Introduction
One of the most crucial activities involved in securing SCADA/ICS systems is the initial Risk Assessment. Risk assessment is considered one of the industry’s Best Practices. If you presently work in information security, you are probably aware that risk assessment can be slippery and nebulous concept. Identifying and quantifying risk in any information technology security field is problematic. It is even more so in the field SCADA/ICS security.

In the context of SCADA, risk is defined as the probability of a given threat source exploiting a vulnerability multiplied by the impact.
R = tvx
Where:
t is the threat
v is the vulnerability
x is the impact or consequences
So, for instance, if we have a 10% chance of a $1,000,000 loss, the risk is $100,000 (.10 x 1,000,000). The big problem of assessing risk in SCADA/ICS is that the number of security events is so limited (due to under
reporting of even the limited number of events. No one in the industry wants to report a breach of the are not required to) that it is difficult to assess the probabilities of events. At the same time, the potential impact could be catastrophic (the risk of a hacked PLC controlling a pressure valve in a nuclear power plant or petroleum refinery could involve tens of billions of dollars ($) impact and many lives).
The process of evaluating the risk in SCADA/ICS is similar to other IT systems, but the outcome of such an analysis is more uncertain. Even with that having been said, risk assessment in SCADA/ICS systems is essential in assisting managers and engineers in the development of adequate and effective security policies
Risk Assessment in SCADA/ICS
In this article, I want to lay out the basic outline of risk assessment for SCADA/ICS systems and then we will examine some specific programs and frameworks to assess this risk.
Risk assessment can answer 3 critical questions for us;
(1) What can go wrong?
(2) What is the likelihood?
(3) What are the consequences?
The SCADA/ICS Risk Assessment Process
SCADA/ICS Risk Assessment Process includes three (3) stages;
1. Asset Identification and System Characterization
2. Vulnerability Identification and Threat Modelling
3. Risk Calculation and Management
We can then break down each of these stages into separate steps;
Stage #1 Asset Identification and Characterization
Step #1 Define Business/Operation Objectives
Step #2 System Characterization/Classification
Step #3 Asset Identification
Step #4 Network Topology and Data Flow Review
Step #5 Risk Pre-screening
Stage #2 vulnerability Identification and Threat Modelling
Step #6 Security Policy Review
Step #7 Controls Analysis
Step #8 Cuber Vulnerability Assessment
Step #9 Threat Assessment
Ste #10 Attack Vector Assessment
Step #11 Attack Tree/Risk Scenario Creation
Step #12 Validate Findings
Stage #3 Risk calculation and Management
Step #13 Calculate Risk
Step #14 Prioritize and Deploy Mitigation
Step #15 Validate Mitigation
Although many senior level cyber security professionals are capable of conducting a risk assessment, it is recommended that these individuals have SCADA/ICS experience as the standard tools in the cyber security arena are generally woefully inadequate in the SCADA/ICS arena. In addition, some of these tools can actually have adverse affects on SCADA/ICS systems.
SCADA/ICS Risk Assessment Methods
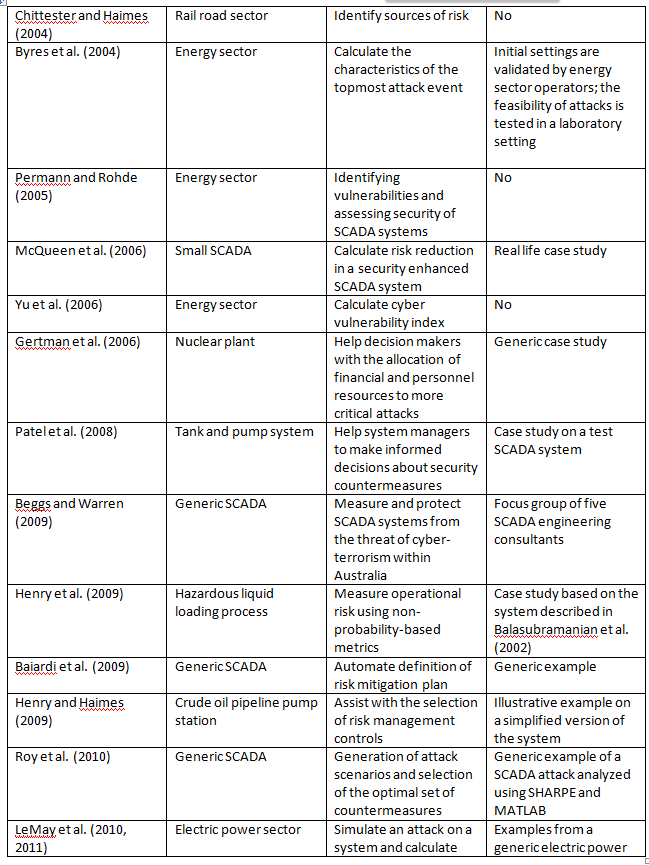
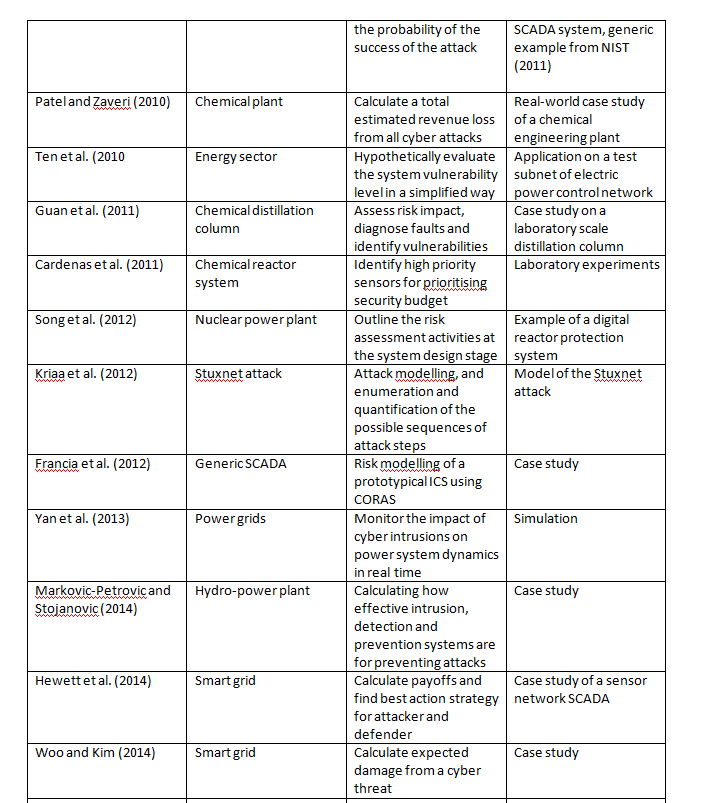
Over the years, a number of researchers have developed methods of risk assessment. The following list is meant to be a summary of the most prominent research. Note that not all these methods apply to every SCADA/ICS environment (check the sector column) and not all of them have been evaluated in live environments.
Authors and Year / Sector / Goal Evaluation / Method
Risk Management Protocols/Standards/Frameworks
In addition to methods listed above, there are a number of risk assessment protocols, standards and frameworks available to managers in this industry. These often incorporate the methods and methodologies of the research listed above, but not always.
The most prominent of these include;
(1) NIST 800-82
This document, first published in 2008, recommends that “established” security and vulnerability testing methodologies be adapted to SCADA/ICS. NIST notes and cautions that these established security and vulnerability tests may cause failure in a more fragile ICS environments.
(2) North American Electrical Reliability Council (NERC)
Published its “Vulnerability and Risk Assessment” in 2002 and has not been updated. They have also published a number of Critical Infrastructure Protection (CIP) standards. These standards only require that entities, “identify and document a risk-based assessment methodology”. This structure leaves a lot of wiggle room by managers to avoid negative reports and leave facilities still vulnerable.
(3) Cyber Security Evaluation Tool or CSET
This tool, developed by the U.S. DHS, is available for free. It is used to SCADA/ICS security assessments against industry standards. DHS describes their tool as “a desktop software tool that guides users through a step-by- step process to assess their control system and information technology network security practices against recognized industry standards”
Look for my upcoming tutorial on CSET here on Hackers-Arise.
(4) INL National SCADA Test Bed Program (NSTB)
This program is intended to share information among stakeholders in the industry obtained through risk assessments. Keeping in mind that much of that information is business sensitive, INL works with the industry partners to determine which information is disclosed. Although this is necessary to garner cooperation, it is also a weakness of the program.
(5) Ideal-Based Risk Assessment and Metrics
This method is unique in that it works from an “ideal state” and works backward to determine how far the target is from this ideal state of security. This approach is useful in an environment, like SCADA/ICS, where little data exists to assess the probabilities of a breach. The drawback to this system is its complexity and its subjectivity of risk scoring against an ideal system.
Conclusion
Risk assessment is key first step in securing a SCADA/ICS site from a security breach. Unfortunately, risk assessment in such an environment is fraught with perils including the heterogeneity of the industry and protocols, a lack of good data on breaches and the difficulty of assessing the consequences of such a breach. Despite these hurdles, we must still be willing to periodically objectively assess the risk of these far too vulnerable and yet critical facilities, if we are to have any success in making them more secure.
In my next tutorial in this series, we will examining one of these Risk Assessment Guidelines/Tools, the U.S. Homeland Security’s CSET risk assessment framework.