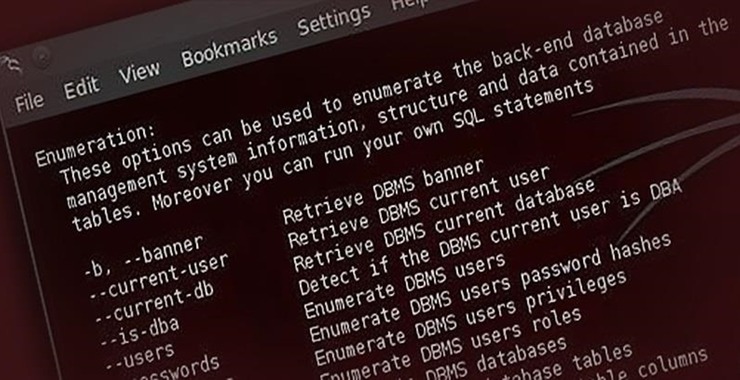
Database Hacking, Part 4: Extracting Data with sqlmap
Welcome back, my aspiring White Hat Hackers! In my previous tutorials in this series, I taught you the basics of SQL injection (the most common method of hacking online databases) and then how to use it against a MySQL database. In this tutorial, we will look at how to now extract the key data from […]
Continue Reading