Finding the F5 Systems Vulnerable to CVE-2020-5902 using Shodan
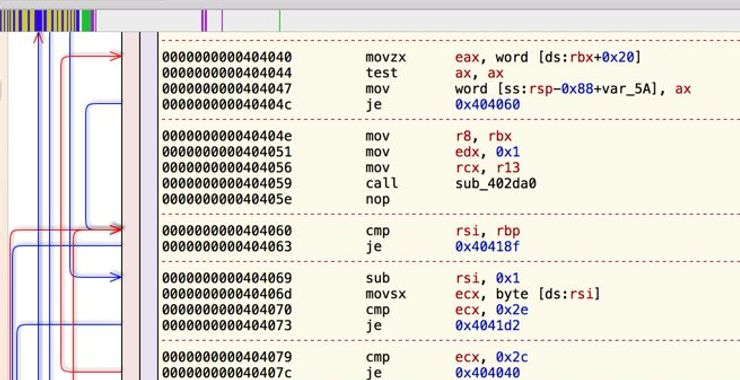
Welcome back, my aspiring cyberwarriors! On July 4, 2020 (US Independence Day), F5 released a security patch for their BIG-IP systems that allows the attacker to take control of the affected systems. This vulnerability is rated a 10/10 in severity and assigned CVE-2020-5902. This vulnerability is so severe that an attacker with even rudimentary skills […]
Continue Reading