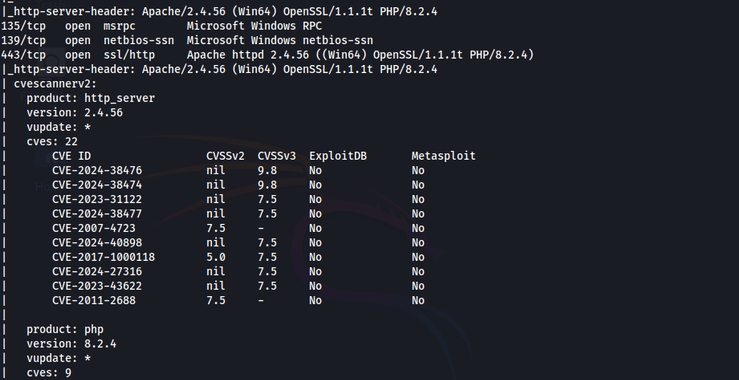
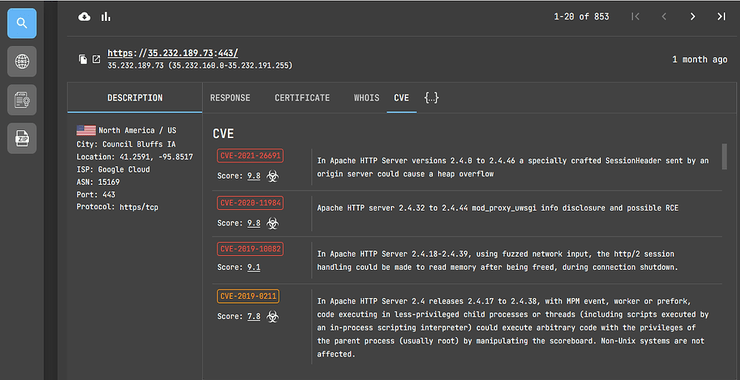
Vulnerability Scanning: Automatic Search For Known CVEs With CVEScannerV2
Welcome back, aspiring cyberwarriors! During reconnaissance, our goal is to identify vulnerable services within our target’s network. To streamline this process, CVEScannerV2 was developed – a powerful Nmap script that bridges the gap between network scanning and vulnerability assessment. This tool enhances the capabilities of the widely-used Nmap scanner, offering security professionals a comprehensive […]
Continue Reading