Mr. Robot Hacks, Season 3 E.9: How Elliot Traces the Dark Army
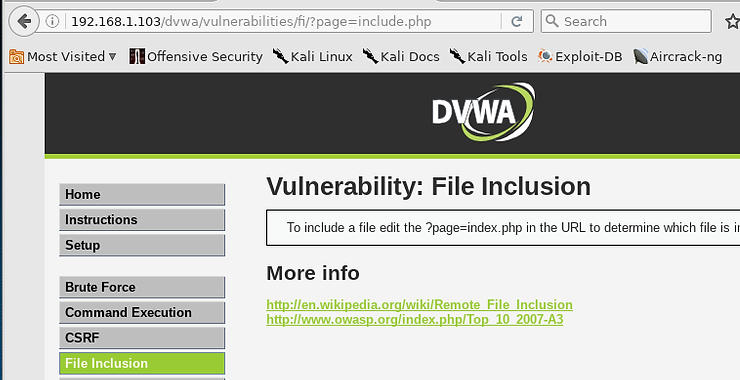
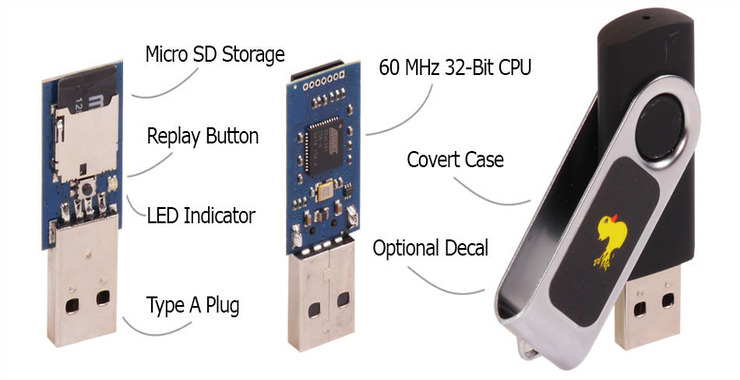
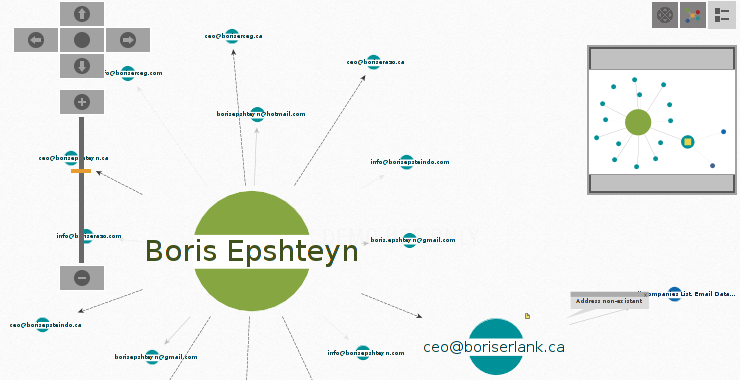
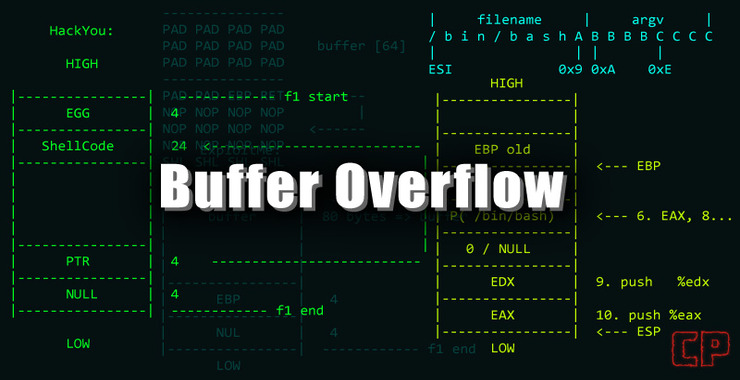
As Mr Robot races to the conclusion of Season 3, Elliot is determined to stop the Dark Army from doing any more damage. The Dark Army, led by White Rose, has blown up 71 buildings. As you remember, Elliot’s system has been compromised and he wants to trace the malware back to its source and […]
Continue Reading