I. Introduction
This section of this course is designed to help you find and use exploits that will work against known vulnerabilities. As you already know, there is no “silver bullet” exploit that works against all systems, under all circumstances. Exploits are very specific. They work ONLY under very specific circumstances. In many cases, they are only effective against a specific operating system, with a specific application, with a specific port open and sometimes, even in a specific language. That is why the reconnaissance work with did the earlier modules is so important. Without that information, we are literally taking a “shot in the dark” and are very unlikely to be successful.
When we know of a vulnerability in the target system, the next step is to find an exploit that takes advantage of it. There are many vulnerabilities that don’t necessarily have an exploit for it or at least a known public exploit. In this module, we are focused on finding those exploits and then how to adapt and use them. In Lesson #1 of this module, we used www.securityfocus.com to identify a vulnerability AND an exploit for Adobe’s Flash Player. In this Lesson, we will use Offensive Security’s “Exploit DB” to find exploits against a particular vulnerability.
II. Exploit DB
Exploit DB is a website that is managed by the folks at Offensive Security, the same folks who developed BackTrack and Kali. You can get to Exploit DB by navigating to www.exploit-db.com as seen below.

Exploit-DB categorizes exploits into these categories;
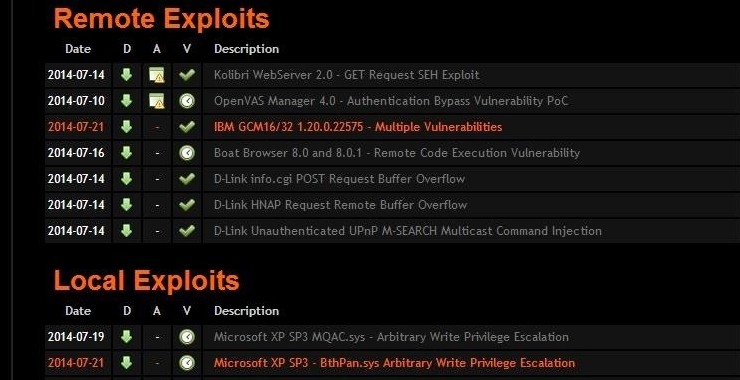
(1) Remote Exploits
(2) Web application exploits
(3) Local and privilege escalation Exploits
(4) PoC (Proof of Concept) and Denial of Service Exploits
(5) Exploit and Shellcode Archive
(6) Archived Security Papers.

If we want to search for a specific exploit, rather than simply view newly developed exploits, Exploit-DB has a “Search” function. In this case, we will be looking for some Web Application exploits, so click on Web Applications and then Click on Search near the upper Right Menu bar and it will bring up a screen like below. In this case. let’s look for Exploits that apply to the popular open source Content Management system (CMS) Joomla. Type “Joomla” into the Free Text Search box and click on search.
When you do so, Exploit-DB will return all the Exploits with Joomla as its target as seen below.

Note that there are over 1000 entries in the Exploit-DB database of Joomla exploits. Also, note that if you have a specific name for the exploit you can enter it in the “Title” window or if you have the CVE number, Exploit-DB is able to find the exploit that applies to that particular CVE. Also, note that many of the Joomla exploit are of the SQL Injection variety which is not surprising.
Let’s take a look at one of those exploits. Let’s click on the second one listed the “Joomla! Component J2Store < 3.3.7 – SQL Injection”. When we do so, you can see the exploit below.

As we can see, the author describes the exploit in the upper circled text and then provides us with the SQL code in the lower circled text that takes advantage of this vulnerability in Joomla.

III. Exploit-DB Advanced Search
In addition to regular search, exploit-db has “Advanced Search” capabilities. Click on the “Advanced ” word next to the search button and it opens a screen like that below. When do this, in addition to the “Title”, “Free Text Search” and “CVE” fields to search for, we have “Author”, “Platform”, “Type”, “Port” and OSVDB fields to search by. Although it may not seem intuititive, exploits written for the Metasploit Framework are usually categorized by author as “metasploit”. When we type in metasploit into the author field, Exploit-DB returns for us all the exploits that can be used with our Metasploit framework, making their use much simpler (we will be doing a module on the Metasploit Framwork in Module 9).
When we click on “Search”, exploit-db returns to us all the exploits written for Metasploit, over 1300. Any of these can be easily plugged in to Metasploit for exploiting the targeted system.

Finally, we can combine these two searches to find exploits that work in Metasploit against Joomla by typing Joomla in the Free Text window and Metasploit under author and Exploit-db returns for us five (5) exploits purposely written to exploit Joomla that can be used in the Metasploit Framwork as seen below.

IV. Exploit-DB in Kali
Exploit-DB is also built into Kali so there is no need necessarily to go to the website to find exploits. From the GUI, go to Applications –> Kali Linux –>Exploitation Tools –> Exploit Database –> searchsploit or open a command prompt and type “searchsploit”
This opens an application that enables us to search the exploit-db on our desktop as seen in the screenshot below.

This screen explains nearly everything we need to know about using searchploit. The syntax is fairly simple and intuitive, we simply use the term searchsploit followed by one or more terms to search for. Unfortunately, unlike the website, it does not have the capability to specifically search by author, CVE, platform, etc., but if you put those items within the search string, in most cases it will pick up the exploit you are looking for.
Let’s try to do the same search we did above within the website using searchsploit to find Joomla exploits for the Metasploit Framework. Let’s first search for simply “Joomla”.
kali > searchsploit joomla

As you can see, Joomla returned hundreds of exploits. Now, if we add the search term Metasploit to our search, so we are looking for Joomla exploits with the author “Metasploit” as we did above, searchsploit returns no results.
kali > searchsploit metasploit joomla

Finally, let’s try to find the same exploit we found above using the Exploit-DB website by using additional keywords. In this case, since that exploit is named ” “, let’s try adding the keyword to the “spider” to our search.
kali > searchsploit joomla spider

Searchsploit returned eleven (11) results when we added the term “spider” to our search, but none of the exploits appears to be the exploit we are looking for.
V. Conclusion
Exploit-DB is an excellent repository of known exploits. The web interface has powerful search functionality built in that enables us to narrow down our search for exploits by many different criteria. The advanced search is especially powerful enabling us to search by author, port, platform, etc. The searchsploit command in Kali Linux is convenient, but not nearly as powerful as the search function on the Exploit-DB website.