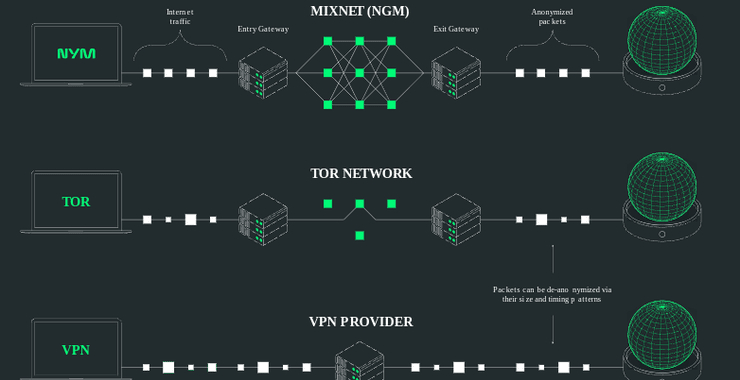
NymVPN Setup & Testing: A Hands-On Walkthrough
Welcome back, aspiring cyberwarriors! In recent years, VPN’s have been marketed as a sure-fire way to keep your safe from hackers.Unfortunately, that has been shown to be in-arguably false with dozens of vulnerabilities found in all the major VPN developers. See our article here on the major recent vulnerabilities found in these devices, many […]
Continue Reading