Database Hacking: SQLite Essentials and Attack Strategies
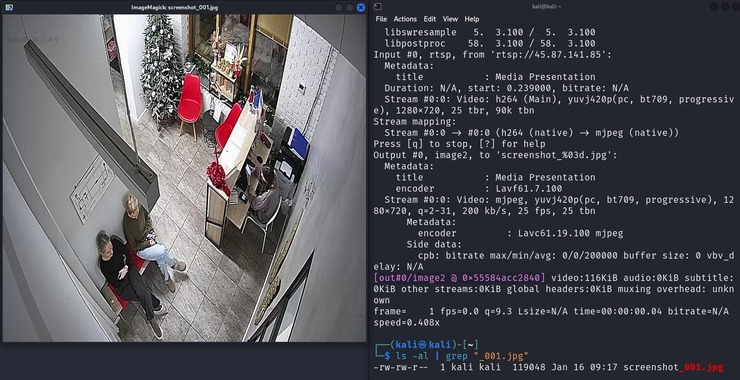
Welcome back, aspiring cyberwarriors! SQLite is one of the most commonly used database engines, embedded in countless applications, mobile devices, and web services. Its compact design makes it a popular choice for developers, but it’s also an attractive target for hackers. Whether you’re a penetration tester, cyberwarrior, or security researcher, mastering SQLite can open […]
Continue Reading