Welcome back, my aspiring cyberwarriors!
If the hacker can obtain or crack the target’s password, in many cases, this can lead to complete account compromise and takeover. Many people use simple passwords that are relatively easy to crack with a good word list. From our examination and analysis of data dumps on the dark web, about 10% of people use one of the top 10,000 passwords, and about 30% use one of the top 1,000,000 passwords. When attempting to crack the target’s password, make certain to try these first before engaging in the long tedious process of brute force password cracking. We have compiled the 10,000 most common passwords and the 1,000,000 most common passwords from dumps on the dark web and made them available to you here.
In many cases, people use words and numbers that are familiar to them. Remember, the targets likely have multiple passwords and need to change them frequently. This makes it very difficult to remember. As a result, they try to use familiar words and numbers such as their child’s name and birth date, spouse’s name and wedding anniversary, etc. Admit it, you’ve probably done this! If we can gather this information about the target using good OSINT, we may be able to create a custom, potential password list that could save us hours, days, or weeks from using a brute-force attack on their password.
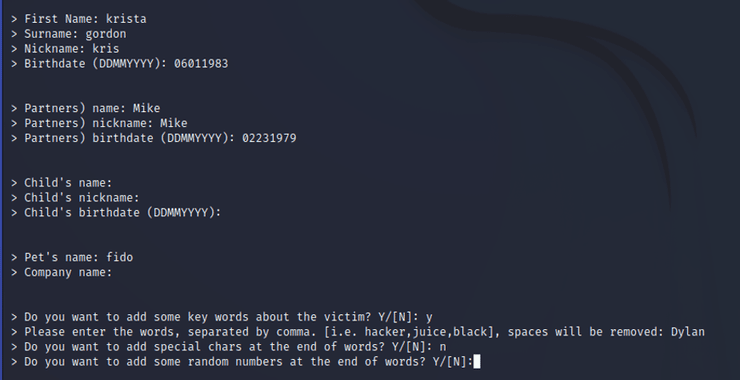
We have a special tool that can create tailored password lists based upon some key info on the target. It’s called cupp or Common User Password Profiler.
Step #1: Download and Install cupp
Cupp is not built into Kali, so you will need to download it from github.com.
kali > git clone https://github.com/Mebus/cupp

To run cupp’s help screen, we simply need to enter;
kali > ./cupp.py

kali > ./cupp -i


When cupp has completed its task, it places all the potential passwords (5832 in this case) in a file named Krista.txt. We can view the contents of that file by entering;
kali > cat krista.txt

And then variations on her favorite musician’s name (Dylan)…

…and then variations on her name.
There is a VERY good chance that the target’s password is among this custom-made password list.
Summary
Password cracking is the art and science of finding the target’s password. If you do, you can likely take complete control of the target and probably their life!
Rather than proceeding immediately to the time-consuming and tedious brute-force password cracking first, try the most commonly used passwords. Our analysis indicates that about 35% of passwords are in the 1 million most used passwords. If this fails, try developing a custom password list using cupp from the information you can glean from some well-honed OSINT skills.