Linux Basics for Hackers: Building a Router with nftables
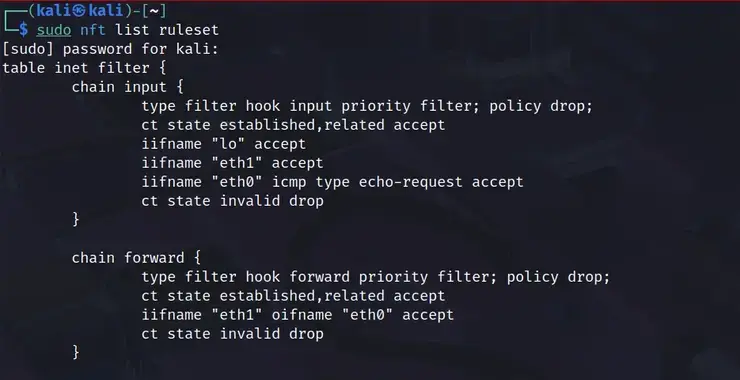
Welcome back, aspiring cyberwarriors! As you know, traditional hardware routers can be expensive, inflexible, and often come with proprietary firmware that limits your control. By leveraging the power of Linux and nftables, you can create a customized routing solution that gives you complete control over your network traffic, security policies, and performance optimizations. Nftables represents […]
Continue Reading