MiTM Attack with Ettercap
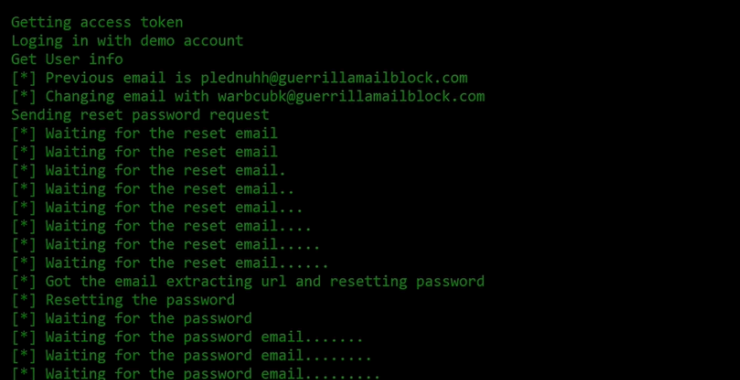
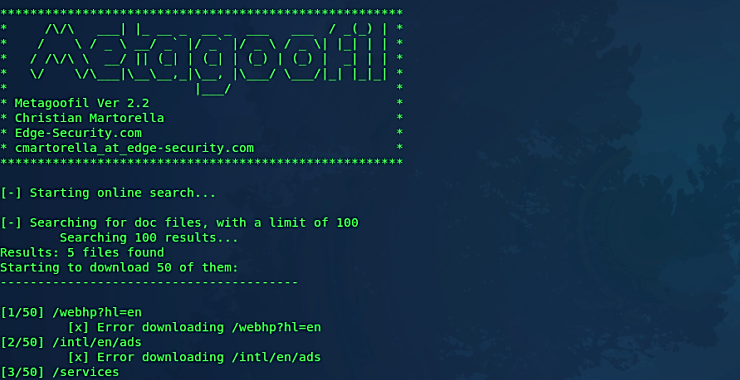
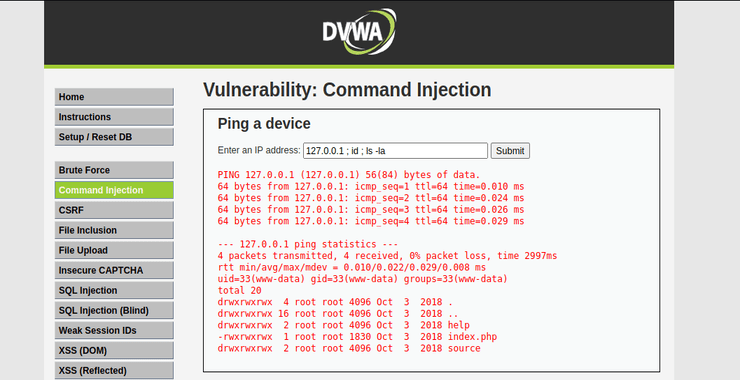
Welcome back, my rookie cyber warriors! Man-in-the-Middle attacks can be among the most productive and nefarious attacks. If the attacker/hacker can place themselves between two systems (usually client and server) they can control the flow of traffic between the two systems. In this way they can eavesdrop on the traffic, delete the traffic, inject malware […]
Continue Reading