Network Forensics, Part 2: Detecting and Analyzing a SCADA DoS Attack
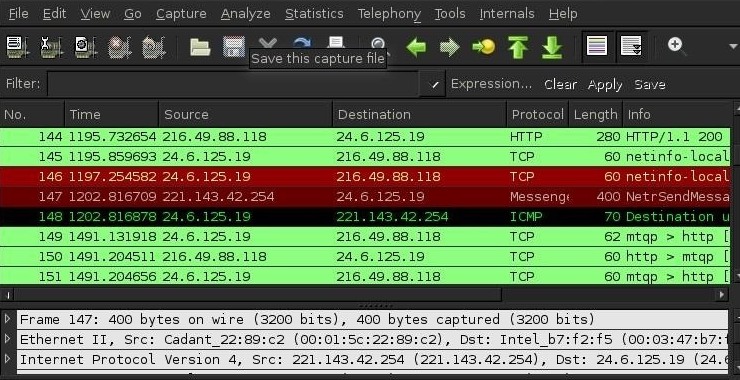
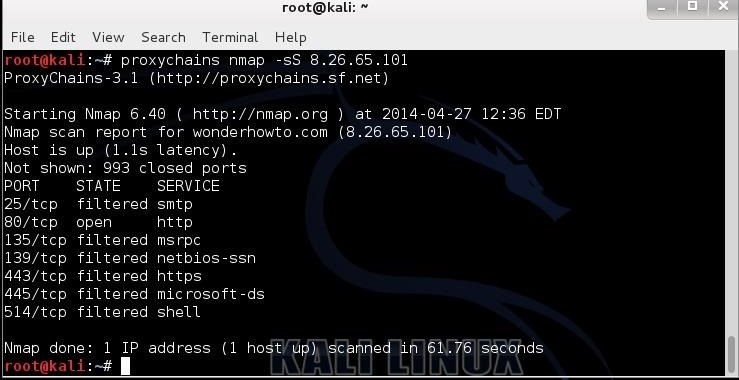
Welcome back, my aspiring network forensic investigators! Now that you have a basic understanding of Wireshark and have conducted an analysis of a malware attack using Wireshark, let’s expand our purview of network attacks to that critical but often overlooked area of IT security, SCADA/ICS security. Unlike most attacks on IT security, attacks on SCADA/ICS […]
Continue Reading