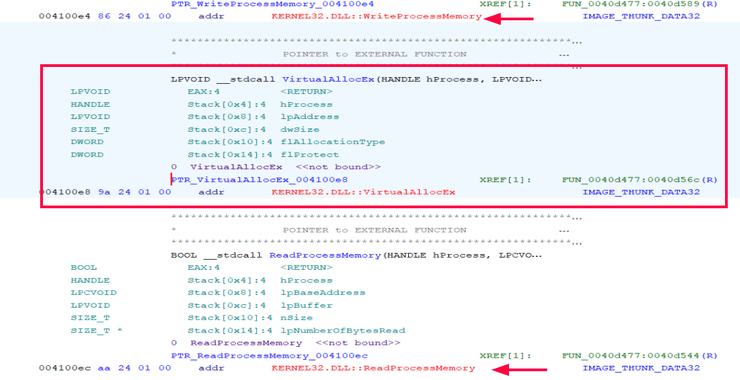
Malware Analysis: Process Injection in the REMCOS RAT
Process injection is one of those stealthy techniques malware loves to use to stay under the radar. By injecting malicious code into legitimate processes, attackers can hide in plain sight, making detection a real challenge. In this post, I’ll walk you through an actual malware sample that uses process injection, breaking down how it works. […]
Continue Reading