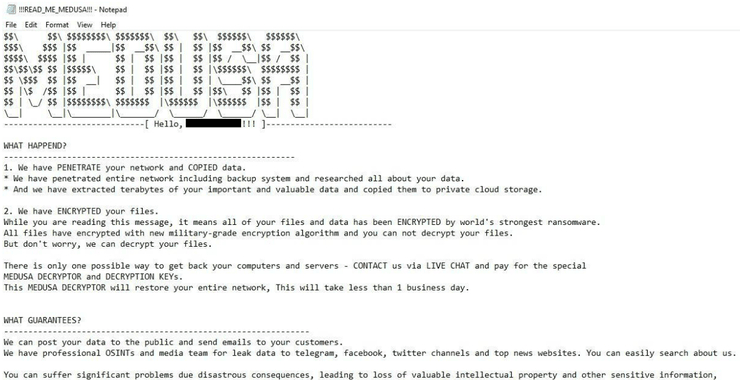
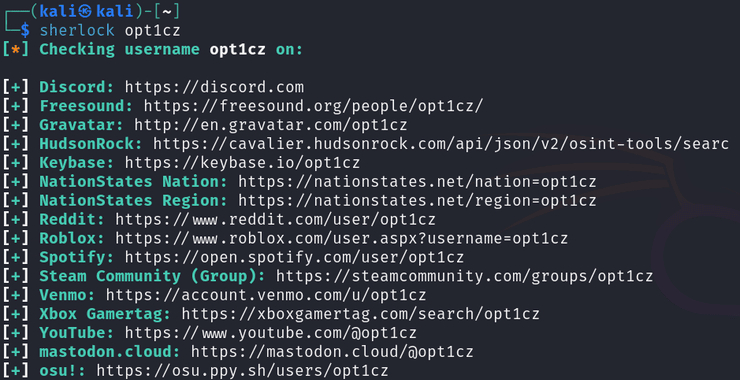
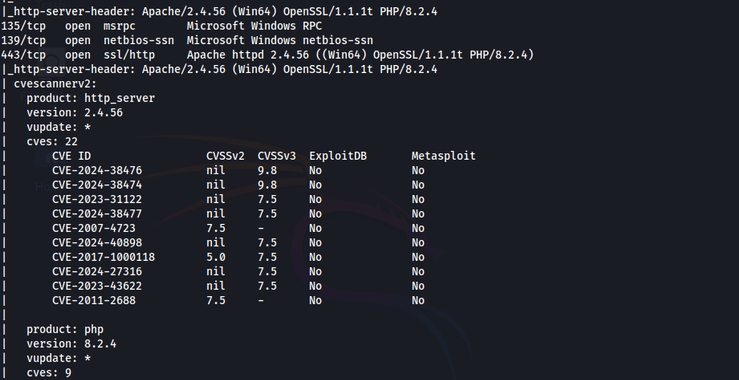
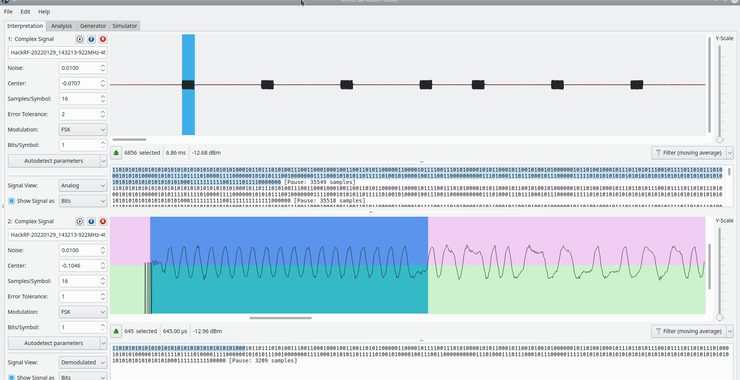
The Medusa Ransomware Threat: Anatomy of a Cybercrime Operation
Welcome back, aspiring cyberwarriors! In Greek mythology, Medusa was once a beautiful woman until Athena’s curse transformed her into a winged creature with a head full of snakes. She is seen as both a monster and a protector, possessing the power to turn anyone who gazes upon her face to stone. Ransomware groups often adopt […]
Continue Reading