In this tutorial, we will be setting up a SCADA/ICS Honeypot. As you know, a honeypot is a computer system that looks and acts like a vulnerable system. This particular honeypot is on an Ubuntu system with several SCADA protocols including modbus.

Honeypots can be used to study attackers or divert them from more valuable resources. This particular Honeypot was developed by Honeynet Project (www.honeynet.org) and is among the most sophisticated SCADA honeypots yet developed. It is a low interaction honeypot that changes the MAC address of its adapters, so that attackers cannot easily fingerprint it. As we will see in this lab, it looks and acts nearly identically to an actual SCADA/ICS system, including slow response times like an industrial system under heavy load.
To start, you will need an Ubuntu 12 or later operating system. I have created a user “honey” with a password “honey”, but of course, you can create any user/password you like.
Step #1 Install the necessary libraries
The first step is to install the necessary libraries and dependencies.
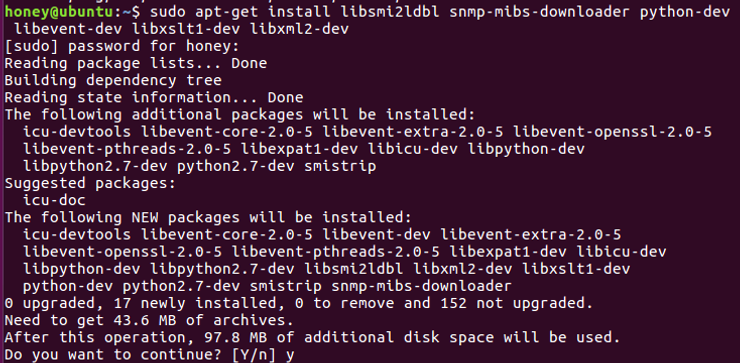
ubuntu > sudo apt-get install libsmi2ldbl snmp-mibs-downloader python-dev libevent-dev libxslt1-dev libxml2-dev
Step #2 Install Python-pip package management system
In this step, we need to download the pip package management system
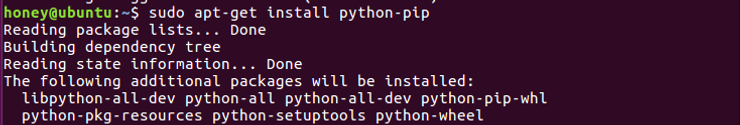
ubuntu>sudo apt-get install python-pip
Step #3 Install MySQL and Dependencies
Next, we need to install the open source database management system, MySQL and its dependencies.
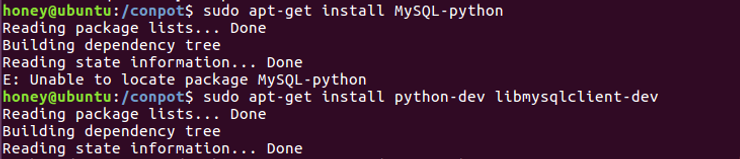
ubuntu>sudo apt-get install python-dev libmysqlclient-dev
ubuntu> sudo pip install MySQL-python
Step #4 Install Conpot
In this step, we download and install the SCADA honeypot system, conpot, using pip.
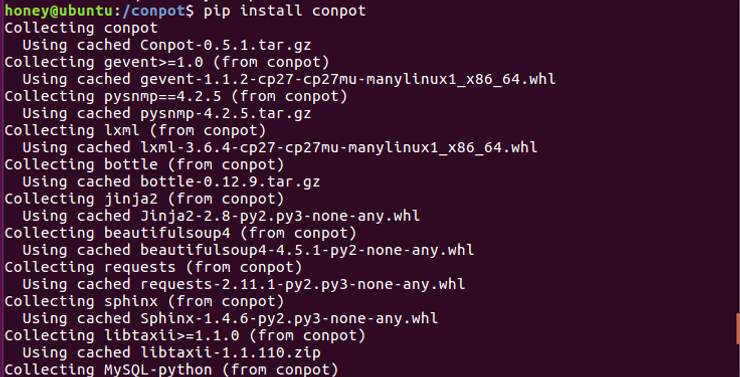
ubuntu>sudo pip install conpot
Step #5 Run conpot
Next, we need to run the conpot system. Conpot comes with four different templates to replicate different SCADA systems. Here, we will use the default template that replicates a Siemens SIMATIC S7-200.
ubuntu>sudo conpot –template default
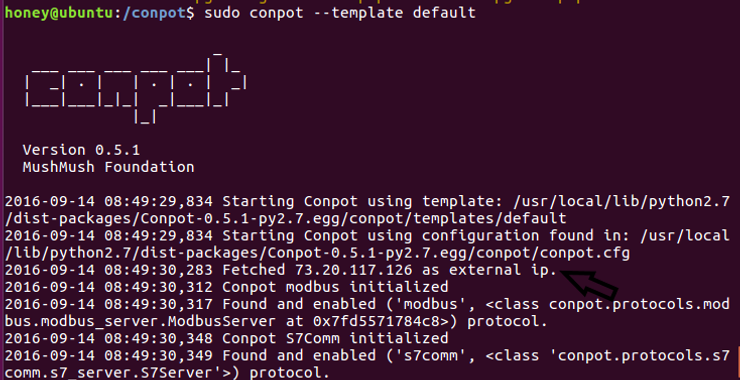
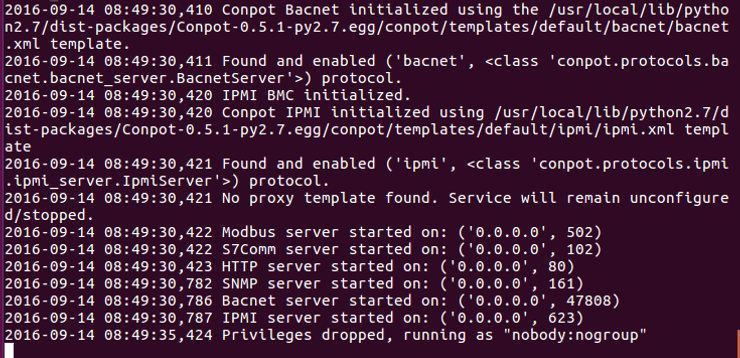
As you can see, the honeypot has been started and used an external IP address of 73.20.117.126.
In a future tutorial in this series, we will test to see what it looks like to an outside attacker to gauge its authenticity.





