OSINT: Google Hacking and Dorks to Find Key Information
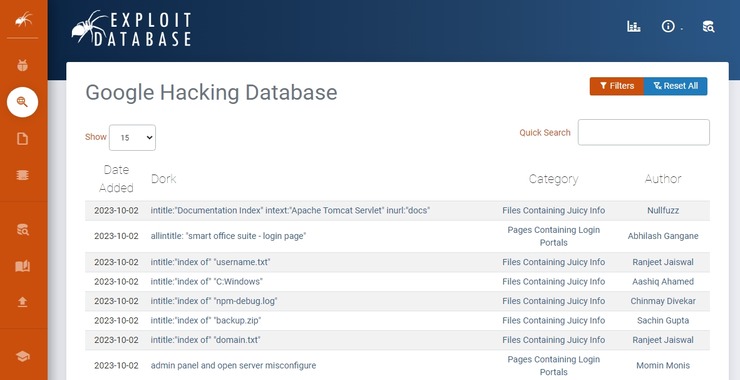
As all of us know, Google operates the most widely used Internet search engine on the planet. Google crawls nearly every web page, of every website, and builds a massive database of all the information it gathers. Most people then use Google’s database to search by keywords for articles relevant to the subject of their […]
Continue Reading