacking in numerous ways. For a review of how SCADA hacking is different, check out my article here. One of the key ways that SCADA Hacking and Security is different is that the security professional is protecting the process and not necessarily the data as in traditional systems. In SCADA hacking is may be possible to do serious damage to a SCADA/ICS system by just disrupting the process. This may include a DoS attack or something as sophisticated as the Stuxnet attack where the NSA developed malware not to destroy or explode the system, but simply to get it to operate in a way that was different that is was designed to operate. In the case of Stuxnet, it changed the rotational speed of the centrifuges used to enrich uranium. This was much more stealthy and effective than blowing up the facility.
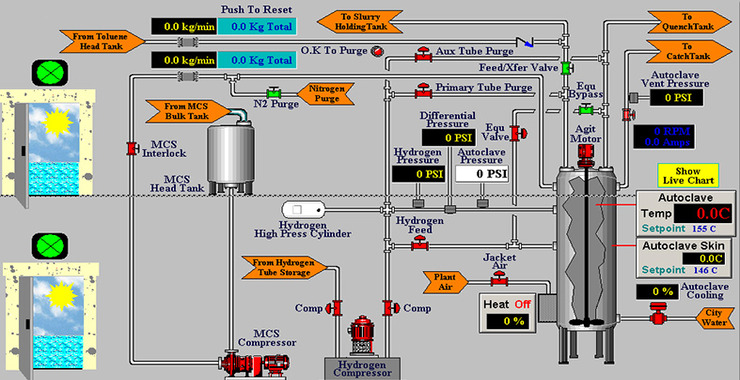
SCADA/ICS systems are designed to be carefully and precisely orchestrated toward a particular purpose. For instance, the PLC’s are designed to precisely open a valve when the pressure hits a particular level. If the opens earlier or later, it can have destructive and disruptive consequences. The pipe or plant may blow up or the output can be spoiled or tainted. In either case, the process is disrupted. Remember, SCADA/ICS security is ALL about protecting the process.

Take a look at the gif above to get an idea of how these systems are controlled and operated.
In the past, most SCADA/ICS hackers focused upon denial of service attacks or taking control of the system. In the Stuxnet attack, the worm took control of the PLC’s and subtly changed the RPM’s of the centifuges. In the BlackEnergy3 attack in 2014 against Ukraine’s primary energy distribution system, the Russians took control of breakers on the electricity grid and turned off the power. In my attack on the Schneider Electric building control system, I took root access of the entire system.
I am proposing a different and unique way of disrupting these systems. Many of the systems have a TCP/IP connection so that someone, somewhere can monitor and maintain these systems. These connections very often accept packets without authentication to the PLC’s. These packets are capable of reading, and in some cases, writing values to the coils and memory locations on the PLC’s.

By changing whether a coil (an ON/OFF switch) is on or off can have disruptive consequences that are hard to predict. Obviously, if that coil controls a pressure valve, the system can be destroyed. If we change the memory values within the PLC, it can change, for instance, how long the valve is open or closed or the value (temperature or pressure) the valve opens or closes. This also can have very disruptive consequences.
In our attacks against the Russian industrial infrastructure, this is exactly what we did. Journalists and others asked us “what were the consequences”. Our answer was “we don’t know, but the consequences were not good”. What we can say for certain is that many of these facilities started on fire, blew up or were disrupted in their process. In each case, it hampered Russia’s ability to produce war materiel and keep their industrial economy running smoothly.

Summary
I am proposing that sending random, unauthenticated packets into an industrial facility can be a new way of conducting cyberwar against industrial facilities. This type of attack has unknown, precise consequences but any change is sub-optimal since these facilities are carefully choreographed systems.
For more on SCADA/ICS Hacking and Security, become a Subscriber and attend our next SCADA/ICS Hacking and Security training.