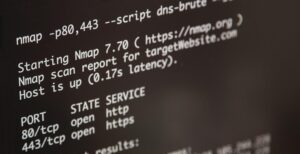
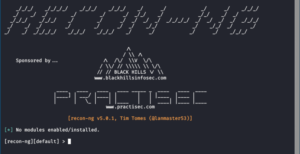
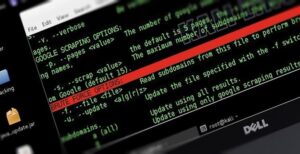
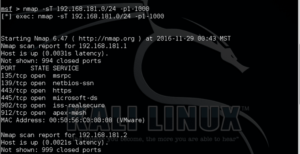
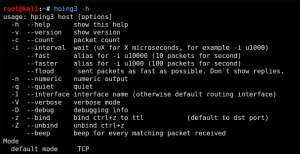
Although every hacker is looking forward to pwning the system, reconnaissance may be the most important part of the hacking process. In many cases, reconnaissance can consume 70-80% of the time of the hacking process. Without good reconnaissance, your hacking attempts are likely to be for naught.
Exploits are very specific to the technology being utilized. This can include the operating system (OS), the applications being run, the ports and services, and even the language of the system. We must gather all that information and sometimes even more before we select the right approach to exploit the system.
In this section, I will show you numerous ways to gather information on the target. Some of these include;
Learn more in the courses: