Welcome back, aspiring cyberwarriors and OSINT investigators!
In our digital age, email addresses have become the keys to our online identities. They’re used for everything from social media accounts to financial services, making them prime targets for hackers.
The Rise of Data Breaches
The 21st century brought a huge increase in digital information. As more of our lives moved online, so did our risks. In 2013, the Yahoo breach affected 3 billion accounts, highlighting the urgent need for better tools to detect and stop data breaches.
In the following years, we saw more big breaches, like Equifax in 2017 and Marriott in 2018. Each one reminded us that our digital information was more at risk than ever.

Key Features of Mosint
Email Verification and Validation
Data Breach and Password Leak Checking
Related Emails and Domains
Pastebin Dump Scanning
Google Search Integration
DNS/IP Lookup
Services
Mosint integrates with several services to gather information. Some of these require API keys, similar to h8mail. Here’s a quick overview of the services:
ipapi.co (Public): More information about the domain
hunter.io (Public, API key required): Find related emails
emailrep.io (Public, API key required): Check for breached sites
scylla.so (Public): Database leaks
psbdmp.ws (Public, API key required): Pastebin dumps
Intelligence X (API key required): Password leaks
BreachDirectory (API key required): Password leaks
HaveIBeenPwned (API key required): Password leaks
Step #1: Install Mosint
The first step is to install mosint. Docker has made this process simple and all we need to do is the following:
Clone the repository:
kali> git clone https://github.com/alpkeskin/mosint.git
Build a docker image:
kali> cd mosint
kali> docker build -t mosint .
Step #2: Mosint Set Up
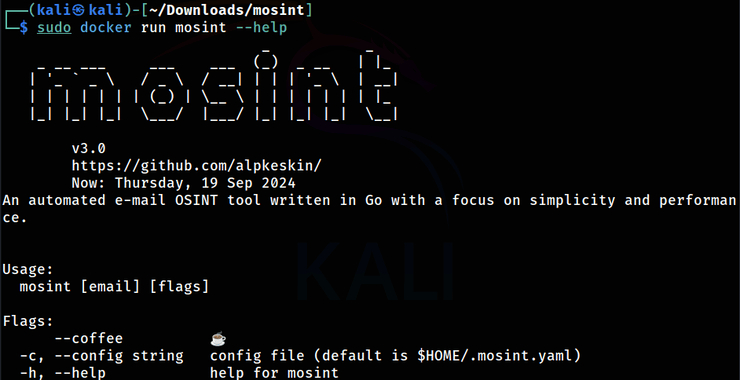
Before get started, let’s look at this tool’s help screen:
kali> docker run mosint –help

The use is straightforward:
kali> docker run mosint <target email address>
But before you start, you should add API keys for services like HaveIBeenPwned and others to get better results. There is an example-config.yaml file in the tool’s directory. For default use, simply rename this file to .mosint.yaml and place it in your home directory
Step #3: Search For Email Addresses
Let’s try using mosint to find information about a Russian email address, maria.shalina@lenta.com
kali > sudo docker run mosint maria.shalina@lenta.com

In the screenshot, mosint has identified multiple locations where this email address appears and identified the IP and location (Moscow).

As you can see below, mosint has identified numerous pastebin dumps where this email appears.


As a result of the scan, we got valuable information about the email address, but it’s worth noting that this scan was performed without integration through the API with premium services such as haveibeenpwned.com – I’ll leave it to you.
Summary
Mosint is a powerful addition to the OSINT investigator’s toolkit. While it shares some similarities with h8mail, its unique features and Go-based architecture make it a compelling alternative or complementary tool. The integration of Google search, DNS lookups, JSON output and Pastebin dumps provides investigators with a broader range of data and more flexible reporting options.
When searching for an individual by email address, mosint can be a powerful tool to find key information including password data dumps, web sites, and geo-location.