Welcome back, my aspiring cyberwarriors!
The landscape of digital privacy continues to evolve as surveillance capabilities expand globally. Our digital footprints are continuously tracked, analyzed, and leveraged by various entities. While traditional privacy tools focus on encrypting the content of communications, they often overlook a significant vulnerability: metadata. This “data about your data” reveals communication patterns, including who you’re communicating with, when you’re online, and behavioral patterns in your digital activities. As Edward Snowden’s disclosures demonstrated, extensive metadata collection can provide detailed profiles of user activities even without access to communication content.
Many individuals employ Virtual Private Networks (VPNs) as an initial defense against surveillance. However, standard VPNs provide only a single protection layer, creating a potential vulnerability. If the VPN provider experiences a security breach or monetizes user data (as observed with many free VPN services), user privacy becomes compromised. Additionally, conventional VPNs can access both user identity and browsing history, creating a centralized repository of sensitive information.
Comprehensive digital privacy protection requires approaches that extend beyond basic encryption methods. NymVPN offers an alternative that combines a decentralized VPN with a mix network architecture.

NymVPN is an open-source privacy solution that launched on March 13, 2025, at London’s Frontline Club, so it is brand new! Developed to address the claim that “digital privacy is broken,” NymVPN fixes key flaws in existing tools by protecting both message content and metadata that could expose user behavior.
Key features of NymVPN include:
-
Dual Protection Modes: Options include a Fast mode for standard browsing and an Anonymous mode for enhanced privacy requirements.
-
Decentralized Network: The system utilizes over 600 independently operated nodes across approximately 60 countries, reducing single points of failure.
-
Metadata Protection: The mixnet technology addresses patterns in communication metadata beyond standard content encryption.
-
Payment Unlinkability: The zk-nyms cryptographic system prevents payment information from being associated with online activities.
Understanding NymVPN’s Dual Protection Modes
NymVPN offers two distinct modes of operation, each designed for different privacy needs and use cases.
Fast Mode
Fast Mode employs a decentralized 2-hop architecture using the WireGuard protocol. Unlike standard VPNs that route traffic through a single server (often under singular ownership), NymVPN’s Fast Mode transmits data through two independent nodes operated by separate entities.
The WireGuard foundation supports efficient performance while maintaining security, making Fast Mode suitable for common activities such as web browsing, streaming, and downloading. Connections are secured with multiple encryption layers, including cryptographic implementations such as AES-128, ChaCha20-Poly1305, and BLAKE2.
Anonymous Mode
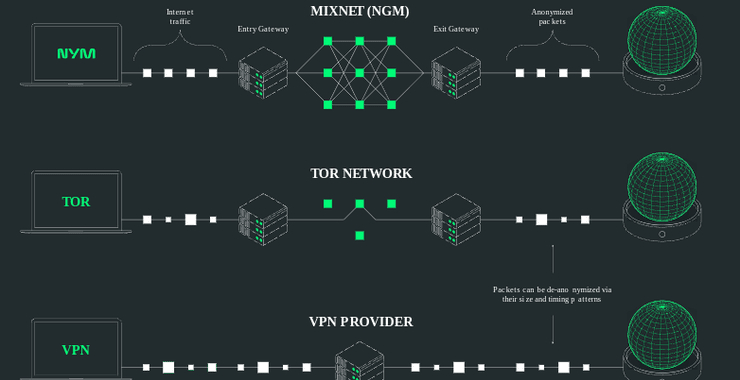
For situations requiring higher privacy standards, NymVPN’s Anonymous Mode activates the Noise Generating Mixnet (NGM). This system routes traffic through a 5-hop path, with each hop adding an additional protection layer.
-
Multi-server routing: Connections are directed through five independent hops, preventing any single node from linking user identity to destination.
-
Cover traffic: The network produces randomized “noise” packets indistinguishable from actual traffic, embedding real communications within artificially generated data.
-
Packet mixing: Data packets are intentionally reordered and timed differently during network transit, disrupting timing patterns that might otherwise reveal communication relationships.

Understanding zk-nyms
A critical vulnerability in many privacy tools is the payment process. Even if your online activities are protected, your subscription payment can often be linked to your identity, creating a potential privacy leak.
NymVPN addresses this issue through zk-nyms technology. This cryptographic protocol combines zero-knowledge proofs with digital signatures to provide network access without revealing identifying information.
When subscribing to NymVPN, payments (whether in fiat currency or cryptocurrency) convert to NYM tokens through market mechanisms. These tokens exchange for zk-nyms credentials, functioning as privacy-preserving proof of payment that grants network access.
How NymVPN Compares to Other Privacy Solutions
Comparing NymVPN with other privacy tools provides context for understanding its distinctive attributes.
NymVPN vs. Conventional VPNs
Unlike centralized VPN providers such as IVPN, ProtonVPN, and MullvadVPN, NymVPN operates on a decentralized model. While these conventional providers may offer multi-hop routing as an optional feature, their centralized architecture means they maintain visibility into user activities. NymVPN’s decentralized approach prevents any single entity from correlating user identity with browsing patterns.
Additionally, conventional VPNs lack community governance mechanisms. NymVPN incorporates user participation through stake delegation and feedback channels, allowing the network to develop based on user requirements rather than solely corporate objectives.
NymVPN vs. Decentralized VPNs
Other decentralized VPN services including Sentinel, Mysterium, and Orchid share similar objectives but differ in implementation. Sentinel and Mysterium currently lack multi-hop routing capabilities, potentially exposing users to correlation analysis. Orchid, despite decentralization claims, currently operates nodes through the company and partners, which affects the degree of decentralization.
Furthermore, the payment systems employed by these alternatives often create privacy vulnerabilities. Mysterium’s reliance on blockchain transactions generates public records that could potentially expose user activities. Orchid’s nanopayments system, while innovative, still creates public blockchain records that could connect users to specific nodes.
NymVPN’s zk-nyms technology provides enhanced payment privacy, preventing financial transactions from being linked to network activities.
NymVPN vs. Tor
More significantly, Tor’s packet handling methodology creates vulnerability to timing analysis. Packets in the Tor network follow a first-in, first-out sequence, potentially allowing advanced monitoring to correlate user activities. NymVPN’s mixnet actively reorders packets during transmission and introduces cover traffic, substantially reducing the effectiveness of such analysis.
Summary
As digital surveillance capabilities advance, conventional privacy tools may no longer provide sufficient protection for online activities. NymVPN represents an evolution in privacy technology, combining decentralized VPN functionality with mixnet architecture to protect both data content and the metadata patterns that can reveal user behavior.