Open-Source Intelligence (OSINT): Unmasking YouTube with OSINT Tools!
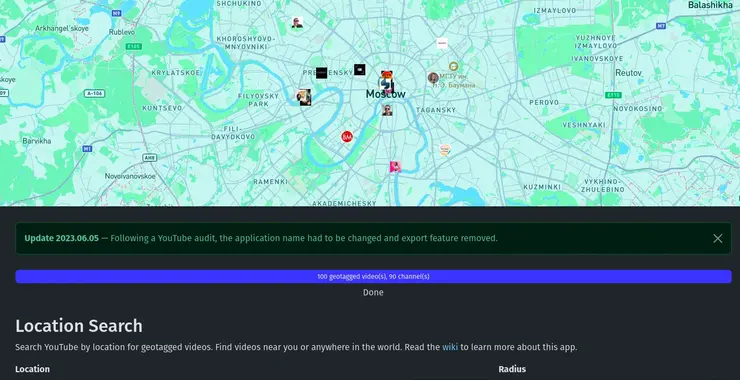
Welcome back, aspiring cyberwarriors! In our digital investigations, we often need to extract valuable intelligence from video content. This might include identifying locations, uncovering connections between individuals, finding deleted content, or simply gathering information that someone has inadvertently shared on camera. It is critical that we know how to effectively search through the massive repository […]
Continue Reading