Welcome back, my aspiring cyberwarriors!
Recently, security researchers discovered a critical vulnerability in the Windows IPv6 packet processing system, which was subsequently assigned the identifier CVE-2024-38063. This vulnerability can lead to a denial of service, as well as remote code execution (RCE) via specially crafted IPv6 packets.

Unlike many vulnerabilities that require user interaction or specific software to be installed, CVE-2024-38063 can potentially be exploited remotely with no user interaction, making it particularly dangerous. In this guide, we’ll delve into the technical details of CVE-2024-38063 and explore how it can be exploited.
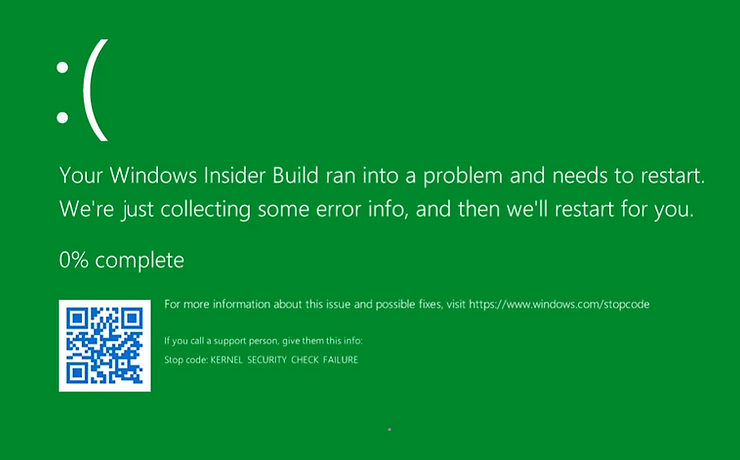
Vulnerability Details
To understand CVE-2024-38063, we need to delve into the intricacies of how Windows handles IPv6 packets. The vulnerability arises from a complex interplay of packet processing mechanisms within the Windows TCP/IP stack.
Windows employs a technique called packet coalescing, where it combines multiple IP packets for batch processing. This is generally done to improve network performance. When processing these coalesced packets, Windows first handles the extension headers for each packet before moving on to the packet data itself.
During this process, Windows creates a linked list of packet objects. Each of these objects contains what’s called a NET_BUFFER, which holds the actual packet data, along with a current-offset field. This field indicates how far the packet has been parsed.
The vulnerability comes into play when processing a specific type of extension header called “destination options.” If an error occurs while parsing this header, it triggers an error handling function. This function is supposed to “revert” the buffered packet data to its starting point and reset the current-offset field to zero. However, there’s a crucial flaw in this process: only the first packet in the linked list gets marked as having an error.
This is where things get interesting. Despite this error, the system continues to parse extension headers of other packets in the list, even if they’ve been “reverted.” As a result, the system ends up processing unexpected data. Instead of pointing to the extension headers as it should, the packet data now points to the IPv6 header. Moreover, the offset field is zero instead of its expected value (typically 0x28).
The real trouble starts when the system processes fragment extension headers. To calculate the length of non-header data, it subtracts a fixed value (0x30) from the current offset. But remember, our offset is now incorrectly set to zero. This subtraction causes an underflow, resulting in a very large length value.
In certain timeout scenarios, this large length value gets used in 16-bit calculations. This causes an integer overflow, which ultimately leads to a buffer overflow when copying data. It’s this buffer overflow that opens the door for potential DoS and arbitrary code execution.
Exploitation Strategy
The exploitation strategy takes advantage of the “Ipv6pReceiveFragment” function and involves the following steps:
Send malformed destination options to trigger “IppSendError”.
Follow with a fragment packet.
Exploit packet coalescing to reset data and offset of the second packet.
Cause an underflow in “Ipv6pReceiveFragment”, creating a reassembly object with a high 16-bit fragment data length.
Wait for 1 minute to trigger “Ipv6pReassemblyTimeout”.
Cause an integer overflow in the buffer size calculation, leading to a heap-based buffer overflow.
Exploitation
For this guide, we’ll be using a Python script that implements the CVE-2024-38063 exploit developed by ynwarcs.
Step 1: Set Up the Environment
First, we need to download proof-of-concept script from github.com
kali> git clone https://github.com/ynwarcs/CVE-2024-38063.git
Next, navigate to the new directory, script.
kali> cd script
Then, install scapy using pip3.
kali> pip3 install scapy
Step 2: Prepare the Script
Open the script and modify the following fields:
iface: Specify the network interface to use (e.g., “eth0” or “wlan0” on Linux).
ip_addr: Set the IPv6 address of the target system.
num_tries and num_batches: Adjust these to control the number of packet batches sent.
mac_addr: Leave empty unless Scapy can’t find the MAC address automatically.
Here’s an example of how your configured script might look:
iface=’eth0′
ip_addr=’1234:1234:1234′
mac_addr=”
num_tries=20
num_batches=20
Step 3: Run the Exploit
The script will send multiple packets to exploit the vulnerability, including an IPv6 packet with a malformed “destination options” extension header. It will also send an IPv6 fragment # 1, potentially concatenated with the first packet, followed by an IPv6 fragment # 2 (with the same ID) to complete the second fragment.
The script attempts to trigger multiple corruptions to increase the chance of a crash. Wait for about a minute to allow “Ipv6pReassemblyTimeout” to be triggered. As a result, the system will be disrupted.
The exploit will not work under all circumstances, as is the case with any exploit.
For troubleshooting, follow these steps:
First, ensure IPv6 connectivity with “ping -6 {ipv6_address}” from the host PC. Also, check whether your ISP supports IPv6.
If Scapy reports “Mac address to reach destination not found,” resolve MAC address issues by manually finding the target’s MAC address.
You can use Wireshark or Scapy to obtain the MAC address and then add it to the “mac_addr” field in the script.
Finally, address packet coalescing issues by modifying network adapter settings such as “Packet Coalescing” and “Interrupt Moderation”.
Summary
CVE-2024-38063 is a serious vulnerability that affects Windows systems with IPv6 enabled. This article explains the details of a vulnerability and presents a proof of concept (PoC) that can cause a denial of service on unpatched Windows systems running IPv6. Its discovery underscores the importance of ongoing security research and the need for prompt patching. Patch your system immediately!