Welcome back, my aspiring SCADA Hackers!
The recent ransomware attack against the Colonial Pipeline in the US reminds us that SCADA/ICS infrastructure is NOT immune from ransomware attacks. In fact, this attack should remind us just how vulnerable industrial systems are to cyber-attacks and the potential ramifications of such attacks. Remember, with SCADA/ICS systems you are protecting the process. The process is far more important than the data and ransomware is very effective at disrupting the process.

Most ransomware to date has been targeted to traditional IT systems. In addition, earlier ransomware attacks took a shotgun approach to targets, in other words, send out thousands or millions of attack vectors and hope that a few are successful. In the last year, those of us employed protecting industrial systems have something new to worry about, a ransomware variant designed specifically for SCADA/ICS systems and targeted specifically to a single target!
Enter SNAKE (EKANS)
In January 2020, a new ransomware malware was found in the wild by the MlawareHunterTeam and sent to Vitali Kremenz to reverse-engineer. It was written Google’s coding language, Golang, an increasingly popular language for ransomware developers (probably because it provides for cross-platform development). This ransomware was quickly given the moniker, Snake, for the strings found among the code (it appends .EKANS to the file strings it encrypts).
This ransomware targets industrial systems specifically by;
Targeting a specific domain or IP address
Targeting specific industrial processes
Like other ransomware, it encrypts critical files, but first, it kills the industrial processes and then encrypts. In this way, not only are the files unavailable to the target, but the industrial processes are stopped and can’t be re-started without the decryption key. Finally, the attackers demand a ransom in millions of dollars rather than hundreds of dollars like the typical ransomware so prevalent throughout the world.
Anatomy of Snake
Snake is tailored to each industrial target, so each one is slightly different. In this case, we will examine a variant of Snake that was used to bring down the industrial operations of Honda, the Japanese auto manufacturer. On June 8, 2020, Snake brought Honda’s operation in Japan and Europe to a screeching halt.
Because Snake is tailored specifically to the target, it can’t be said what its particular attack vector is. The attackers use a multitude of vectors to enter the system including;
Known vulnerabilities
Stolen Credentials
Weak or misconfigured RDP
In the case of the Honda attack, the attack vector was likely through RDP. Other attacks may involve the typical ransomware vectors such as phishing and malicious documents. Furthermore, in some cases, Snake has exfiltrated data before the encryption process begins.
Let’s take a look at how Snake does its dirty work.
Stage 1
To begin, the Snake’s executables are just 3-4MB in size, written in GO, and are 32-bit and unsigned. When the executable is executed on the target, the first thing it does is to make certain that it is the only being run once by using a mutex named “EKANS”.
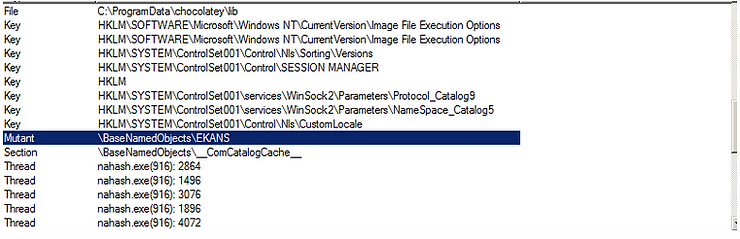
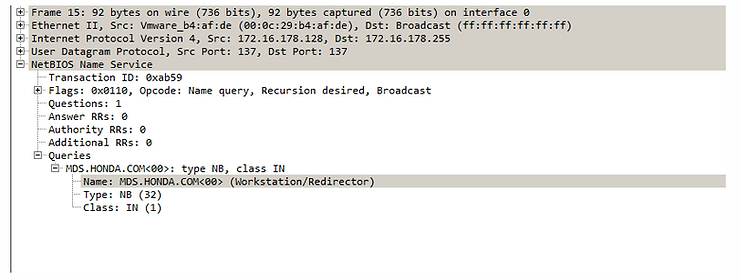
Next, it tries to verify that it is in the proper target’s network by using DNS and NETBIOS. If the name resolution is unsuccessful, the malware simply exits without encryption. The specificity of the attack is also reflected by the IP address of Honda appearing in computer’s RAM.
Stage 2
Before Snake begins encryption, the malware uses the Windows firewall to block any incoming or outgoing network connections using the netsh command. Now with the outside world cutoff, it kills any hard-coded processes that might interfere with the encryption stag
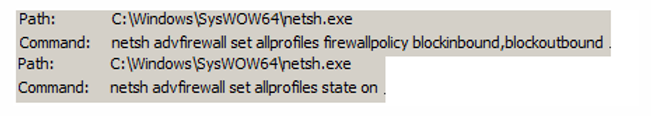
Stage 3
Snake has a hard-coded list of potential industrial processes such as GE Proficy, GE Fanuc, Honeywell’s HMI, Flexnet, and others. It looks for these processes and if they exist, it stops them. It’s important to note that Snake does NOT have the capability of injecting commands into these processes which would be far more malicious and could have devastating consequences. I would not be surprised if we see that capability or module added in future variants of Snake.
Snake also removes the computer’s Shadow Volume Copies and kills processes related to virtual machines (VMWare Tools), and remote management tools and software.
Stage 4
Once all this preparation is completed, Snake begins encryption. Snake uses AES-256 and RSA-2048. Snake uses the symmetric key for encrypting and decrypting and the key is encrypted with the attacker’s public key. The encryption process excludes all critical system files and folders so that the system can be used to pay the ransom. Like nearly all other ransomware, it contains a hard-coded list of file extensions to encrypt such sql, doc., xls, accdb, etc. The encrypted files’ strings are all appended with five characters (.EKANS).
Stage 5
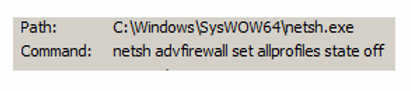
Once all the files are encrypted, Snake once again uses the netsh command to disable the firewall.
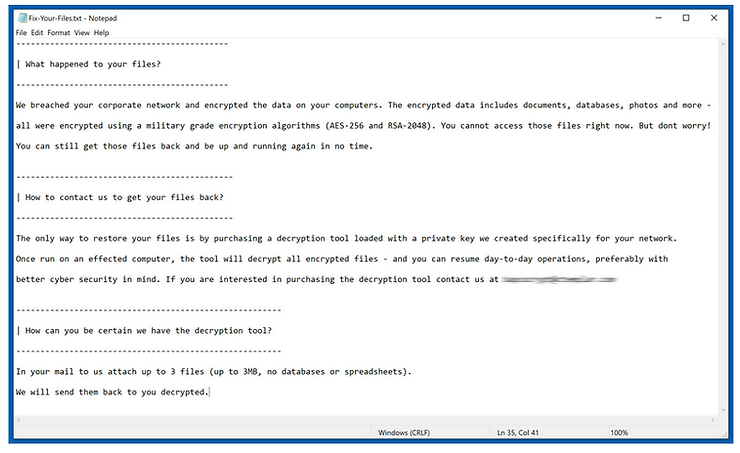
Finally, the ransom note is presented to the target.
Summary
While ransomware has become the scourge of our digital systems, a new variant threatens SCADA/ICS systems and infrastructure. Snake is ransomware that specifically targets industrial systems and if successfully infecting an organization can kill industrial processes that can only be re-started by paying the ransom and decrypting the files.
For more on SCADA Hacking and Security, click here