Web App Hacking: XXE Vulnerabilities and Attacks
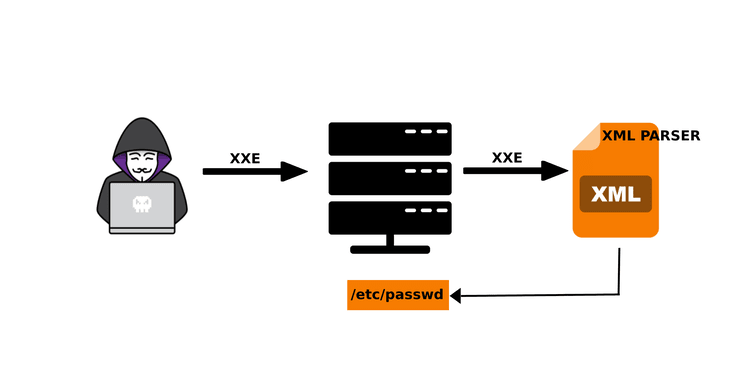
Welcome back, my aspiring Web App cyberwarriors! Among the most important types of web app attacks is the XXE attack. This is the XML eXternal Entity Injection attack. This type of vulnerability allows an attacker to interfere with the app’s processing of XML data. Many applications use the XML format to transmit data between the […]
Continue Reading